Squid is an open-source web caching and Internet proxy application which is widely used for speeding up the webserver and aiding in its security. A heap buffer overflow vulnerability has been discovered in some versions of the Squid web proxy cache servers. This vulnerability is tracked as CVE-2019-12527 and could be exploited by attackers to trigger DoS condition or execute arbitrary code on the vulnerable servers. The root cause of this vulnerability is the incorrect buffer management used within the application.
Technical Details:
HTTP protocol supports various authentication schemes and many among them involve the use of the “Authorization ” header with the following format,
Authorization: <type> <credentials>
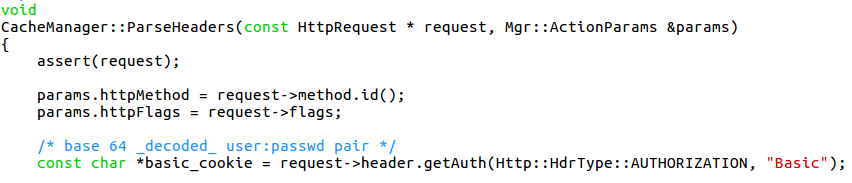
When Squid proxy vulnerabilities on the server receive an incoming HTTP request for cache manager, the CacheManager::ParseHeaders function is called to parse the headers of the request. If the header contains an “Authorization” string that starts with a value “Basic“, the function HttpHeader::getAuth is called.
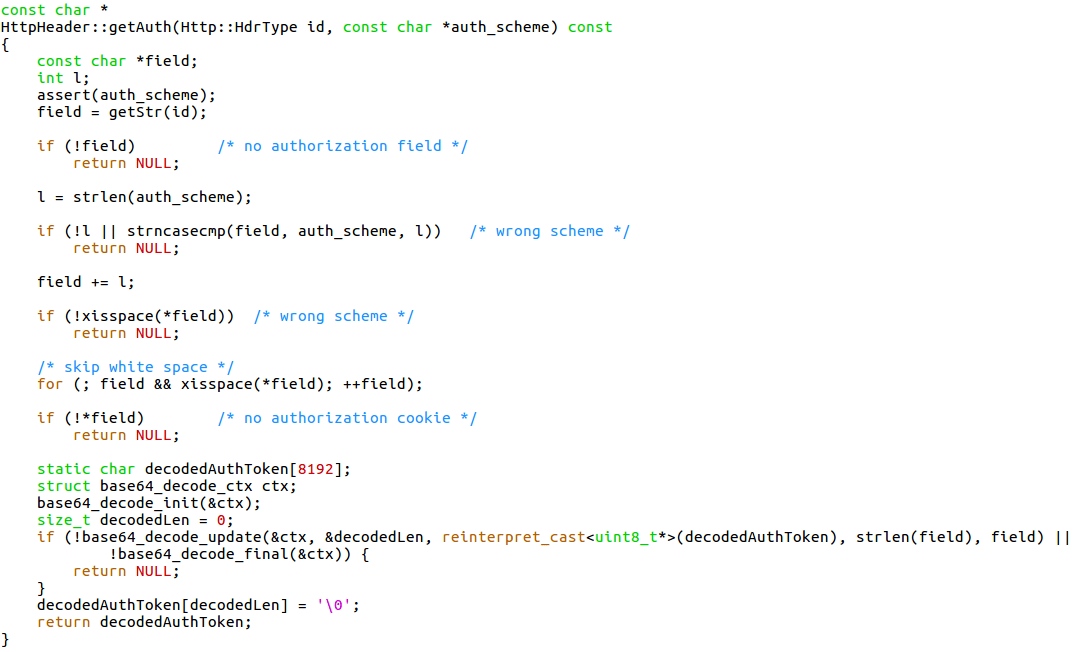
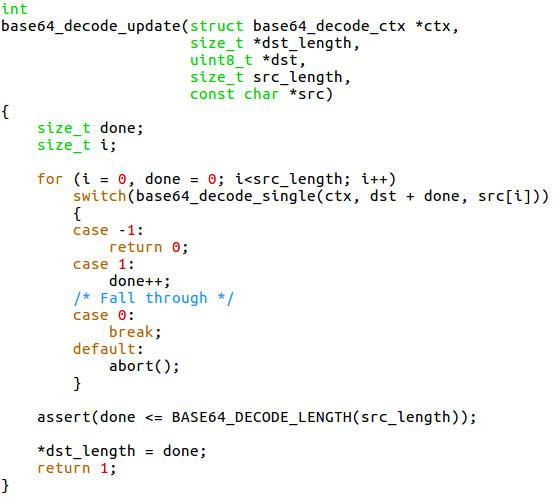
The HttpHeader::getAuth function uses an 8192-byte buffer namely decodedAuthToken, into which it performs base64-decoding of <credentials> using base64_decode_update function. If the decoded data is over 8192 bytes, a buffer overflow will happen.
Thus if an attacker sends a crafted request with ‘Authorization: Basic’ header followed by a credential string of very large length, this large string is forwarded to base64_decode_update function for decoding. If the length of the input string is that much large that decoded data is over 8192, the result will overflow the 8192-byte buffer size allocated resulting in the buffer overflow condition.
Affected Products:
All Squid versions up to 4.0.23 and including 4.7 built with Basic Authentication features are vulnerable. This issue is limited to traffic accessing the Squid Cache Manager reports or using the FTP protocol gateway.
Impact:
This vulnerability allows a malicious user to write a substantial amount of arbitrary data to the heap, potentially gaining the ability to execute arbitrary code. On systems with memory access protections, this can result in the Squid process being terminated unexpectedly resulting in a denial of service for all clients using the proxy.
Solution:
According to Squid security advisory, the vulnerability has been fixed in Squid version 4.8.
Please refer to this KB article to patch using SanerNow.