Apache HTTP server recently fixed two security vulnerabilities, out of which a wildly exploited Zero-Day flaw also existed. Attackers use a path traversal flaw existing in the application to map URLs to files outside the expected document root, leading to information disclosure. This zero-day CVE-2021-41773 is critical and has wild exploitation. Therefore, a Vulnerability Management Software can prevent these attacks.
According to the Apache advisory published, the zero-day flaw also fixed another vulnerability, CVE-2021-41524, in the same patch. A null pointer dereferences flaw existing in the application allowed attackers to cause a denial-of-service attack on the Server and is rated moderate by the Apache security team. A good Vulnerability Management Tool can resolve these issues.
Zero-Day vulnerability (CVE-2021-41773)
Ash Daulton and the cPanel Security Team discovered this vulnerability on September 29th and reported it to the Apache security team. This vulnerability is introduced due to a change made to path normalization in an Apache HTTP Server version 2.4.49. The attacker used this path traversal flaw existing in the application to map URLs to files outside the expected document root. These requests succeed when the files outside the document root are not protected by the “require all denied” configuration. Additionally, attackers can also cause information disclosure by leaking the source of interpreted files like CGI scripts.
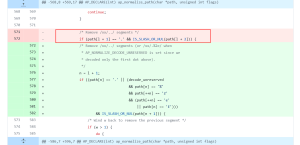
Since this vulnerability is exploited in the wild, users of the Apache HTTP Server are advised to update to the patch version released immediately. Hence, the image below displays this vulnerability’s root cause in the Apache HTTP Server vulnerable code. It fails to check the ‘/xx/.%2e/‘ characters in the payload, which the attackers use to exploit this zero-day. So this check also implements in the patch version as shown in the image.
Null pointer dereference vulnerability (CVE-2021-41524)
LI ZHI XIN from NSFocus Security Team reported this issue on September 17th to the Apache security team. Attackers can use a specially crafted HTTP/2 request to exploit the application’s null pointer dereference flaw existing in version 2.4.49. However, on successful exploitation, attackers will be able to cause a Denial-of-Service condition in the HTTP Server. Also, Apache claims that there is no trace of active exploitation of this vulnerability. Still, users need to upgrade their application to the patched version to stay protected from this flaw.
PoC
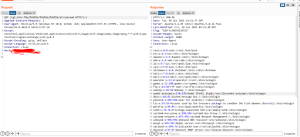
As the information about vulnerable payloads is public information, many PoCs are publishing in the Twitter accounts of Security researchers. Below is a one-line PoC that can be of use to perform the attack on a vulnerable Server. Moreover, the attackers can get the “/etc/passwd” information as seen in the below image by using the payload “$host/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd”. This same part is in use by the below script to fetch the /etc/passwd file information.
"cat targets.txt | while read host do ; do curl --silent --path-as-is --insecure "$host/cgi-bin/.%2e/%2e%2e/%2e%2e/%2e%2e/etc/passwd" | grep "root:*" && echo "$host \033[0;31mVulnerable\n" || echo "$host \033[0;32mNot Vulnerable\n";done"
Credits: @h4x0r_dz
Impact
An attacker could exploit the path traversal and null pointer dereference vulnerability existing in the affected version of Apache HTTP Server to map URLs to files outside the expected document root or cause an information disclosure and denial of service in the Server.
Affected version by Apache HTTP Server Zero-Day Vulnerability
Apache HTTP Server version 2.4.49
Solution
Apache HTTP Server version 2.4.50
SanerNow VM detects these vulnerabilities. Therefore, We strongly recommend applying the security updates for all vulnerabilities on high priority.