LockBit remains one of the most aggressive ransomware groups, continuously adapting its tactics to target organizations worldwide. Despite law enforcement crackdowns — such as international takedown efforts, infrastructure seizures, and arrests of affiliates — LockBit persists by refining its techniques, exploiting vulnerabilities, and leveraging its Ransomware-as-a-Service (RaaS) model to enable affiliates to carry out attacks.
LockBit ransomware spreads through compromised credentials, phishing emails, and unpatched software vulnerabilities. Once inside a network, affiliates use tools to escalate privileges, disable security measures, and move laterally. While automation assists in identifying entry points, the ransomware’s deployment often involves manual intervention to maximize damage and ensure widespread encryption.
The group relies on a range of sophisticated tactics to infiltrate networks, escalate privileges, and force victims into paying ransom, including:
- Double Extortion: Data is exfiltrated before encryption, allowing attackers to threaten public leaks if ransom demands are not met.
- Triple Extortion: In addition to encryption and data leaks, LockBit sometimes threatens victims with Distributed Denial-of-Service (DDoS) attacks to increase pressure.
- Exploitation of Unpatched Vulnerabilities: LockBit frequently exploits known security flaws, including Citrix Bleed (CVE-2023-4966), Fortinet VPN vulnerabilities (CVE-2018-13379), and ConnectWise ScreenConnect vulnerabilities (CVE-2024-1708).
- Brute-Force and Credential Theft: Weak authentication mechanisms are a primary attack vector, with LockBit using stolen credentials, phishing, and brute-force attacks to gain access to enterprise networks.
- Lateral Movement and Privilege Escalation: Once inside a network, LockBit affiliates use tools like Mimikatz, Cobalt Strike, and PsExec to escalate privileges, disable security measures, and encrypt critical systems.
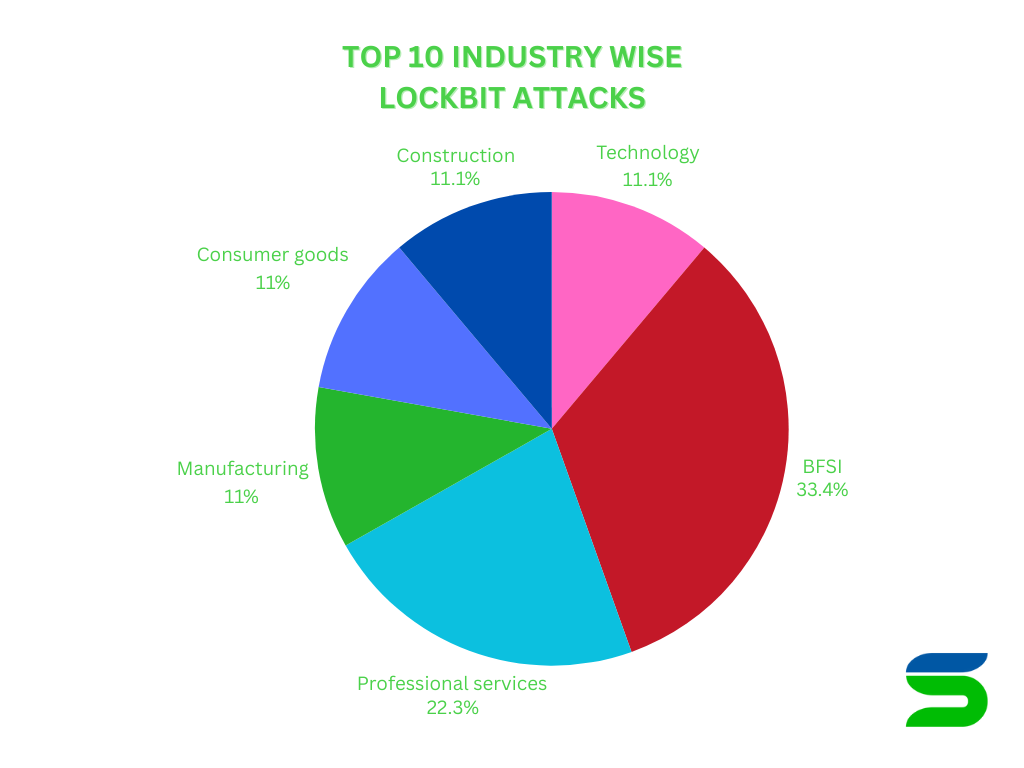
Geographic Operations and Industries Targeted
LockBit primarily targets organizations in North America and Europe but has been observed expanding its operations into Asia, South America, and Australia. The group avoids Russian-based entities, likely due to its origins in Russian-speaking cybercriminal communities and an implicit understanding that targeting local organizations could invite law enforcement scrutiny.
Some of the industries commonly attacked include:
- Healthcare: Hospitals and medical institutions have been frequent targets, leading to disrupted patient care, delayed procedures, and compromised medical records.
- Finance: Banks and financial institutions suffer from service outages, data breaches, and fraudulent transactions.
- Retail: Large-scale retailers have faced operational halts, affecting supply chains and customer transactions.
