Bluekeep is an exploit not unheard of. But, it is only in the recent times that an active exploitation of BlueKeep vulnerability has hit the headlines. Tracked as CVE-2019-0708, BlueKeep is a critical wormable remote code execution flaw in Remote Desktop Services that Microsoft patched in the May 2019 Patch Tuesday Updates. However, over 724,000 systems worldwide could still be unpatched and exposed to potential attacks. A patch management software patches vulnerabilities like bluekeep vulnerability.
A security researcher named Kevin Beaumont built a worldwide honeypot network named BluePot using Azure Sentinel with Microsoft Sysmon. Although no signs of attack were observed initially, late October saw a steep increase in the crashing and rebooting of honeypots. An analysis of the crashdump from one of the honeypots in Germany was carried out by KryptosLogic. They analyzed the pool allocations with the pool tag TSic, used by IcaAllocateChannel in the Windows RDP driver termdd.sys. The presence of thousands of allocations of size ‘0x170’ with TSic tag suggested an abnormal behavior.
Looking back at the BlueKeep exploit, an allocation of the exact size ‘0x170’ is required to fill a memory hole in the freed channel structure MS_T120 with a dangling pointer. Thousands of allocations also suggest the usage of heap spraying technique for exploitation. To gain Remote Code Execution, an attacker must hijack a pointer at offset 0x100 in the channel structure. This pointer indirectly links to a function which leads to the shellcode. The pointer dereferences the address fffffa80`08807048 which leads to the exploit payload. The researchers were able to match these parameters with the recent attack sample, indicating a Bluekeep exploit. The attackers had used the same shellcode with the user mode egg from the BlueKeep Metasploit module. To avoid such attacks, use a vulnerability management tool.
The payload was an encoded PowerShell command that the attacker used to download another PowerShell command from their server. The last stage involved executing a malicious binary, which connects to a cryptocurrency miner.
Microsoft did its part by working closely with the researchers to investigate the RDP exploits.
From early September, Microsoft actively protected its Microsoft Defender ATP customers well before attackers targeted the deployed honeypots. Microsoft Defender ATP collected a number of critical signals using behavioral detection for the BlueKeep Metasploit module. A close examination of the C2 servers and behavioral aspects of recent attacks indicated a connection of the BlueKeep exploitation with an ongoing coin mining campaign. The same coin miner payload has infected countries like France, Russia, Italy, Spain, Ukraine, Germany, the United Kingdom, etc.
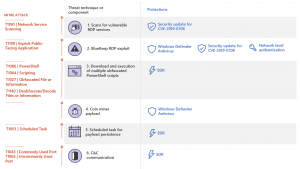 fig.BlueKeep exploitation techniques
fig.BlueKeep exploitation techniques
Image Credit: microsoft.com
According to Microsoft, bluekeep vulnerability attacks could have started off as a port scan for machines with vulnerable RDP services. The next step was to run a PowerShell script using the BlueKeep Metasploit module to download and launch other encoded PowerShell scripts. Apart from retrieving the coin miner payload, the final scripts also create scheduled tasks to achieve persistence on the infected machines. The attacker finally saves the coin miner as ‘C:\Windows\System32\spool\svchost.exe’ on the target.
There have been no reports of attacks involving malware or ransomware’s abusing BlueKeep. However, it is very likely that the attackers will sooner or later incorporate BlueKeep exploits in their modules only to leave behind devastating consequences.
Affected Products
Remote Desktop Services on :
- Windows 7
- Windows Server 2008
- Windows Server 2008 R2
- Windows Server 2003
- Windows Vista
- Windows XP
Impact
An unauthenticated attacker who connects to the target system using RDP and sends specially crafted requests can execute arbitrary code on the system
Solution
Microsoft has released a patch for this vulnerability (CVE-2019-0708) in May 2019 Patch Tuesday Updates. Strongly recommend applying the patches for CVE-2019-0708 on all internet facing systems with RDP without any further delay.
SecPod Saner detects this vulnerability and automatically fixes it by applying security updates. Download Saner now and keep your systems updated and secure.

