Patch Management is one of the most critical components of the vulnerability management and cyberattack prevention process. It streamlines, regulates, and methodizes the application of patches for a smoother process. Following NIST patch management guidelines will strengthen your IT security and zerofy vulnerabilities.
Also, find the easiest way to implement NIST patch management guidelines in your organization.
NIST Patch Management: A Deep Dive
Following NIST’s guidelines for patch management will drastically reduce your investment in time, manpower, and effort. However, you must remember to customize the plan to match your security goals and align it accordingly.
Let’s discuss the major response strategies and recommendations to follow to achieve fruitful NIST patch management and obtain the benefits.
Response Approach for Software Vulnerabilities
Creating a response plan that includes deployment, prioritization, and application of patches is vital in managing software vulns.
Further, there’re other factors to keep in mind for appropriate risk response for vulnerabilities.
Risk response for vulnerabilities is categorized into four different levels:
- Accept: Willingly accept the potential risk of a vulnerability and try to prevent it from being exploited with security controls.
- Mitigate: Reduce the risk by mitigating it by patching or other security measures.
- Transfer: Reduce the risk by sharing the outcome with another party, typically a cybersecurity insurance company.
- Avoid: Completely avoid the risk by uninstalling the vulnerable application or removing the device itself.
Once an appropriate response is selected, the next step is to execute the response according to NIST patch management.
Select the response plan for patching and how to do it. Let’s take a quick look at the response plan:
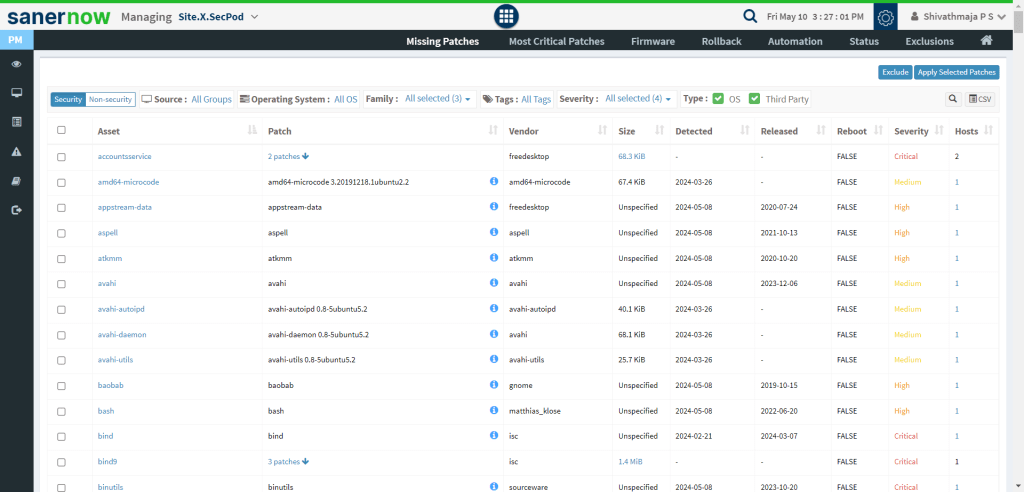
- Prepare to Deploy the Patch:
Before deploying a patch, prioritize it. Further, schedule the deployment so it doesn’t hinder user experience, and acquire and test it as well. This will allow you to validate the patch and ensure any unforeseen issues will not occur.
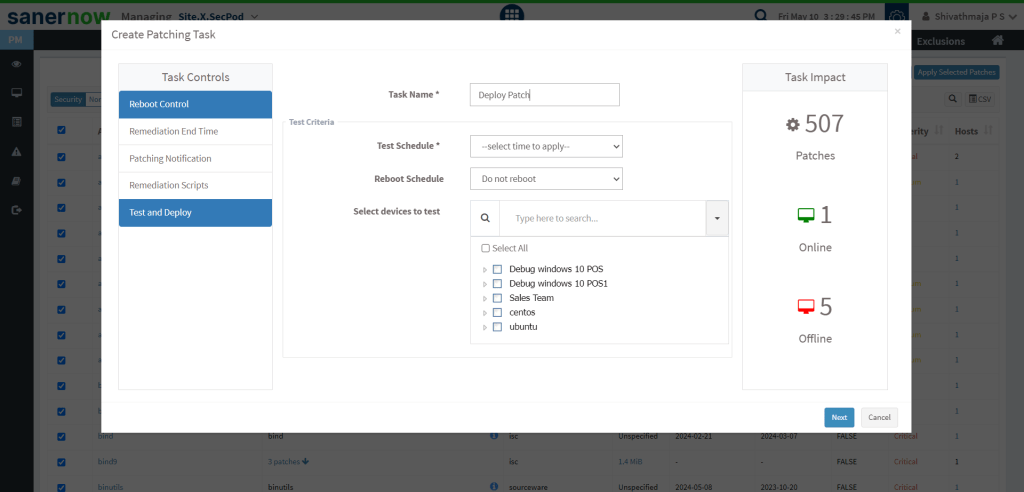
- Deploy the Patch:
Deploying the patch involves steps like proper distribution to all exposed devices and validating its integrity. Further, the process should also include installing the patch and ensuring its application by rebooting the app or device as needed.
