Atlassian Confluence recently published a security advisory to patch a critical OGNL(Object-Graph Navigation Language) injection vulnerability existing in Confluence Server and Data Center instance. This vulnerability allowed authenticated and, in some instances, even unauthenticated users to execute arbitrary code on the affected Confluence server instance. The flaw is assigned with the identifier CVE-2021-26084 and is considered critical upon receiving the highest CVSS base score of 9.8. Hence, it is essential to have a vulnerability management solution. The users need to concentrate on the fact that the vulnerable instances can accesse by an administrator or non-administrator user when the “Allow people to sign up to create their account” option is enables in the endpoint.
About the vulnerability (CVE-2021-26084)
Security researcher Benny Jacob discovers this vulnerability which exploits actively now. Affects only on-premise customers by this vulnerability, and Cloud customers are not vulnerable. Normally, the bug requires attackers to be logged in to the network to perform the attack, but under certain circumstances, it even allowed unauthenticated attackers to carry out the attack. A patch management tool can help remediate this vulnerability. The #tag components used in the payload evaluates as OGNL expressions and converts into HTML. There comes the risk when modifying the template payload to include OGNL expressions. That converts into java classes accessed in the Confluence code and executes any command or code inside the payload. So all the on-premise customers who have the vulnerable setup need to update their software.
Affected versions
- Confluence Server/Data Center version < 6.13.23
- Confluence Server/Data Center version 6.14.0 < 7.4.11
- Confluence Server/Data Center version 7.5.0 < 7.11.6
- Confluence Server/Data Center version 7.12.0 < 7.12.5
PoC
Publishes multiple PoCs regarding this vulnerability. However, it was initially published on Github. When the payload "queryString=alt3kx\\u0027%2b#{6*666}%2b\\u0027" is injected into the post request, the response from the server is "<input type="hidden" name="queryString" value="alt3kx{3996=null}" />". Here #{6*666} is the OGNL expression which executes through the exec method of getRuntime() function of java.lang.Runtime class and renders into an HTML page.
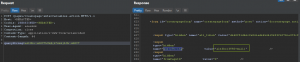 Credits: Github
Credits: Github
Workaround of CVE-2021-26084
Atlassian published the workaround details that applies to the vulnerable instances if the upgrade to the latest versions is not possible. Analyzing the Windows and Linux workaround scripts released, it is evident that the following five files in the Confluence installation directory needed modification to be safe from the attack:
- confluence/users/user-dark-features.vm
- confluence/login.vm
- confluence/pages/createpage-entervariables.vm
- confluence/template/custom/content-editor.vm
- confluence/WEB-INF/atlassian-bundled-plugins/confluence-editor-loader*.jar
Windows: cve-2021-26084-update.ps1
Linux: cve-2021-26084-update.sh
Download the above scripts published by Atlassian and update the $INSTALLATION_DIRECTORY parameter to the location of the Confluence Server installed in the machine. Also, make the scripts executable and run them on the affected instances. Requires a restart of the server after the script runs successfully. If using a Cluster, the script needs executed in each node of the cluster.
Impact
An unauthenticated attacker could exploit the Webwork OGNL injection vulnerability to execute arbitrary code on the affected Confluence Server or Data Center instance.
Solution
Atlassian Confluence server fixes this vulnerability in the following versions:
- Confluence Server/Data Center version 6.13.23
- Confluence Server/Data Center version 7.4.11
- Confluence Server/Data Center version 7.11.6
- Confluence Server/Data Center version 7.12.5
SanerNow can detect this vulnerability. We recommend the users of the affected software install the necessary Confluence Server security updates as soon as possible to stay protected.