AgeLocker Ransomware targeting QNAP network-attached storage (NAS) devices have been used by attackers to encrypt user data and demand a ransom. It has been found after research that no unpatched vulnerability was found to be exploited in the use of AgeLocker ransomware attack, whereas all the known affected QNAP NAS Devices are running older unpatched QNAP device firmware which needs to be updated.
AgeLocker Ransomware Details:
AgeLocker malware name originates with the use of Actually Good Encryption (AGE) algorithm to encrypt data. Researchers have warned that once data is encrypted with the malware there is no way to decrypt it without paying the ransom to the attackers.
Last week QNAP published a security advisory providing the technical details of the malware and steps to mitigate the attack. Currently, intelligence has pointed out that AgeLocker affected systems are macOS and Linux devices. When the ransomware has encrypted the files, it leaves behind a ransom note named HOW_TO_RESTORE_FILES.txt stating the victim that their QNAP device has been targeted for a ransomware attack and data is encrypted with a special encryption algorithm as shown in the below screenshot.
Unfortunately a malware has infected your QNAP and a large number of your files has been encrypted using a hybrid encryption scheme.
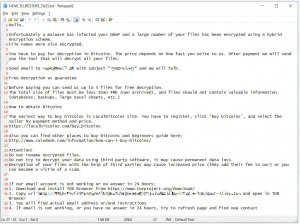
Image Credit: bleepingcomputer
The vendor also added in an alert that older versions of the PhotoStation app are also affected by the known issue.
QNAP Product Security Incident Response Team (PSIRT) has found evidence that the ransomware may attack earlier versions of Photo Station. We are thoroughly investigating the case and will release more information as soon as possible.
Affected products
QNAP NAS devices running older versions of QTS(known as QNAP device firmware) and older versions of PhotoStation app mostly on macOS and Linux.
Impact
This issue allows remote attackers to encrypt files on the affected system and demand for ransom.
Solution
The Vendor has published a security advisory stating the technical details of mitigating the vulnerability and to make sure issues have been patched.