Millions of routers are exposed to a security flaw that existed for a decade in home routers with Arcadyan firmware. This actively exploited flaw tracked under CVE identifier CVE-2021-20090 has found its way into routers provided by at least 20 models across 17 different vendors and 11 countries. A patch management tool can remediate this vulnerability. Devices from multiple vendors and ISPs, including Asus, British Telecom, Deutsche Telekom, Orange, O2 (Telefonica), Verizon, Vodafone, Telstra, and Telus, are there in that list. The discovered 13 Internet Service Providers (ISPs) are used in Argentina, the U.S., Australia, Canada, Germany, Japan, New Zealand, Mexico, Netherlands, Russia, and Spain.
Tenable discovered a critical path traversal vulnerability. When exploited, this vulnerability enables attackers to bypass authentication to the web interface of routers, granting them access to other devices on a home or corporate network and observing that threat actors are actively exploiting this vulnerability from Wuhan, Hubei province, China. These attackers are using malicious tools to deploy a Mirai botnet variant. Having a vulnerability management software is essential here.
Vulnerability Details (CVE-2021-20090)
The path traversal vulnerability exists due to improper access permission set for a list of folders and files. It will allow unauthenticated users to access sensitive information. Attackers can use the ‘valid httoken’ obtained in further requests to retrieve sensitive information, such as the ‘admin’ password.
Affected Applications
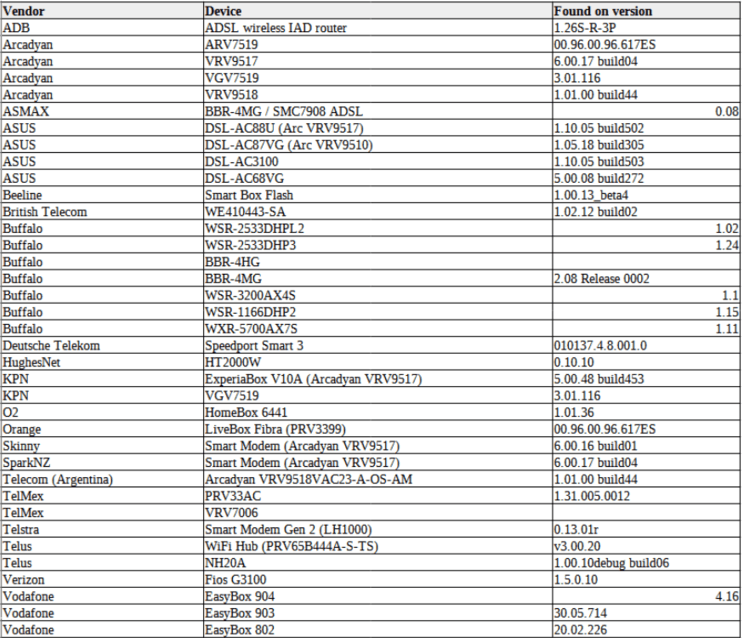
Security researchers have found that Arcadyan firmware, used in routers from multiple vendors, is vulnerable. Below is the attached list of affected devices from different vendors:
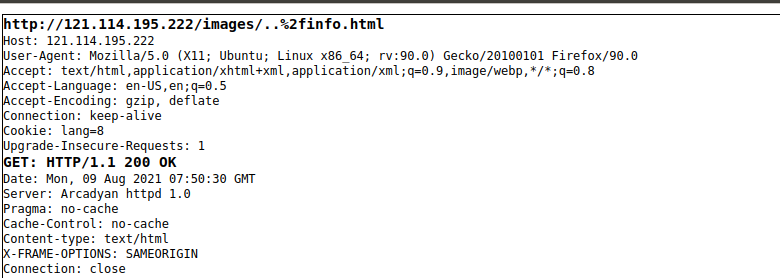
Attached below are a screenshot of an HTTP request and response on a vulnerable router allowing access to a page that restricts authenticated users:
Another two vulnerabilities affecting Buffalo WSR-2533 models are tracked under CVE identifiers CVE-2021-20091 and CVE-2021-20092.
Vulnerability Details (CVE-2021-20091)
The remote code execution vulnerability exists due to improper validation of user-supplied input by the web interface of the Buffalo router. Attackers can inject a crafted parameter from ‘apply_abstract.cgi’ into the device’s global config file, allowing them to insert a new line into the configuration file and enable telnetd.
Vulnerability Details (CVE-2021-20092)
The information disclosure vulnerability exists due to improper access control. An unauthorized actor can get a valid token by navigating to the ‘loginerror.html’ page. Attackers can use the ‘valid httoken’ obtained in further requests to retrieve sensitive information, such as the ‘admin’ password.
Affected Applications
Buffalo WSR-2533DHPL2 firmware version <= 1.02 and WSR-2533DHP3 firmware version <= 1.24
Solutions
We strongly recommend updating the router to the latest available Arcadyan firmware version.