The world is huMONGOous, as is the amount of data we possess.
The above line explains where the word ‘Mongo’ originated and why we need MongoDB. MongoDB is a cross-platform document orientation database. Document databases pair each key with a complex data structure known as a document. Documents can contain many key-value pairs, key-array pairs, or even nested ones. MongoDB will also have vulnerabilities that we can solve using a Vulnerability Management Tool.
Known as a No-SQL database, it does not have traditional table structures and supports JSON-like data structure which is easy to read and understand. A schema need not be defined before inserting data. This is helpful in agile development where there are frequent iterations in development, data changes its form, data types are polymorphic, and the volume of data is massive.
Challenges with massive data and MongoDB Vulnerabilities
How do we make a minor change in the document in the database? How do we merge or replace new data into an existing document? Programmatically, should we fetch the whole document into memory and traverse to the key at which that value needs to be changing? Isn’t it expensive? What are the vulnerabilities?
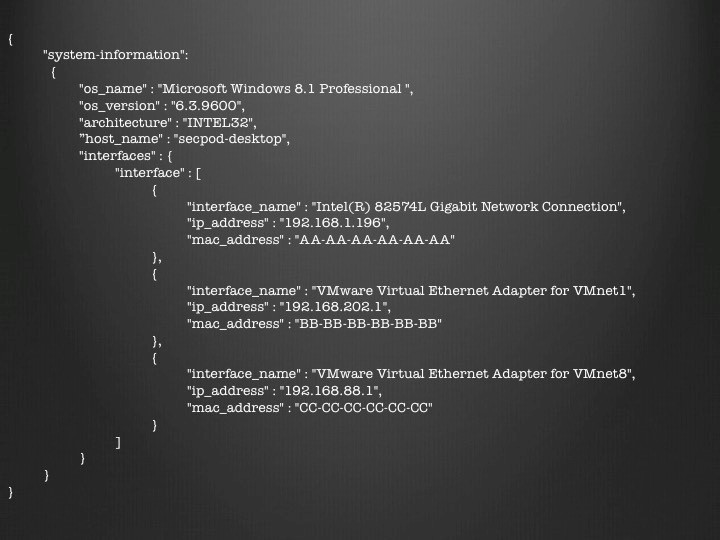
Consider a database containing network interfaces of each system in the organization, a relatively smaller example for ease of understanding:
If one of the network interfaces changes in a system, we intend to update this information in our database. However, The simplest way to do this is to replace the entire document if we maintain a list of all existing interfaces. Often this is not the case.
When a new network interface is added or an existing network interface is modified, a system event occurs with the details of that network interface. Typically, systems would request to update this information into the server. Additionally, we would need to handle similar requests from multiple machines in parallel to update their information. To manage vulnerabilities on multiple systems, a good vulnerability management software will be helpful.
Solution
We use the update command to add or modify an existing document in MongoDB.
Adding an item in an array
In an existing document in a collection, you could use $push to add a new network interface. Instead of $push, $addToSet can also be used, however we will see usage $push in the upcoming examples.
{ $push: { <field1>: <value1>, … } }
Example:
