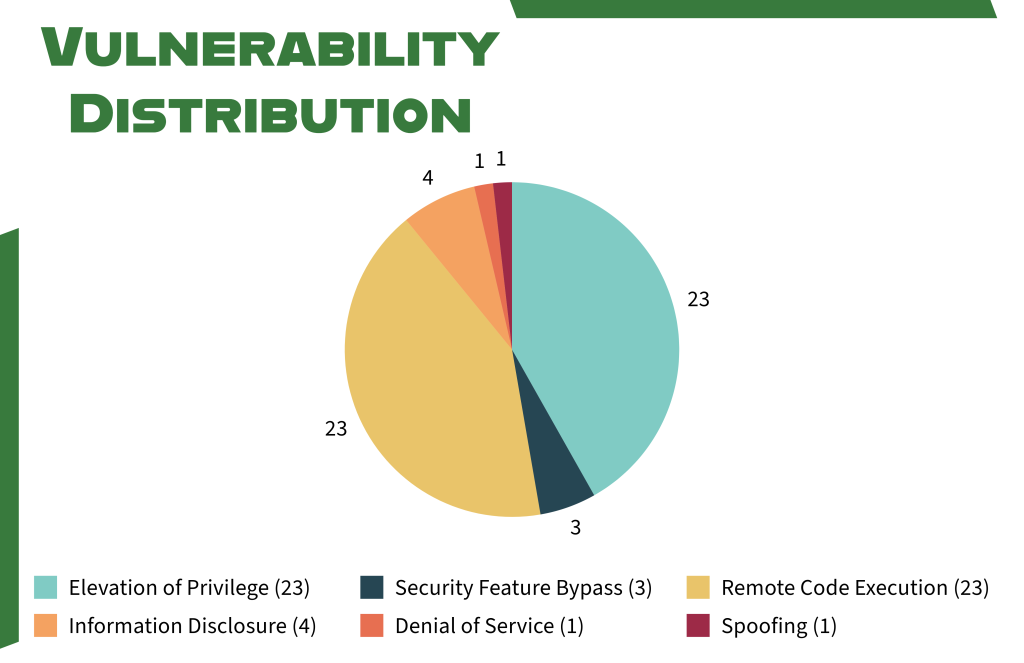
Microsoft’s March 2025 Patch Tuesday has arrived, delivering new security updates and enhancements. This month’s release addresses 57 vulnerabilities, including seven that are classified as zero-day vulnerabilities. Additionally, six “Critical” vulnerabilities involving remote code execution have also been resolved in this Patch Tuesday update.
The chart below displays the vulnerabilities along with their corresponding enumeration.
Zero-Days
This Patch Tuesday, seven zero-day vulnerabilities were addressed, of which six are actively exploited, and one is publicly exposed. The affected products include Microsoft Management Console, Windows NTFS, the Fast FAT File System Driver, and the Win32 Kernel Subsystem.
The six actively exploited zero-day vulnerabilities are:
- CVE-2025-24983: Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability
Use after free in Windows Win32 Kernel Subsystem allows an authorized attacker to elevate privileges locally. Local attackers who can win a race condition can gain SYSTEM privileges on the device.
- CVE-2025-24984: Windows NTFS Information Disclosure Vulnerability
The insertion of sensitive information into a log file in Windows NTFS allows an unauthorized attacker to disclose information with a physical attack. An attacker needs physical access to the target system to plug in a malicious USB drive. Successful exploitation will allow the attacker to read portions of heap memory and steal information.
- CVE-2025-24985: Windows Fast FAT File System Driver Remote Code Execution Vulnerability
Integer overflow or wraparound in Windows Fast FAT Driver allows an unauthorized attacker to execute code locally. An attacker can trick a local user on a vulnerable system into mounting a specially crafted VHD that would then trigger the vulnerability.
- CVE-2025-24991: Windows NTFS Information Disclosure Vulnerability
An out-of-bounds read in Windows NTFS allows an authorized attacker to disclose information locally. Like the above vulnerability, attackers can exploit this flaw by tricking a user into mounting a malicious VHD file. Successful exploitation of this vulnerability will allow attackers to read small portions of heap memory.
- CVE-2025-24993: Windows NTFS Remote Code Execution Vulnerability
Heap-based buffer overflow in Windows NTFS allows an unauthorized attacker to execute code locally. Like the above vulnerabilities, attackers can exploit the flaw by tricking a user into mounting a malicious VHD file.
- CVE-2025-26633: Microsoft Management Console Security Feature Bypass Vulnerability
Improper neutralization in Microsoft Management Console allows an unauthorized attacker to bypass a security feature locally.
Exploitation of the vulnerability requires that a user open a specially crafted file. In an email attack scenario, an attacker could exploit the vulnerability by sending the specially crafted file to the user and convincing the user to open the file. In a web-based attack scenario, an attacker could host a website (or leverage a compromised website that accepts or hosts user-provided content) containing a specially crafted file designed to exploit the vulnerability.
An attacker would not be able to force users to visit the website; rather, he would have to convince them to click a link and open the specially crafted file.
The publicly disclosed zero-day vulnerability is:
- CVE-2025-26630: Microsoft Access Remote Code Execution Vulnerability
Use after free in Microsoft Office Access allows an unauthorized attacker to execute code locally. To exploit the flaw, a user must be tricked into opening a specially crafted Access file. Microsoft mentioned that the flaw cannot be exploited through the preview pane.
Products Affected
The vulnerabilities addressed in this Patch Tuesday affect the products listed below. If you are using any of these products, we strongly recommend applying the patches provided by Microsoft immediately. For more information about the vulnerabilities and the corresponding patches, please refer to Microsoft’s Security Update Guide.
- Microsoft Management Console
- Windows NTFS
- Fast FAT File System Driver
- Win32 Kernel Subsystem
- ASP.NET
- Azure Agent
- Azure ARC
- Azure CLI
- Azure promptflow-core
- Azure promptflow-tools
- Microsoft 365 Apps for Enterprise
- Microsoft Access
- Microsoft Excel
- Microsoft Office
- Microsoft Office LTSC
- Microsoft Visual Studio
- Microsoft Word
- Office Online Server
- Remote Desktop client
- Visual Studio Code
- WinDbg
- Windows 10
- Windows 11
- Windows App Client for Windows Desktop
- Windows Server
Instantly Fix Risks with SanerNow Patch Management
SanerNow patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. SanerNow patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.

