Microsoft’s April 2024 Patch Tuesday wasn’t your average update day. While a record number of vulnerabilities were addressed (149), a unique aspect emerged – three critical vulnerabilities resided within a single product: Microsoft Defender for IoT. This blog post dives into these critical defenders for IoT flaws (CVE-2024-29053, CVE-2024-21323, CVE-2024-21322) and sheds light on a concerning zero-day exploit (CVE-2024-26234) patched this month.
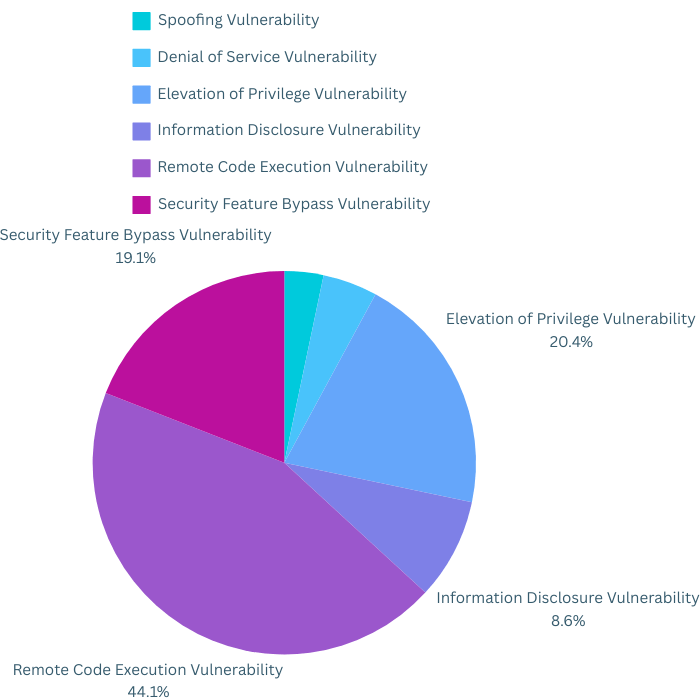
Here’s a breakdown of the types of vulnerabilities patched:
Remote Code Execution (RCE): A significant number of patches, 67 to be exact, targeted RCE vulnerabilities. These are particularly critical as they allow attackers to execute malicious code on a victim’s machine remotely.
Elevation of Privilege: Patches were rolled out to address 31 vulnerabilities that could grant attackers escalated privileges within a system.
Security Feature Bypass: 29 vulnerabilities allowed attackers to bypass security features, potentially exposing systems.
Other vulnerabilities addressed included information disclosure (13), denial-of-service (DoS) (7), and more.
While the number of patches is impressive, it’s important to note that not all vulnerabilities were critical. Microsoft rated Only three ” critical, ” meaning they could be exploited with minimal user interaction. The majority fell under the “important” category, requiring some form of social engineering to be effective.
Summary Chart
Defender for IoT Under Siege
As the guardian of our Internet of Things (IoT) and Operational Technology (OT) devices, Microsoft Defender for IoT plays a vital role. However, this Patch Tuesday exposed its vulnerabilities:
Unrestricted File Upload (CVE-2024-29053): This critical vulnerability allowed any authenticated user to upload a malicious file, potentially taking control of the system or compromising sensitive data on the Defender for IoT sensor. The lack of access restrictions makes this particularly problematic.
Update Manipulation Vulnerability (CVE-2024-21323): This vulnerability involved a weakness in how Defender for IoT receives updates. An attacker with some control over the update delivery process could exploit this flaw. This could lead to injecting a malicious update package, potentially overwriting critical files and compromising the sensor’s functionality or rendering it inoperable.
Administrative Access Abuse (CVE-2024-21322): While requiring prior administrative access to the Defender for IoT web application limits its reach, it highlights the importance of strong access controls and user privilege management. An attacker with admin access could exploit this vulnerability to gain even more control over the system.
Zero-Day Threat (CVE-2024-26234)
Adding another layer of urgency, a separate zero-day vulnerability, CVE-2024-26234, was addressed this Patch Tuesday. While Microsoft initially indicated that this vulnerability was not known to be exploited, they later acknowledged its exploitation in the wild. This zero-day exploit involved a malicious driver disguised with a valid Microsoft certificate. This vulnerability allowed attackers to deploy backdoors and potentially compromise systems.

Microsoft Security Bulletin Summary for April 2024
In addition, this release includes security updates for the following products, features, and roles.
- .NET and Visual Studio
- Azure
- Azure AI Search
- Azure Arc
- Azure Compute Gallery
- Azure Migrate
- Azure Monitor
- Azure Private 5G Core
- Azure SDK
- Mariner
- Microsoft Azure Kubernetes Service
- Microsoft Brokering File System
- Microsoft Defender for IoT
- Microsoft Edge (Chromium-based)
- Microsoft Install Service
- Microsoft Office Excel
- Microsoft Office Outlook
- Microsoft Office SharePoint
- Microsoft WDAC ODBC Driver
- Microsoft WDAC OLE DB provider for SQL
- Windows Hyper-V
- SQL Server
- Windows Authentication Methods
- Windows BitLocker
- Windows Compressed Folder
- Windows Cryptographic Services
- Windows Defender Credential Guard
- Windows DHCP Server
- Windows Distributed File System (DFS)
- Windows DWM Core Library
- Windows File Server Resource Management Service
- Windows HTTP.sys
- Windows Internet Connection Sharing (ICS)
- Windows Kerberos
- Windows Kernel
- Windows Local Security Authority Subsystem Service (LSASS)
- Windows Message Queuing
- Windows Mobile Hotspot
- Windows Proxy Driver
- Windows Remote Access Connection Manager
- Windows Remote Procedure Call
- Windows Routing and Remote Access Service (RRAS)
- Windows Secure Boot
- Windows Storage
- Windows Telephony Server
- Windows Update Stack
- Windows USB Print Driver
- Windows Virtual Machine Bus
SanerNow Vulnerability Management and SanerNow Patch Management detect and automatically fix these vulnerabilities by applying security updates. Finally, use SanerNow to keep your systems updated and secure.