- Manufacturing: Industrial organizations experience downtime, impacting production and logistics.
- Government and Public Sector: Municipalities, law enforcement agencies, and local governments have been targeted, disrupting public services.
The Financial Implications of LockBit
The financial and operational impact of LockBit ransomware attacks is severe:
- Data Theft and Exposure: Sensitive corporate and personal data are frequently stolen and published on leak sites when ransoms go unpaid.
- Operational Disruptions: Entire IT infrastructures are encrypted, forcing organizations to suspend operations, sometimes for weeks.
- Financial Losses: Victims face ransom demands ranging from hundreds of thousands to millions of dollars, alongside costs associated with system restoration and regulatory fines.
- Reputational Harm: Customer trust is eroded, and affected businesses may face lawsuits or compliance penalties due to data breaches.
Understanding how LockBit operates is very important to strengthening defenses. This blog examines the vulnerabilities it exploits and provides strategies to mitigate these risks.

LockBit’s Recent Attacks and Their Impact
London Drugs (May 2024): Retail Sector Disruption
LockBit’s attack on Canadian retailer London Drugs brought operations to a standstill, affecting supply chains and customer transactions. Point-of-sale systems and logistics networks were encrypted, preventing stores from processing sales and delaying shipments. Employees faced temporary layoffs, and customers experienced service disruptions. The breach exposed vulnerabilities in the retail sector, particularly regarding unpatched systems and weak access controls. Beyond financial losses, the attack damaged consumer trust, prompting a reassessment of incident response and cybersecurity strategies in the industry.
Evolve Bank & Trust (June 2024): Targeting Financial Institutions
LockBit exploited security gaps in Evolve Bank & Trust’s network, compromising sensitive financial data and forcing a temporary suspension of online banking services. Customers and businesses reliant on digital transactions experienced significant disruptions, with account access restricted and payments delayed. Regulatory bodies scrutinized the breach, increasing compliance pressures on financial institutions. The incident highlighted the banking sector’s ongoing challenge in balancing service availability with stringent security measures, reinforcing the need for continuous vulnerability management and stronger authentication mechanisms.
University Hospital Center, Zagreb (June 2024): Impact on Healthcare
The ransomware attack on the University Hospital Center in Zagreb severely impacted healthcare operations, delaying medical procedures and restricting access to critical patient records. Doctors and staff were unable to retrieve essential information, leading to postponed treatments and potential health risks for patients. The attack underscored the healthcare industry’s reliance on interconnected systems and the catastrophic consequences of cyberattacks on public health. Recovery efforts required extensive system restoration, and the hospital faced scrutiny over cybersecurity preparedness. The incident reinforced the urgency of securing healthcare networks through proactive vulnerability detection and rapid incident response.
Misconceptions in Ransomware Defense
Many organizations miscalculate the threat of ransomware by focusing on perimeter security while neglecting internal vulnerabilities. Relying solely on firewalls and endpoint protection overlooks the fact that groups like LockBit exploit misconfigurations and unpatched software within networks. Delayed patching remains a widespread issue, often deprioritized due to operational concerns, leaving critical flaws open to exploitation. Legacy systems exacerbate this risk, as they frequently lack vendor support and remain vulnerable to known attacks.
Weak access controls further amplify exposure. Poor credential management, misconfigured Remote Desktop Protocol (RDP), and the absence of multifactor authentication (MFA) allow attackers to escalate privileges and move laterally. Flat network architectures make this even more dangerous, enabling ransomware to spread rapidly once initial access is gained. Many organizations also struggle with effective incident response, leading to extended downtime and data loss. Without tested recovery strategies, reliable backups, and real-time security intelligence, detecting and mitigating attacks before they cause significant damage becomes increasingly difficult. Shifting from reactive defenses to proactive risk management — through continuous vulnerability assessment, automated remediation, and real-time anomaly detection — remains integral in combating ransomware threats.
Key Vulnerabilities Exploited by LockBit
To understand and mitigate attacks successfully, it is necessary to analyze the key vulnerabilities consistently exploited by the LockBit ransomware group. Each of these weaknesses represents an opportunity for attackers to infiltrate critical systems, proving the importance of maintaining vigilance and enforcing strict patching regimes.
- Citrix Bleed (CVE-2023-4966)
This vulnerability involves sensitive information disclosure in NetScaler ADC and NetScaler Gateway when configured as a Gateway or AAA virtual server. Disclosed in October 2023, Citrix Bleed allows attackers to bypass authentication mechanisms through improper handling of session data. Exploitation of this flaw can lead to significant impacts such as session hijacking, compromising internal systems, and potential lateral movement within networks. Specifically, attackers leverage crafted HTTP requests to extract session cookies, which can provide unauthorized access to high-value network assets. Organizations using affected Citrix products must prioritize the application of patches released by the vendor and employ robust network segmentation practices to reduce exposure.
