A major ransomware attack named “BadRabbit” is disrupting systems across Europe. The attack has been spreading wildly. BadRabbit locks out a user from login and demands a ransom worth of ~300$ in BitCoin. Some of the countries that are targeted are Russia, Ukraine, Bulgaria, and Turkey. Russian victims were the biggest targets accounting to about 71% of the attack.
The characteristics of NotPetya and BadRabbit looks to be the same. While some of the noticeable differences are, Badrabbit uses custom kernel compared to NotPetya, and in case of NotPetya decryption was not possible whereas in case of BadRabbit decryption might be possible with the criminal’s private key.
As group-ib reports “BadRabbit has same functions for computing hashes, network distribution logic and logs removal process, etc. as NotPetya”.
A drive-by download attack is conducted which leads to the infection of BadRabbit. According to Cisco’s Talos findings, BadRabbit is also using a version of the EternalRomance exploit to spread. This exploit, which comes from the 7 NSA hacking tools which are leaked by a mysterious group Shadow Brokers. Previously we had seen NotPetya using this tool to spread.
How BadRabbit works?
BadRabbit is spreading via a drive-by-downloads mechanism, here are the steps of infection,
- Users visits compromised websites.
- Websites prompts with fake adobe flash player update ‘install_flash_player.exe’
- User accepts the prompt and ‘install_flash_player.exe‘ will be downloaded.
- Executes install_flash_player.exe with elevated privileges.
- The updated deploys the BadRabbit ransomware Attack.
What happens after the execution of ‘install_flash_player.exe‘?
- A file by the name ‘C:\Windows\infpub.dat‘ will be dropped by ‘install_flash_player.exe’ and will be executed by the command ‘C:\Windows\system32\rundll32.exe C:\Windows\infpub.dat, #1 15.‘
- Infpub.dat will drop the ‘C:\Windows\cscc.dat‘ and ‘C:\Windows\dispci.exe‘ files.
- Infpub.dat will then create a Windows service called ‘Windows Client Side Caching DDriver‘ that is used to launch the cscc.dat driver.
- dispci.exe in combination with the cscc.dat driver, is responsible for the disk encryption and ransom screen.
- ‘drogon‘ task is created which will shutdown the machine.
- ‘rhaegal‘ task is created which is responsible of launching ‘dispci.exe‘ when user logs on to the computer.
- After infecting a machine, it used a tool called ‘Mimikatz‘ to get the credentials from memory, also
Indicator’s of Compromise:
Hashes
630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da
579fd8a0385482fb4c789561a30b09f25671e86422f40ef5cca2036b28f99648
8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93
Files
C:\Windows\infpub.dat
C:\Windows\System32\Tasks\drogon
C:\Windows\cscc.dat
C:\Windows\dispci.exe
C:\Windows\System32\Tasks\rhaegal
C2C
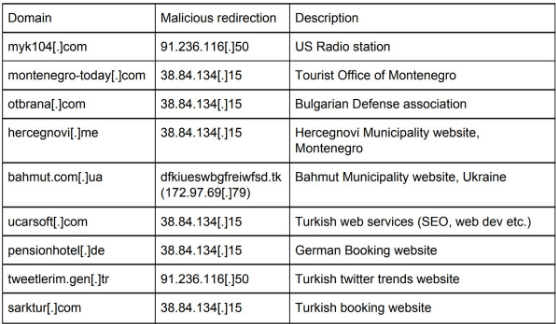
It appears the attackers behind #Badrabbit have been busy setting up their infection network on hacked sites since at least July 2017. - Twitterati
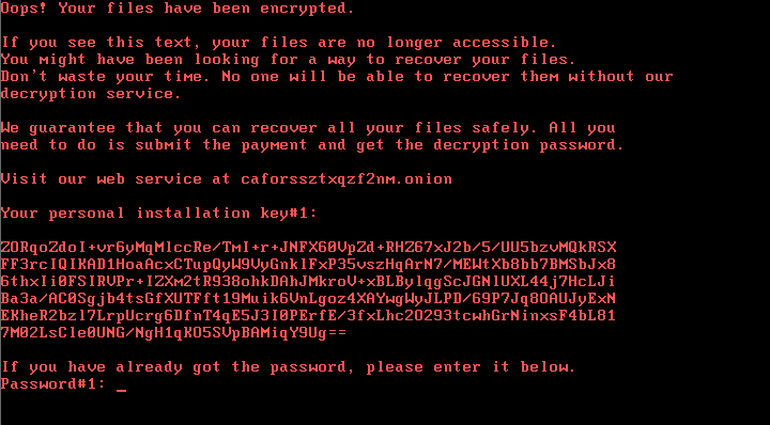
Ransom Note:
Impact:
- Confidential data held hostage.
- All targeted files and documents are encrypted with RSA 2048 encryption mechanism.
- Victim to pay a ransom of ~300$ in BitCoin.
- Users will be locked out of the computer.
How to prevent the attack:
- Disabling WMI service across the network can prevent ransomware from spreading.
- Always update software from vendors.
- Avoid surfing unknown websites.
- Check for valid signed certificates of any installers.
- As per ‘Cybereason‘ there is a quick prevention method available. For more info click here.
SecPod Saner detects this attack in real time. Download Saner now and keep your systems updated and secure.