2025 is upon us! We’re ringing in the new year with – you guessed it – another Patch Tuesday.
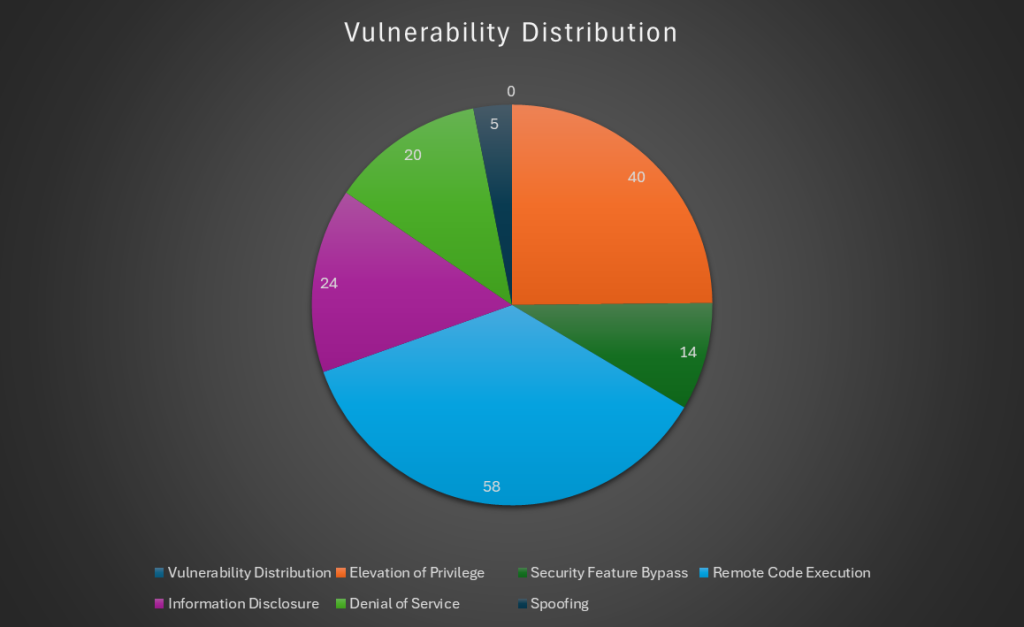
This year’s curtains open with 159 fixes, eight zero-days, and 12 critical flaws. 58 of the flaws found could result in Remote Code Execution. The following chart shows the number of vulnerabilities found in each category.
Zero Days
Of the 8 zero-days found, 3 have been actively exploited, and 5 publicly disclosed.
The actively exploited vulnerabilities are CVE-2025-21333, CVE-2025-21334, CVE-2025-21335, all of which lie within Windows Hyper-V, and result in Elevation of Privilege. Not much information is available on these flaws, but it is known that upon exploitation, an attacker can gain SYSTEM privileges.
The following vulnerabilities have been publicly diclosed:
- CVE-2025-21275 – Windows App Package Installer, Elevation of Privilege: This flaw can, once again, be exploited to gain SYSTEM privileges.
- CVE-2025-21308 – Windows Themes, Spoofing: An attacker would need to persuade the user to load a malicious file onto a vulnerable system, and then interact with it. When the file is viewed in Windows Explorer, Windows will send an authentication request to the remote host, containing the logged-in user’s NTLM credentials. The said credentials can then be cracked to obtain the user’s plain-text password.
- CVE-2025-21186, CVE-2025-21366, CVE-2025-21395 – Microsoft Access, Remote Code Execution: All three of these flaws involve opening specially crafted Access documents in order to trigger RCE.
Products Affected
- .NET
- .NET and Visual Studio
- .NET,.NET Framework, Visual Studio
- Active Directory Domain Services
- Active Directory Federation Services
- Azure Marketplace SaaS Resources
- BranchCache
- IP Helper
- Internet Explorer
- Line Printer Daemon Service (LPD)
- Microsoft AutoUpdate (MAU)
- Microsoft Azure Gateway Manager
- Microsoft Brokering File System
- Microsoft Digest Authentication
- Microsoft Graphics Component
- Microsoft Office
- Microsoft Office Access
- Microsoft Office Excel
- Microsoft Office OneNote
- Microsoft Office Outlook
- Microsoft Office Outlook for Mac
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft Office Word
- Microsoft Purview
- Microsoft Windows Search Component
- Power Automate
- Reliable Multicast Transport Driver (RMCAST)
- Visual Studio
- Windows BitLocker
- Windows Boot Loader
- Windows Boot Manager
- Windows COM
- Windows Client-Side Caching (CSC) Service
- Windows Cloud Files Mini Filter Driver
- Windows Connected Devices Platform Service
- Windows Cryptographic Services
- Windows DWM Core Library
- Windows Digital Media
- Windows Direct Show
- Windows Event Tracing
- Windows Geolocation Service
- Windows Hello
- Windows Hyper-V NT Kernel Integration VSP
- Windows Installer
- Windows Kerberos
- Windows Kernel Memory
- Windows MapUrlToZone
- Windows Mark of the Web (MOTW)
- Windows Message Queuing
- Windows NTLM
- Windows OLE
- Windows PrintWorkflowUserSvc
- Windows Recovery Environment Agent
- Windows Remote Desktop Services
- Windows SPNEGO Extended Negotiation
- Windows Security Account Manager
- Windows Smart Card
- Windows SmartScreen
- Windows Telephony Service
- Windows Themes
- Windows UPnP Device Host
- Windows Virtual Trusted Platform Module
- Windows Virtualization-Based Security (VBS) Enclave
- Windows WLAN Auto Config Service
- Windows Web Threat Defense User Service
- Windows Win32K – GRFX
If you’re using any of these products, you should patch them immediately! Microsoft’s Security Update Guide details mitigations and patches for each vulnerability. You can also use tools to help you apply those patches.
Instantly Fix Risks with SanerNow Patch Management
SanerNow patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. SanerNow patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.