- ConnectWise ScreenConnect Vulnerabilities (CVE-2024-1708)
Discovered in February 2024, this path traversal vulnerability affects ConnectWise ScreenConnect versions 23.9.7 and earlier. It provides attackers with an avenue for executing remote code or accessing critical data by improperly handling input validation in file paths. The flaw allows the traversal of directory structures, granting malicious actors the ability to manipulate or access files outside the intended scope. Exploitation can result in data breaches or even direct compromise of client systems. Organizations that leverage this tool for remote support must upgrade to newer, patched versions immediately. Additionally, hardening remote access configurations and auditing connected devices regularly are critical preventive measures.
- Fortinet VPN Vulnerabilities (CVE-2018-13379)
This long-standing vulnerability involves an improper limitation of a pathname to a restricted directory within the SSL VPN web portal of certain FortiOS and FortiProxy versions. It allows unauthenticated attackers to download sensitive system files, including user credentials. Exploiting this vulnerability often serves as an initial foothold for attackers to achieve network compromise. Despite its discovery in 2018, it continues to be a favored avenue for exploitation due to unpatched systems that remain in use. To mitigate this threat, organizations must eliminate legacy systems or update to the latest firmware versions, implement strong password management policies, and monitor VPN logs for abnormal activity.
- Other Common Exploits
LockBit’s operations also highlight multiple generic attack vectors such as unpatched software and misconfigured Remote Desktop Protocol (RDP) services. These weaknesses allow for unauthorized access and privilege escalation. For instance, outdated systems often lack current security updates, which attackers exploit to deliver payloads. Similarly, improperly configured RDP infrastructures can leave login interfaces exposed, enabling brute-force attacks or credential stuffing. Proactive risk management through automated patch deployment, disabling redundant RDP functionality, and enforcing multifactor authentication are a must to minimize these risks.
Mitigating LockBit’s Attack Vectors with SanerNow
LockBit’s sustained success in breaching organizations stems from its ability to exploit vulnerabilities that remain unpatched or misconfigured within enterprise networks. Attackers take advantage of software flaws, weak authentication mechanisms, and poor security hygiene to gain initial access and deploy ransomware payloads. Addressing these risks requires a structured approach that incorporates continuous assessment, rapid remediation, and real-time security intelligence.
Continuous Vulnerability Exposure Management (CVEM) with SanerNow
SanerNow provides a unified platform designed to detect, assess, prioritize, and remediate vulnerabilities before they can be exploited by adversaries such as LockBit. The platform’s Continuous Vulnerability Exposure Management (CVEM) methodology integrates multiple security functions into a single, efficient workflow, minimizing the window of exposure for known exploits.
- Comprehensive Attack Surface Visibility: SanerNow actively monitors IT assets, providing an up-to-date inventory of software, configurations, and security gaps. Attackers often exploit outdated systems, shadow IT, and unmonitored devices, making continuous visibility a fundamental requirement for risk mitigation.
- Automated Vulnerability Detection and Risk Prioritization: Leveraging a security intelligence library with over 190,000 vulnerability checks, SanerNow identifies misconfigurations, outdated software, and exploitable flaws. Unlike traditional vulnerability scanners, the platform contextualizes risks based on exploitability metrics, business impact, and active security intelligence feeds.
- Integrated Patch and Configuration Management: Exploits such as Citrix Bleed (CVE-2023-4966) and Fortinet VPN vulnerability (CVE-2018-13379) remain persistent threats due to delayed patching. SanerNow automates patch deployment across Windows, macOS, Linux, and over 550 third-party applications. Additionally, it enforces configuration hardening to eliminate misconfigurations that attackers leverage for lateral movement.
- Advanced Vulnerability Detection and Exposure Analysis: Attackers frequently use credential theft and privilege escalation techniques to maintain persistence. SanerNow continuously assesses endpoint security configurations, identifying weak authentication policies, exposed RDP services, and unauthorized administrative privileges that increase ransomware risks.
- Real-time Monitoring and Anomaly Detection: SanerNow enables security teams to track deviations from baseline configurations and detect suspicious activities indicative of pre-ransomware behaviors. Rule-based and trend-based analysis helps organizations detect anomalies before they escalate into full-blown ransomware incidents.
- Compliance and Security Policy Enforcement: Industries affected by LockBit attacks, such as healthcare and financial services, must adhere to strict regulatory standards. SanerNow aligns vulnerability and patch management operations with frameworks like NIST, HIPAA, PCI DSS, and ISO, ensuring that security policies are enforced, and audit readiness is maintained.
Reducing Ransomware Risks with a Proactive Defense Strategy
LockBit continues to exploit organizations that lack proactive risk management. SanerNow eliminates security blind spots by integrating asset exposure management, vulnerability detection, and remediation in a single, cohesive platform. The ability to rapidly identify and address security gaps minimizes the attack surface, making it significantly harder for ransomware groups to succeed. Organizations seeking a structured approach to ransomware defense can implement SanerNow’s Continuous Vulnerability and Exposure Management platform to minimize risk and strengthen security against emerging threats. Visit our website to learn how SanerNow can enhance your enterprise security.

