A major new security flaw has been discovered and it affects practically every device that uses Wi-Fi. Its called KRACK (Key Reinstallation Attacks), and its very easy for attackers to decrypt and spy on anything a victim do online, which includes any passwords that a victim types or any documents sent can be seen by the attacker. It is essential to have a vulnerability management tool to avoid these kind of attacks.
The krack attack vulnerability exists in the WPA2 protocol, which allows attackers to read information. Attackers can abuse this to steal sensitive information, such as credit card numbers, passwords, chat messages, emails, and photos. The attack works against all modern protected Wi-Fi networks. A patch management software can help patch up these vulnerabilities.
What is WPA2 ?
WPA2 (Wi-Fi Protected Access 2) is a network security technology commonly used on Wi-Fi wireless networks. WPA2 is used on all certified Wi-Fi hardware since 2006 and is based on the IEEE 802.11i technology standard for data encryption.
What is WPA2 4 way Handshake ?
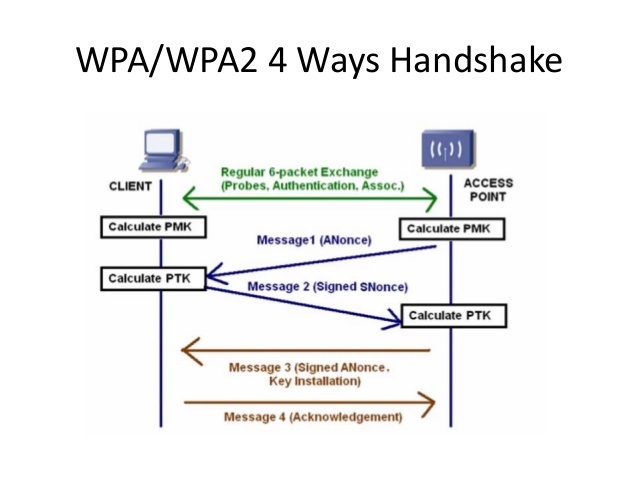 WPA2 4 ways handshake is a type of network authentication protocol established by IEEE-802.11i. The figure depicts the actual messages exchanged during the handshake.
WPA2 4 ways handshake is a type of network authentication protocol established by IEEE-802.11i. The figure depicts the actual messages exchanged during the handshake.
Message 1 : The AP (Access Point) sends a nonce-value to the clinet (ANonce).
Message 2 : The client now has all the attributes to construct the PTK(Pairwise Transient Key). The client sends its own nonce-value (SNonce) to the AP together with a Message Integrity Code (MIC), including authentication.
Message 3 : The AP constructs and sends the GTK(Group terminal key, which is used to decrypt multicast and broadcast traffic) and a sequence number together with another MIC.
Message 4 : Finally the client sends a confirmation to the AP.
Through the four-way handshake, the access point and wireless client (or supplicant) can independently prove to each other that they know the PMK (Pairwise Master Key) without ever disclosing the key.
The process generally does not send the PMK over the network, which keeps this component unshared and strengthens the security.
What is KRACK Attack ?
An attacker repeatedly carries out the Krack Attack by resetting the nonce transmitted in the third step of the WPA2 handshake (4-way handshake). Through this process, the attacker can gradually match encrypted packets seen before and learn the full keychain used to encrypt the traffic.
When the client wants to connect to a protected Wi-Fi network, it executes a 4-way handshake. Also, it negotiates a fresh encryption key to encrypt the traffic. The system will install this key and use it to encrypt normal data frames using an encryption protocol.
Only after receiving message 3 will the key install. AP will re-transmit message 3 if it did not receive an appropriate response as an acknowledgment. So the client may receive message 3 multiple times. Each time client receives the message, it will reinstall the same encryption key, and thereby reset the nonce.
However, an attacker can force these nonce resets by collecting and replaying retransmissions of message 3 of the 4-way handshake. In this manner, by forcing nonce reuse, an attacker can replay, decrypt, and forge packets.
Proof of concept in this demonstation. The exploit code is here
Associated CVE's:
CVE-2017-13077: Reinstallation of the pairwise encryption key (PTK-TK) in the 4-way handshake.
CVE-2017-13078: Reinstallation of the group key (GTK) in the 4-way handshake.
CVE-2017-13079: Reinstallation of the integrity group key (IGTK) in the 4-way handshake.
CVE-2017-13080: Reinstallation of the group key (GTK) in the group key handshake.
CVE-2017-13081: Reinstallation of the integrity group key (IGTK) in the group key handshake.
CVE-2017-13082: Accepting a retransmitted Fast BSS Transition (FT) Reassociation Request and reinstalling the pairwise encryption key (PTK-TK) while processing it.
CVE-2017-13084: Reinstallation of the STK key in the PeerKey handshake.
CVE-2017-13086: reinstallation of the Tunneled Direct-Link Setup (TDLS) PeerKey (TPK) key in the TDLS handshake.
CVE-2017-13087: reinstallation of the group key (GTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
CVE-2017-13088: reinstallation of the integrity group key (IGTK) when processing a Wireless Network Management (WNM) Sleep Mode Response frame.
- krackattacks
How to prevent KRACK Attack ?
- Luckily many Wi-Fi routers and device makers are about to issue patches and here is the list of vendors have already issued the patch.
- Microsoft have already provided a patch to address this issue, and its identified by CVE-2017-13080.
- Its always a good practice to turn on auto updates on your devices. All devices accross platforms are provided with patches. Fix the Client and Router to avoid a Krack Attack.
However, SecPod Saner detects this vulnerability and automatically fixes it by applying security updates. Finally, Download Saner now and keep your systems updated and secure.