Image Source: pcworld
Ever wonder why your system running slower than usual, and how those annoying random messages pop up? or the newly added extensions in your browser, which you never used. The browser can’t load pages, internet connectivity is one thing but your computer is always slow. Those crashes that happen every now and then, that you have no idea of why???. Well, how about those extra toolbars with full of useless buttons and search boxes in your browser!!! Patch management tool can fix such problems.
Well speak of the devil, is it malware which is doing all of those things? is it your machine infected? Yes, you’re half way there to find out that your machine might have turned into a zombie controlled by C&C. A Vulnerability management software can stop your machines from getting affected.
It is botnet command and control server.
What is a Command and Control Server (C&C) ??
Botnet Command-and-control servers, also called C&C or C2, are used by attackers to maintain communications with compromised systems within a target network. These systems include Computers, Smartphones, and IoT’s, .
What is a zombie??
Zombie (Not a literal meaning!!!) is also called as a botnet (A term formed by combining the words robot and network) is the machine which is infected with a Trojan horse and being controlled by a C&C server. A botnet is a set of computers that are used without the knowledge of their owners to send files (including spam and malware’s ) to other computers over the Internet. Most of the affected systems are private computers.
Why communication is required?
Botnets follow specific instructions received from their C&C (Command and Control) to execute a set of commands based on the purpose and structure of the botnet. They install keyloggers to collect sensitive information, such as credit card numbers, send spam emails, or even assist in conducting DDoS attacks. Botnet’s are not just capable of uploading reports and results of commands to its C&C server. Botnet do what commander (C&C) tells them to do.
What’s a botnet command and control server architecture looks like? and How it works?
So, for what purpose these bots are used? Let’s just consider an example of spamming. When addresses that send spam are frequently blacklisted, the system automatically flags emails as spam. How to overcome this issue and still be able to send as many spams as possible? well thanks to the zombies, using thousands of unique addresses it will be a cup cake for attackers to send emails, and make huge money out of it.
Also considering the fact that C&C servers are much intended to conduct DDoS, things go like this, an army of zombies keeps sending a stream of false/dummy requests to the web servers continuously, and web server won’t be able to handle such huge multiple requests coming at a time leading to DDoS attack, criminals demands money from the owners in return of stopping such an attacks.
A botnet is also capable of creating a zombie army and installing a password stealing software. These software’s can steal passwords of email accounts, bank accounts, and credit card numbers, then criminals will sell this information to make money. The more the zombie army grows more the money attackers make by doing illegal activities.
Two Types of Botnet architecture:
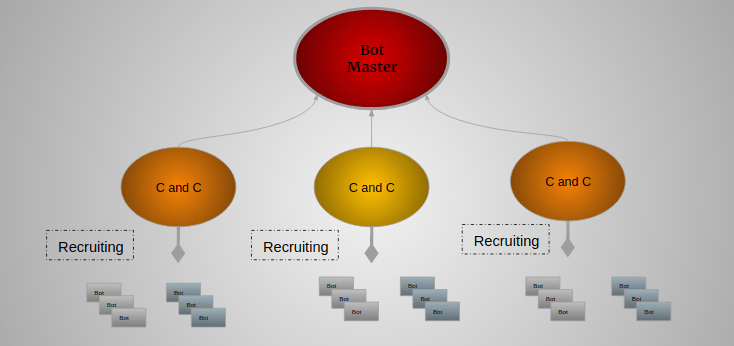
Typically, two types of architecture are either centralized around a C&C server or decentralized using peer-to-peer communication.
Centralized:
The most common and widespread type, which provides resources to individual clients’ requests, is centralized with a C&C server. This is a type of network based on client-server model. Typically these type of botnet communicates through Internet Relay Chat(IRC).
- IRC clients are computer programs that a user can install on his or her system.
- These clients communicate with chat servers to transfer messages to other clients.
- IRC networks use simple, low bandwidth communication methods, making them widely used to host botnets.
- They are relatively simple in construction and have used moderate success for coordinating DDoS attacks and spam campaigns while being able to switch channels to avoid being taken down continually.
Topologies used in centralized architecture are star, multi-server, and hierarchical.
Decentralized or Peer-to-Peer:
Despite using centralized servers have their own advantage. One problem with using centralized servers, which uses IRC is that each botnet client must know the IRC server, port, and its channel to be of any use to the botnet. Since Anti-malware organizations can detect and shut down these servers and channels, effectively halting the botnet attack. Bringing down a centralized server can leave the zombies dead. In term, botnet army is of no use to the attackers.
What are the infection methods?
So how do C&C recruit a botnet, or create an army of botnets? There are multiple ways of turning a computer into a botnet.
- Email: Attackers will send you emails with malicious code attached in a file, or a link to the website where a malicious code is hosted. opening these attachments or clicking on the links will lure the attackers to drop the malware within the machine which will turn it into a zombie.
- Exploiting Vulnerabilities: Multiple vulnerabilities when exploited will offer a backdoor to the machine’s, which will be used by attackers to drop the malware into the machine. Vulnerabilities that includes browser plugins, Add-ons, and any other software that are installed in the machine.
What to do, if your computer has turned into a zombie?
- Use some of the Sysinternals tools to find which process is consuming more memory, or look out for unknown and suspicious processes. If found kill all related process.
- It is always good to scan the machine with different antivirus engines and see whether it detects any malware, though it’s not a complete solution, up to some extent there are possibilities of identifying malware with latest antivirus signatures.
- Most of the antivirus would fail to detect and remove malware in case of most advanced malware, where it can link itself with operating system, process or registries.
- In case of rootkits its hard to remove the infection, the only and most effective way of cleaning the machine is to restore from backups or installing the OS or reverting to the older image. But before proceeding with this, beware of what you are going to lose. Make sure reverting back or restoring backup won’t cause much damage or result in loss of data.
- Once the system is clean from malware’s, apply security updates regularly to avoid future infections.
If just a tiny malware can cause a humongous damage. Then what about an army of botnet who can deliver and control these malware’s can cause!! Yes detecting and avoiding C&C communication is a necessity.
Implement basic security controls to detect and avoid systems becoming zombies:
An Organization may have thousands of machines infected by a botnet and controlled by a C&C. It will include anomalous network traffic or erratic performance of systems. Considering in an enterprise reducing the number of hosts used as zombies, or the amount of data sent out are using HTTP, HTTPS or other common protocols, attackers trying to reduce detection.
- Organizations can detect botnet infection on their networks using a set of network analysis and correlation with local system logs or investigations.
- The most effective detection method for a large, distributed network is to use a dedicated network appliance that has access to all Internet traffic in order to identify suspicious packets.
- Every machine should have modern anti malware software installed and updated regularly, ideally on an automated basis.
- Every machine should have basic hardening done, such as removing potentially unwanted programs and software, and should protect a host-based firewall, network firewall, or both.
- Despite of all the above things that need to be done. The emphasis should be on patching security updates which will aid in blocking attacks using unpatched software.
SanerNow keep your enterprise clean and secure from the attackers by providing all of the above security controls. Download Saner now and keep your systems updated and secure.

Informative