In an existing document in a collection say systeminfo,
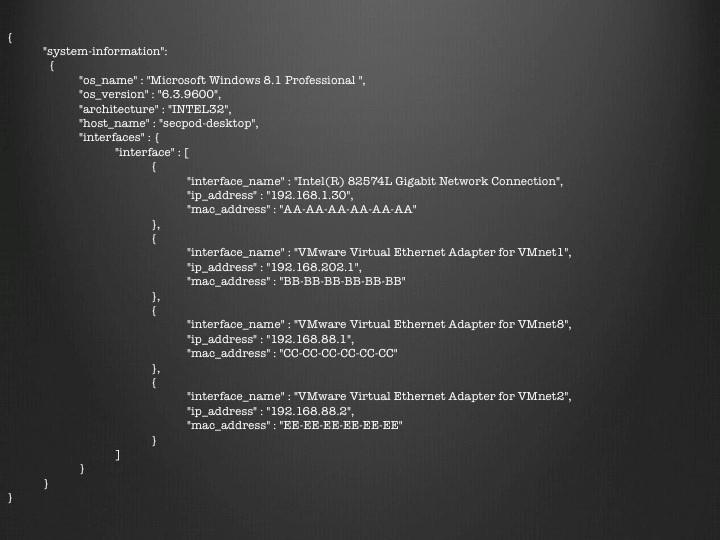
db.systeminfo.update({“system-information.host_name”:”secpod-desktop”},{“$push”:{“system-information.interfaces.interface”:{“interface_name” : “VMware Virtual Ethernet Adapter for VMnet2”, “ip_address” : “192.168.88.2”, “mac_address” : “EE-EE-EE-EE-EE-EE”}}});
As a result, a new network interface gets added in the array of interfaces,
Removing an existing item in an array
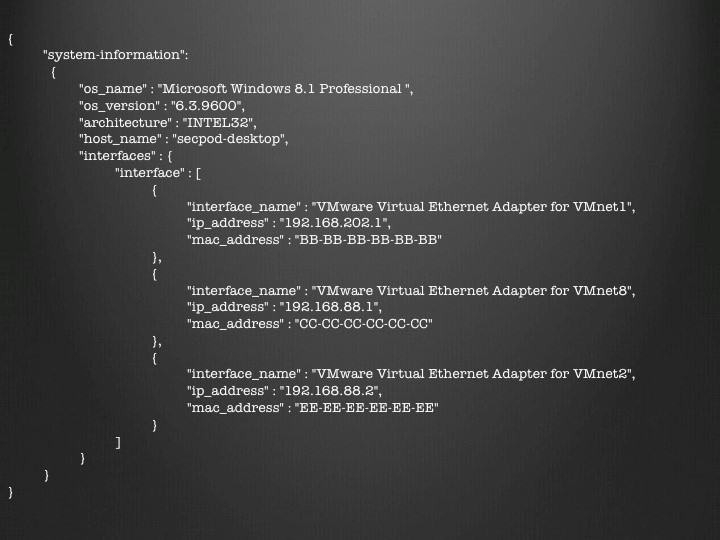
In an existing document in a collection, you could use $pull to remove a new network interface.
{ $pull: { <field1>: <value1>, … } }
Example:
In an existing document in a collection, say systeminfo,
db.systeminfo.update({“system-information.host_name”:”secpod-desktop “},{“$pull”:{“system-information.interfaces.interface”:{“interface_name” : ” Intel(R) 82574L Gigabit Network Connection”}}});
Modifying an existing item in an array
In an existing document in a collection, you could use a combination of $pull and $push to modify a new network interface.
{ $pull: { <field1>: <value1>, … } }
{ $push: { <field1>: <value1>, … } }
Example:
Considering the prior example, in an existing document in a collection, say system info, run the following commands
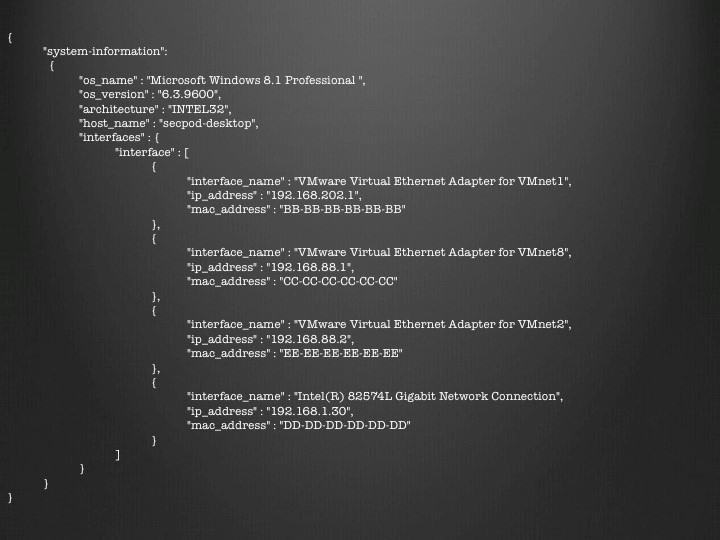
db.systeminfo.update({“system-information.host_name”:”secpod-desktop”},{“$pull”:{“system-information.interfaces.interface”:{“interface_name” : ” Intel(R) 82574L Gigabit Network Connection”}}});
db.systeminfo.update({“system-information.host_name”:”secpod-desktop “},{“$push”:{“system-information.interfaces.interface”:{“interface_name” : ” Intel(R) 82574L Gigabit Network Connection”, “ip_address” : “192.168.1.30”, “mac_address” : “DD-DD-DD-DD-DD-DD”}}});
As a result, the network interface gets modified in the array of interfaces,
Such modifications especially aid in cases where IPs are assigning dynamically, and a change in the database is necessary from time to time.
Summarizing, the above examples avoid the constraints and frustration of modifying data objects in memory. In a scenario of documents containing nested sub-documents or arrays, such as system details containing a huge set of file data, installed patches, and applications, processes, etc., we might not be able to handle huge data in memory. Therefore I hope this helps you understand the Mongodb. vulnerability!
Preeti Subramanian

Thanks for sharing such good information.