Image Credit: Cybellum
A 15-year-old Microsoft Windows Zero-Day vulnerability, dubbed as DoubleAgent, has been discovered by using a vulnerability scanning tool. It could allow anyone to take full control of the system. This vulnerability is a new code injection technique that works on all the versions of Microsoft Windows Operating Systems, even on the latest release of Windows 10. It can exploit any windows architecture, any windows user or any target process including the privileged processes.
Attackers can use this vulnerability to compromise any legitimate process like any antivirus software which runs as a high privileged process. This hijacked antivirus process can then turn against the system they’re meant to protect. Hence called DoubleAgent attack. Anyways, an auto patching solution can patch this vulnerability.
Microsoft Application Verifier
The DoubleAgent attack relies on Microsoft Application Verifier that gives an attacker the ability to replace the standard verifier with his own custom verifier. Microsoft Application Verifier (AppVerif.exe) is a dynamic verification tool for user-mode applications. This tool monitors application actions while the application runs, subjects the application to a variety of stresses and tests, and generates a report about potential errors in application execution or design. It finds subtle programming errors that might be difficult to detect during standard application testing or driver testing. We can use Application Verifier alone or in conjunction with a user-mode debugger. Application Verifier designed specifically to detect and help debug memory corruptions and critical security vulnerabilities.
Code Injection
A verifier provider DLL is loaded into the process and handles performing run time verifications for the application. DoubleAgent allows the attacker to inject any dynamic link library into any process. Once a DLL injects/registers for a process, it is permanently injected by the Windows Loader into the process every time the process starts, even after reboots or updates or reinstalls or patches.
Application verifier provider DLLs registered per executable name, meaning each DLL bounded to a specific executable name. For registering a new application verifier provider to executable, publicly available code is present, DoubleAgent project.
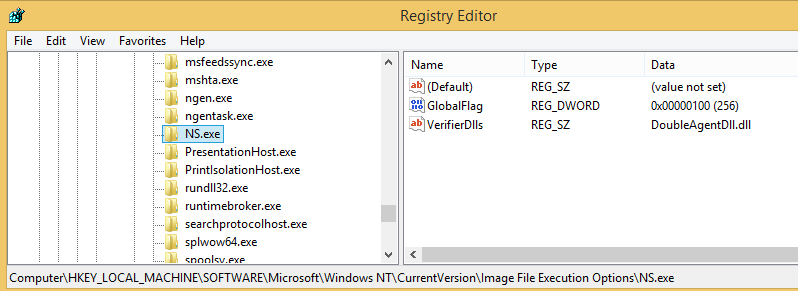
The registration process creates two new registry keys under: HKEY_LOCAL_MACHINE/SOFTWARE/Microsoft/Windows NT/CurrentVersion/Image File Execution Options/PROCESS_NAME (here NS.exe)
DoubleAgent attack used for various practices, like
- Taking full control of antivirus processes.
- Installing malware which is persistent.
- Hijacking the permissions of an existing trusted process.
- Installing backdoors, weakening encryption algorithms or any other modification of the behavior of the process.
- Injecting code to processes of other users or sessions.
- Avast (CVE-2017-5567)
- AVG (CVE-2017-5566)
- Avira (CVE-2017-6417)
- Bitdefender (CVE-2017-6186)
- Trend Micro (CVE-2017-5565)
- Comodo
- ESET
- F-Secure
- Kaspersky
- Malwarebytes
- McAfee
- Panda
- Quick Heal
- Norton
Solution
DoubleAgent exploits an old legitimate feature of Windows and thus cannot patch. As a solution to this vulnerability, applications need to inherit the new design concept of “Protected Processes” introduced by Microsoft more than 3 years ago. Protected process infrastructure only allows trusted, signed code to load and has a built-in defense against code injection attacks. This means that even if an attacker finds a new Zero-Day technique for injecting code, it cannot against the antivirus as its code signs. The new concept is specially for antivirus services. Currently, only Windows Defender has implemented this new design.
- Shakeel

