Here’s a story you might have heard before. Or you might have experienced it before. Alex is an IT Security administrator working for a mid-sized company. The company has invested in a robust Endpoint Detection and Response (EDR) solution to protect its endpoints. One day, Alex receives an alert from the EDR about suspicious activity on an employee’s laptop. The EDR identifies a potential vulnerability being exploited and tries to stop it. However, over the next few days, more alerts flood in, indicating that the malware has spread to other devices. Despite the EDR’s efforts, the attack escalates, causing data exfiltration and system downtime. Alex realizes that while the EDR is helpful, it’s not enough to stop the attack entirely.
But this begs the question, should Alex have tried combating the attack? Or preventing it?
Understanding Reactive Security
What Alex did in the above scenario, along with thousands of IT Security admins in the world, is reactive security. It’s the process of combating threats or attacks by reacting to signs of breaches or exploitations. The process typically involves waiting for cyber attackers to breach your IT network, looking for Indicators of Compromise, and then taking necessary actions.
EDRs are one of the key tools used in the reactive security process.
What Alex did in the above scenario, along with thousands of IT Security admins in the world, is reactive security. It’s the process of combating threats or attacks by reacting to signs of breaches or exploitations. The process typically involves waiting for cyber attackers to breach your IT network, looking for Indicators of Compromise, and then taking necessary actions.
EDRs are one of the key tools used in the reactive security process.
- What are EDRs?
EDRs or Endpoint Detection & Response Tools are security tools that monitor your infrastructure continuously to detect potential Indicators of Compromise and combat cyberattacks.
Here’s a simple way to understand how they work. When you get pneumonia, there are symptoms. Cough, fever, chest pain, fatigue, and loss of appetite. Based on these symptoms, you might be diagnosed by your doctor that you have pneumonia. Similarly, when an attack occurs, there are particular symptoms. EDRs collect data, analyze, and find these symptoms to identify an attack and combat it. - Why are they important?
EDRs are vital in combating cyberattacks and are a powerful weapon in the hands of IT and security administrators. Here are 3 important reasons why:- EDRs detect attackers’ activity, and you can automate responses to threats.
- EDRs gather data that can be used for forensic analysis of a cyberattack.
- EDRs are a must for most compliance standards and key requirements in regulations.
But is Reactive Security the Right Way to Fight Cyberattacks?
The vast majority of organizations in the world use this reactive way to combat threats. And unfortunately, stats don’t exactly support the reactive process. The estimated number of cyberattacks in 2024 is beyond 200 million, and the real number might be even higher.
Reactive security has proven time and again that it’s not the right way to fight cyberattacks. Here are a few key limitations of reactive security and EDRs:
- Detection After the Event: Reaction, as the word suggests, is acting after an event happens. This fundamental fact becomes a key limitation, as EDRs can only act after a threat has already infiltrated the system. By then, damage may already be done.
- Limited Scope: The harsh truth about EDRs is that it can’t monitor your entire IT infrastructure. It can focus on endpoints but typically doesn’t address vulnerabilities in networks, cloud environments, or applications. This can give a false sense of security
- Alert Fatigue: An often-missed limitation of EDRs is that they generate a high volume of alerts, many of which are false positives, overwhelming security teams. That begs the question, how much is too much?
Here’s a snippet from an interesting Reddit thread that echoes the voice of this blog.
“EDRs are not enough. No single piece of technology is ever enough that’s why you have the layered defense approach so that if one tool doesn’t thwart a compromise, another will or a combination of tools will severely mitigate the impact”
EDRs aren’t Enough. So, what should we Do?
If the prospect of trying to fight cyberattacks is the entire crux of reactive security, then let’s flip the script and try to prevent it. And that’s where the idea of proactive security comes into play. Proactive security focuses on preventing attacks before they happen. It involves identifying and mitigating vulnerabilities, hardening systems, and continuously monitoring for potential threats.
Proactive security works on the fundamental fact that “Every Attack Leverages a Weakness.” By mitigating the weakness, you reduce your attack surface and, in turn, the chances of a potential cyberattack.
