2024 is finally coming to a close, and what better way to wrap it up than with a Microsoft Patch Tuesday?
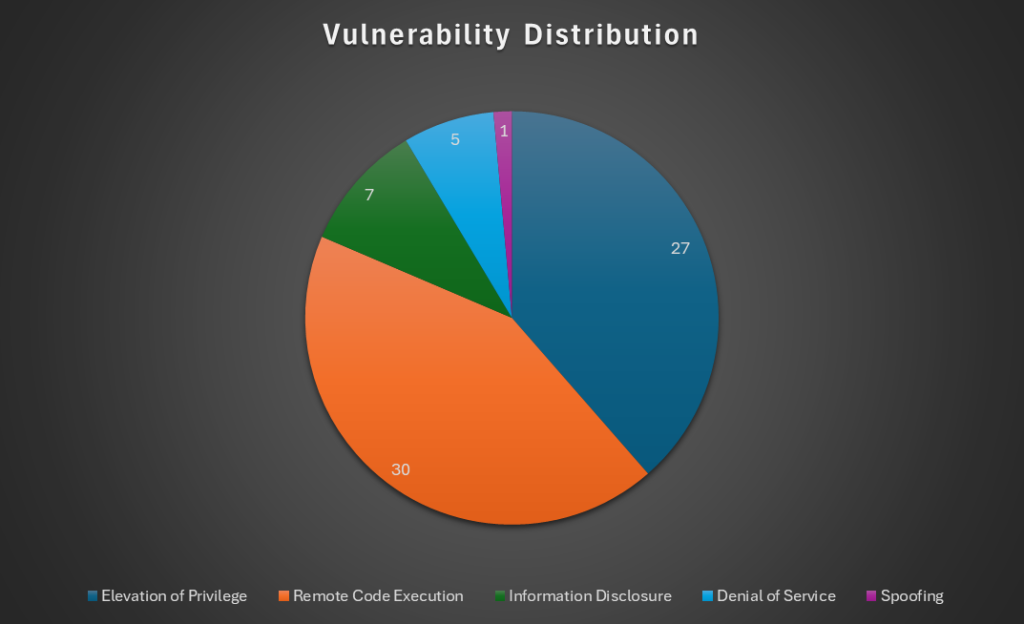
The final Patch Tuesday of the year brings us 71 fixes, one zero-day, and 16 critical flaws. Thirty of the flaws found could result in Remote Code Execution. The following chart shows the number of vulnerabilities found in each category.
Zero Days
Though not much information on it is available, CVE-2024-49138 (in Windows Common Log File System (CLFS) Driver) is known to have been publicly disclosed and actively exploited. This mysterious vulnerability carries a CVSS score of 7.8 and allows an attacker to gain SYSTEM privileges by triggering a heap-based buffer overflow.
The method of exploitation has not been made public as of December 11th, 2024. However, we know that Windows CLFS Driver flaws have been exploited to spread ransomware multiple times, meaning we cannot take this flaw lightly.
Critical Flaws
Out of the 16 critical vulnerabilities patched, a few are particularly striking.
CVE-2024-49112, in Windows Lightweight Directory Access Protocol, allows an unauthenticated, remote attacker to execute arbitrary code with a set of crafted LDAP calls. This is the most severe of the 71 vulnerabilities found, with a CVSS score of 9.8. According to Microsoft, mitigating this vulnerability involves configuring domain controllers to either not access the internet or not allow inbound RPC from untrusted networks.
Windows Remote Desktop Services was found to house nine critical vulnerabilities, all leading to Remote Code Execution. CVE-2024-49106, CVE-2024-49108, CVE-2024-49115, CVE-2024-49116, CVE-2024-49119, CVE-2024-49120, CVE-2024-49123, CVE-2024-49128, and CVE-2024-49132 all have CVSS scores of 8.1 and require an attacker to win a race condition to create a user-after-free scenario.
Interestingly, these aren’t the only vulnerabilities found in Windows Remote Desktop Services. Microsoft also patched CVE-2024-49075 this month, which resulted in a Denial of Service. This flaw is of Important severity and has a CVSS score of 7.5.
There are also more race conditions to be found, albeit in other products. CVE-2024-49118 and CVE-2024-49122 (CVSS 8.1), present in Microsoft Message Queueing (MSMQ), also require attackers to win race conditions to trigger RCE. Exploitation involves sending a crafted MSMQ packet to an MSMQ server. CVE-2024-49118 is, according to Microsoft, not that likely to be exploited since the requisite race condition must be won while an infrequently recurring operation is being executed on the vulnerable system. This means that if the attacker fails once, they must wait for a considerable amount of time before trying again.
Products Affected
- GitHub
- Microsoft Defender for Endpoint
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office Publisher
- Microsoft Office SharePoint
- Microsoft Office Word
- Remote Desktop Client
- Role: DNS Server
- Role: Windows Hyper-V
- System Center Operations Manager
- Windows Cloud Files Mini Filter Driver
- Windows Common Log File System Driver
- Windows File Explorer
- Windows IP Routing Management Snapin
- Windows Kernel
- Windows Kernel-Mode Drivers
- Windows LDAP – Lightweight Directory Access Protocol
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Message Queuing
- Windows Mobile Broadband
- Windows PrintWorkflowUserSvc
- Windows Remote Desktop
- Windows Remote Desktop Services
- Windows Resilient File System (ReFS)
- Windows Routing and Remote Access Service (RRAS)
- Windows Task Scheduler
- Windows Virtualization-Based Security (VBS) Enclave
- Windows Wireless Wide Area Network Service
- WmsRepair Service
If you’re using any of these products, you should patch them immediately! Microsoft’s Security Update Guide details mitigations and patches for each vulnerability. You can also use tools to help you apply those patches.
Instantly Fix Risks with SanerNow Patch Management
SanerNow patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. SanerNow patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.

