Even the most trusted healthcare providers aren’t immune to cyberattacks. One such victim was “Change Healthcare”, a major company in the healthcare industry, providing essential services such as data analytics, payment processing, and software for healthcare systems. Founded to streamline healthcare services and improve efficiency, the company helps millions of Americans receive their care seamlessly.
In March 2023, Change Healthcare found itself as a victim for a complicated cyberattack that shook its operations and the trust of customers. In this blog, let’s talk about the details of the attack, its aftermath, and the lessons we can learn to strengthen our security posture. Incidents like these require you to have a reliable vulnerability management tool.
Who Attacked Change Healthcare?
The cyberattack on Change Healthcare was orchestrated by a well-known group in the cyber-crime world called “BlackCat”. BlackCat is a ransomware gang for targeting large corporations, particularly those that store sensitive information. The healthcare industry, that is already burdened by a vast number of patients’ data, makes it an attractive target.
But why Change Healthcare?
It’s simple, healthcare enterprises store large amounts of sensitive data, such as medical records, insurance details, and payment information. If this data gets into the wrong hands, it leads to identity theft, fraud, and other crimes. Also, healthcare systems can’t afford to be shut down for long, and attackers assume they’ll pay ransom as soon as possible to resume operations. Moreover, Change Healthcare is a leading healthcare claims processing provider, processing 15 billion claims annually in North America.
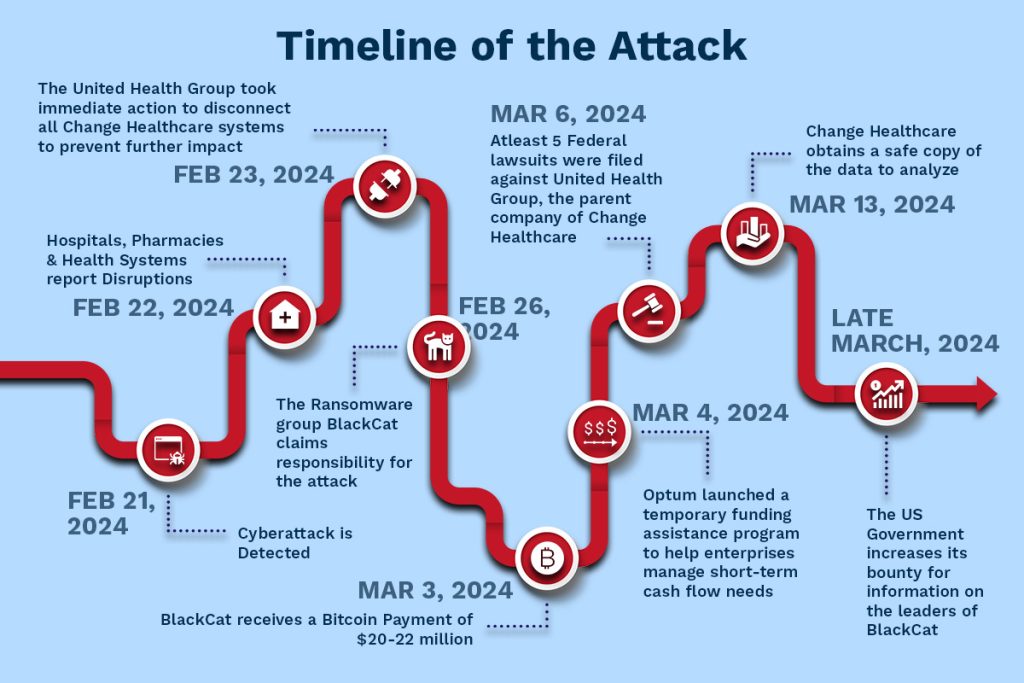
Timeline of the Attack
- February 21, 2024: Cyberattack is detected.
- February 22, 2024: Hospitals, pharmacies, and health systems report disruptions.
- February 23, 2024: The United Health Group took immediate action to disconnect all Change Healthcare systems to prevent further impact.
- February 26, 2024: The ransomware group BlackCat claims responsibility for the attack.
- March 3, 2024: BlackCat receives a Bitcoin payment of $20-22 million.