And the best way to mitigate these weaknesses is with vulnerability management.
- Leveraging Vulnerability Management to Implement Proactive Security:
Vulnerability management is the process of identifying, assessing, prioritizing, and remediating the weaknesses in your IT network. For proactive security, vulnerability management is the cornerstone upon which it can be built.
The idea of proactive vulnerability management is simple. Every cyberattack typically exploits a vulnerability or weakness in your network. And all these weaknesses make up your attack surface.
By closing these gaps, you reduce the attack surface and make it difficult for an attacker to leverage and exploit.
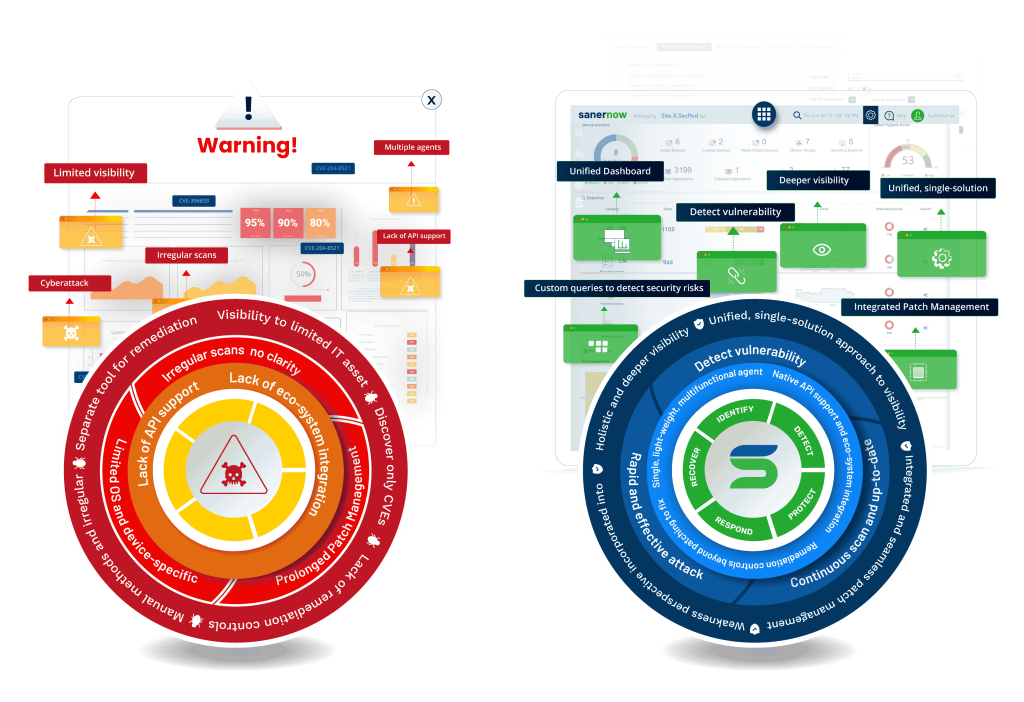
Preventive Cybersecurity: The Saner Way
“Every Attack Leverages Weakness”
That is the fundamental crux of cyberattacks and physical attacks, too. Based on this fundamental truth, SecPod has pioneered the Continuous Vulnerability and Exposure Management (CVEM) framework. The CVEM framework looks from the weakness perspective instead of combating threats or events and secures your network infrastructure against potential threats by uprooting the root cause of the threat itself.
The Saner Platform, built with the weakness perspective, puts prevention first and ensures you are combating vulnerabilities and preventing cyberattacks instead of trying to fight them.
It provides continuous visibility, assessment, and integrated remediation to give you a comprehensive and holistic view and control over your IT. It does what matters, that is, reduce your attack surface.
Conclusion
EDRs are not enough. It’s the harsh truth. But that doesn’t mean they are useless. EDR tools combined with effective vulnerability management can drastically reduce your attack surface and prevent potential cyber threats.
The cybersecurity world desperately needs a shift in how we look at cyberattack prevention. And vulnerability management is the way forward.