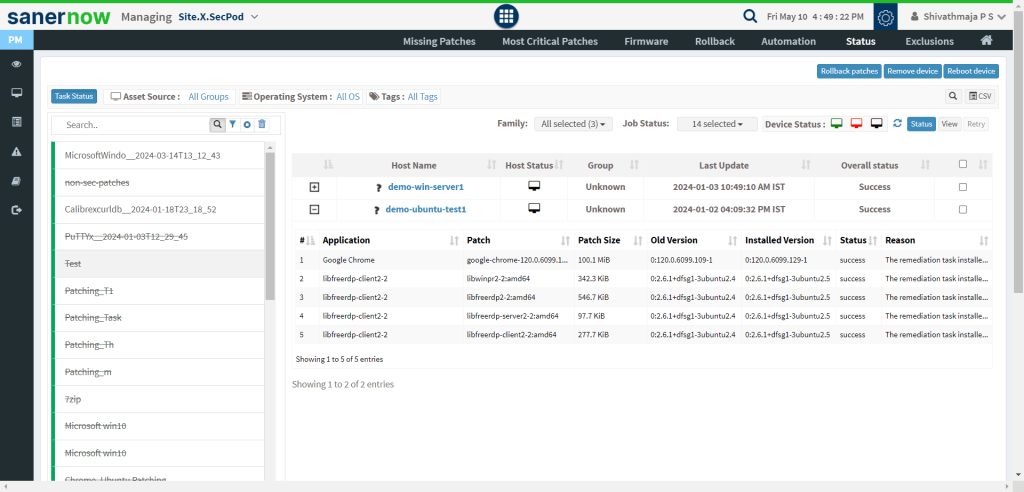
- Verify and Monitor Deployed Patches:
This step is mainly used to confirm if the patch has taken effect and has not reverted to its old state or has caused any issues like device/app crashes.
Key Recommendations for Enterprise Patching
These important tips include reducing patch-related disruptions, proper inventorying, defining risk response, and maintenance plans for different scenarios. The recommendations make for better planning and a smoother patching process.
Let’s take a closer look at some of them:
- Reduce Patch-related Disruptions:
The ultimate goal of patching is to reduce the attack surface. However, the idea is to avoid patching altogether by bringing fewer scenarios that need fixing. By hardening devices, using managed services instead of the software, or working with developers, you must try to bring in the lowest number of vulnerabilities possible. - Up-to-date Inventory of Software and Assets:
An up-to-date inventory will reduce the attack surface. Further, it’s crucial to approach patch management from a device/asset perspective. Some devices are more important than others, so context is critical during patching. - Create and Define Risks Scenario and Respective Maintenance Plans:
The idea is to create action plans for different scenarios that typically happen in the IT management process. The plan includes each step and action that must be followed during the event. The four main scenarios to plan are Routine Patching, Emergency Patching, Emergency Mitigation, and Unpatchable Assets.
Enforcing NIST Patch Management with SanerNow
SanerNow Continuous Vulnerability and Exposure Management is a risk detection and remediation solution that simplifies NIST patch management with ease. With its natively integrated vulnerability detection and patching engine, you will detect vulns, match them with patches, and apply them instantly.
Here’s a brief overview of how SanerNow implements NIST patch management:
- SanerNow provides an automated, up-to-date inventory of assets and helps you visualize your IT infrastructure. This will ensure you don’t miss out on any asset that could potentially expose your network.
- With its natively integrated risk detection and remediation engine, you can quickly and efficiently correlate risks with respective patches. This allows for a faster application of patches and reduced attack surface.
- You can also plan for different risk scenarios by customizing the detection and application of patches with scheduling and automation. This will ensure you are set for any circumstances and can manage effectively.
All in all, SanerNow enforces NIST patch management and helps you achieve compliance with an ultimate security posture.


