Strbleed or StringBleed is a critical flaw in implementing Simple Network Management Protocol (SNMP). It leads to an access-control bypass, possibly involving an ISP customization in some cases. The authentication bypass vulnerability affects several IoT devices, which attackers can exploit by sending random values in specific requests. A good Vulnerability Management Tool can tackle these issues. The vulnerability is in track as CVE 2017-5135.
SNMP protocol has gone through different versions till now. There are three ways for client authentication and authentication on remote SNMP devices supported by SNMP protocol. They are named SNMPv1, SNMPv2, and SNMPv3. Two of these methods (SNMPv1, SNMPv2) are affecting by this authentication bypass vulnerability, which relies on a very simplistic authentication procedure that implies sending a human-readable string datatype value (usually public or private) inside an SNMP request from an SNMP client (app) to a device’s SNMP daemon. Vulnerability Management Software can prevent these attacks.
The device reads this string inside the SNMP request, called a “community string,” and replies to the SNMP client request, either with data or by executing an action. SNMP version 3 gives the option to use a user, password, and authentication methods. Therefore, the StringBleed issue resides in how SNMP agent running on different IoT devices handles a human-readable string datatype value called “community string,” which is used by SNMP version 1 and 2.
The Impact of StringBleed:
The Strbleed or StringBleed vulnerability allows remote attackers to bypass authentication and could also allow attackers to execute code remotely on the vulnerable SNMP device and get full read/write permission using any string/integer value. However, It may result in overwriting MIB(Management Information Base) files. And it allows attackers to retrieve the password and other sensitive information from the vulnerable device without guessing the community string.
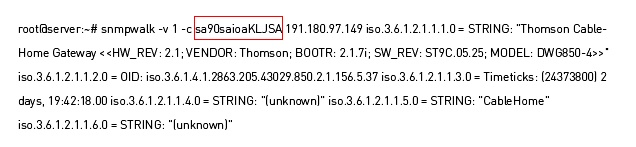
An example of the exploit is below: (https://www.reddit.com/r/netsec/comments/67qt6u/cve_20175135_snmp_authentication_bypass)
The following devices in Shodan are not functioning cor by this vulnerability:
https://www.shodan.io/search?query=DWG850-4
Here the string “sa90saioaKLJSA” has a successful authentication in the SNMP agent. That will happen with any other string integer value.
Around 78 vulnerable cable modem/router models are malfunctioning via StringBleeed. The table here lists the affected modem models.