Microsoft team patched a critical and exciting vulnerability in the Netlogon Remote Protocol of the Windows server last month. zero logon vulnerability discovered by the Cybersecurity firm Secura (dubbed as Zerologon), has received the highest severity score of 10.0. The vulnerability is identified as CVE-2020-1472 and allows an attacker to successfully compromise the vulnerable Domain controller by just setting up a TCP connection with it. This vulnerability is treated as severe because even an unauthenticated attacker can gain the Domain Admin privileges by using the domain controller credentials. A vulnerability management tool can stop the same.
zero logon Vulnerability Details:
The Netlogon Remote Protocol is an RPC interface available on Windows domain controllers which is basically to facilitate the authentication between users and machines, especially to the users logging in to the servers using NTLM protocol. This protocol also allows various functionalities, and notably a computer within the domain to update its password. NRP protocol is as unique since it uses a customized cryptographic protocol to prove client and server authenticity, i.e by knowing a shared secret key. This shared secret key is a hash of the client’s computer account password. Using a patch management software is a method to remediate this vulnerability.
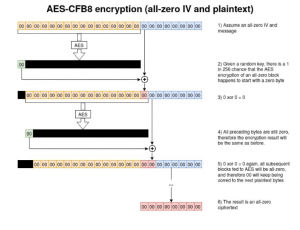
As we all know, authentication attempts are sensitive and hence all the authentication requests take place over an encrypted connection. But the Secura researcher discovered that the domain controllers forced to fall back to unencrypted RPC communication when performing authentication requests. After falling back to an unencrypted communication, a flaw in the Netlogon AES-CFB8 cryptographic negotiation algorithm used to try and steal the credential.
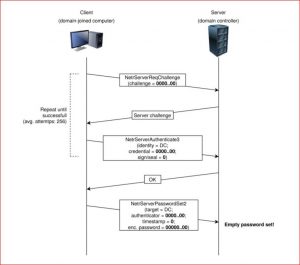
The image here shows that if an attacker is successful in making the communication happen in an unencrypted mode after the TCP handshake, he can later spoof the response message obtained by the Domain Controller to trick the target machine to assume the login is successful.
Image Credit: Secura
Netlogon AES-CFB8 cryptographic negotiation algorithm flaw:
When encrypting a message consisting only of zeroes, with an all-zero Initialisation Vector(IV), there is a 1 in 256 chance that the output will also contain only zeroes.
Proof-of-Concept in zero logon vulnerability:
A PoC is published to exploit this vulnerability. As you can see below, this is the part of the exploit function in POC. Here the flaw in the AES-CFB8 algorithm is know the Client Credential. When the plaintext and ciphertext set to 8 zeros, for 1 in 256 session keys, the correct Client Credential will consist of 8 zeroes.
plaintext = b'\x00' * 8
ciphertext = b'\x00' * 8
try:
server_auth = nrpc.hNetrServerAuthenticate3(
rpc_con, dc_handle + '\x00', target_computer + '$\x00', nrpc.NETLOGON_SECURE_CHANNEL_TYPE.ServerSecureChannel,
target_computer + '\x00', ciphertext, flags
)
assert server_auth['ErrorCode'] == 0
Here when assert server_auth[‘ErrorCode’] value becomes zero, we assume our plaintext value is the right one and hence the client credential can be obtained. Further, the attacker can make use of NetrServerPasswordSet2 function to update the password to the desired value. Similarly, any computer in the domain can compromise including admin.
Impact of zero logon vulnerability
An attacker who successfully exploited the vulnerability can take over the domain controller. Run a specially crafted application on any device on the network.
Affected Products
Affects all Microsoft Windows Servers that use MS-NRPC to connect to a domain controller except server 2008.
- Microsoft Windows Server 2019
- Microsoft Windows Server 2016
- Microsoft Windows Server 2012
- Microsoft Windows Server 2012 R2
- Microsoft Windows Server 2008 R2 Service Pack 1
Solution
Microsoft has released a security fix in its monthly Patch Tuesday updates for August 2020.
SanerNow security content has published to detect and mitigate these vulnerabilities. We strongly recommend applying the security updates as soon as possible following the instructions published in our support article.


Also Windows 2003 and Windows 2008 (not R2) are affected. However, no patch will be issue. Windows 2003 and Windows 2008 are out of support, you should dismiss them as soon as possible.
Which Patch we need to install to fix CVE2020-1472 issue ?
MS portal didn’t include server 2003 and 2008 in affected platform list, hence its not mentioned in the blog. We agree that server 2003 is already End-of-life, but in that case MS portal would have mentioned server 2008 since they release updates for this OS under ESU (Extended Security Update) section.
Patches differ from OS to OS. https://portal.msrc.microsoft.com/en-US/security-guidance/advisory/CVE-2020-1472 already has KB details that are to be installed to patch this vulnerability depending on your OS.
Also, it can be patched using our SanerNow platform with ease, https://support.secpod.com/hc/en-us/articles/360013395037-Zerologon-Patching-Netlogon-Elevation-of-Privilege-Vulnerability-CVE-2020-1472-using-SanerNow