- March 4, 2024: Optum launched a temporary funding assistance program to help enterprises manage short-term cash flow needs.
- March 6, 2024: At least five federal lawsuits were filed against United Health Group, the parent company of Change Healthcare.
- March 13, 2024: Change Healthcare obtains a safe copy of the data to analyze.
- Late March 2024: The US government increases its bounty for information on the leaders of BlackCat.
Collateral Damage Caused by the Attack
The impact of the cyberattack on Change Healthcare was vast and severe. When millions of people rely on a service and it gets compromised, the results are severe.
- Financial strain: The attack caused severe financial strain on healthcare providers, with many reporting cash flow problems. 80% of physician practices lost revenue from unpaid claims, and 78% lost revenue from claims they were unable to submit.
- Delayed patent care: The attack caused delays in patient care and reimbursement, which jeopardized the survival of many healthcare providers.
- Leaked sensitive information: An estimated third of American’s had their sensitive health information leaked to the dark web.
- Credit damage: The attack could damage the credit of smaller providers, who may already have worse credit ratings and could struggle with cash flow disruptions.

This breach didn’t just shake the company. It highlighted how vulnerable the healthcare industry is to cyberattacks and just how many people can be caught in the crossfire when something goes wrong.
How to Avoid Such Attacks?
Change Healthcare’s experience serves as a cautionary tale, and here are the most critical lessons:
- Multi-Factor Authentication: MFA is one of the easiest and most effective ways to prevent unauthorized access. Even if hackers manage to steal a password, an additional layer can stop them then and there.
- Ransomware Defense: Ransomware is a beast, but it can be fought. Regular backups and storing them offline is a key strategy. If attackers hold your current data hostage, you can restore the most recent backup and minimize damage.
- Employee Awareness Training: Many cyberattacks are successful because of simple mistakes, like clicking on a phishing email. Regular training for employees on how to recognize suspicious
emails or websites is a must.
The SanerNow Approach to Prevent Cyberattacks
SanerNow Continuous Vulnerability and Exposure Management solution could have saved Change Healthcare.
- See Everything: Manage vulnerabilities, exposures, and other security risks in a single unified dashboard. It offers a centralized console where you can access information about your IT, track progress and communicate with other teams effectively.
- Asset Exposure: Gain continuous visibility and control over your IT asset infrastructure. Have a comprehensive understanding of the enterprise IT infrastructure that also helps to collaborate and remediate vulnerabilities and exposures.
- Prioritization of Risks: SanerNow’s Risk Prioritization is the world’s first integrated, effective, and rapid risk prioritization based on CISA’s SSVC framework. The vulnerabilities can be prioritized into Act, Attend, Track and Track*. Prioritize vulnerabilities based on their potential impact on the organization’s operations and security.
- Real time visibility: Access real-time visibility into the organization’s security posture and IT infrastructure. Access up-to-date information about the security vulnerabilities, asset inventory, patch status, and compliance posture, enabling you to make informed decisions together.
- Customizable Reports: Create customized reports tailored to your specific requirements. These reports provide insights into key metrics and KPIs, clearing the way for communication between you and your CISO.
- Integrated Patch Management: Collaborate on patching risks with integrated patch management solution. Both security and IT teams can collaborate and ensure the vulnerabilities are detected and patched immediately or schedule patches during off hours to ensure the company’s business is not disrupted.
- Meet Compliant Standards: Automate and streamline compliance management with SanerNow. Ensure the companies compliance standards are up to date by regulating their IT devices with HIPAA, PCI, ISO, NIST CSF, and STIG compliance benchmarks. Also, detect non-compliant systems by identifying faulty system configurations with a fast compliance scan.
Conclusion
The Change Healthcare cyberattack serves as a reminder that no industry is immune to the threats of the digital systems, especially one as critical as healthcare. The lessons learnt definitely helps prevent future incidents. However, SanerNow provides a proactive approach towards vulnerability remediation and helps businesses stay two steps ahead of groups like BlackCat. In the end, proactive cybersecurity isn’t just a precaution, it’s a necessity in today’s threat landscape.


