Valentine’s Day is just around the corner, and Microsoft has already brought us the perfect gift – a personalized hamper of 55 fixed vulnerabilities on Patch Tuesday.
This month brings us fewer flaws than usual, but don’t let your rose-colored glasses fool you! The patches include 4 zero-days, two of which have been actively exploited. The types of vulnerabilities found are shown in the graph below.
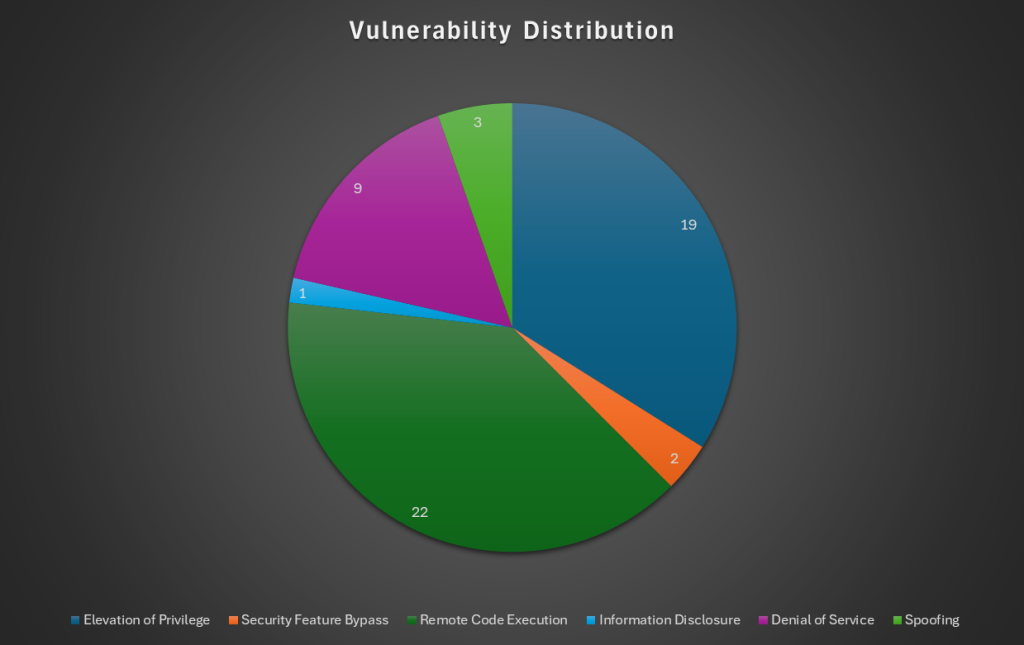
Zero-Days
The following two zero-days have been actively exploited:
CVE-2025-21391 – Windows Storage, Elevation of Privilege: This flaw can be used to delete targeted files on a vulnerable system, which could affect the availability of the service. Further information regarding the method of exploitation has not yet been released.
CVE-2025-21418 – Windows Ancillary Function Driver for WinSock, Elevation of Privilege: This flaw could allow attackers to gain SYSTEM privileges in Windows. Further information regarding the method of exploitation has not yet been released.
The following two zero-days have been publicly disclosed:
CVE-2025-21194 – Microsoft Surface, Security Feature Bypass: This is a hypervisor flaw that enables attackers to bypass Unified Extensible Firmware Interface (UEFI) and compromise the secure kernel.
Once again, not many details about this vulnerability have been released.
CVE-2025-21377 – NTLM Hash Disclosure Spoofing Vulnerability: This bug, which can be triggered by minimal interaction with a malicious file, exposes a Windows user’s NTLM hashes, potentially allowing a remote attacker to authenticate as the user.
Typically, these NTLM hashes can be cracked afterwards to obtain the plain-text password or used in pass-the-hash attacks. No further information has been released yet.
Products Affected
Show some love to your system by patching the following products! Microsoft’s Security Update Guide details mitigations and patches for each vulnerability. You can also use tools to help you apply said patches.
- Active Directory Domain Services
- Azure Active Directory
- Azure Firmware
- Azure Network Watcher
- Microsoft AutoUpdate (MAU)
- Microsoft Digest Authentication
- Microsoft High Performance Compute Pack (HPC) Linux Node Agent
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office SharePoint
- Microsoft PC Manager
- Microsoft Streaming Service
- Microsoft Surface
- Microsoft Windows
- Outlook for Android
- Visual Studio
- Visual Studio Code
- Windows Ancillary Function Driver for WinSock
- Windows CoreMessaging
- Windows DHCP Client
- Windows DHCP Server
- Windows DWM Core Library
- Windows Disk Cleanup Tool
- Windows Installer
- Windows Internet Connection Sharing (ICS)
- Windows Kerberos
- Windows Kernel
- Windows LDAP – Lightweight Directory Access Protocol
- Windows Message Queuing
- Windows NTLM
- Windows Remote Desktop Services
- Windows Resilient File System (ReFS) Deduplication Service
- Windows Routing and Remote Access Service (RRAS)
- Windows Setup Files Cleanup
- Windows Storage
- Windows Telephony Server
- Windows Telephony Service
- Windows Update Stack
- Windows Win32 Kernel Subsystem
Instantly Fix Risks with SanerNow Patch Management
SanerNow patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. SanerNow patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.

