Management Engine also known as the Manageability Engine is an autonomous subsystem that has been built into all Intel CPU since 2008. And it has access to almost all information including network adapters, system memory etc, which, if exploited would allow complete compromise of vulnerable PCs, laptops, or servers. Intel ME firmware affected by multiple buffer overflow (CVE-2017-5705) vulnerabilities, which allow attackers with local access to execute arbitrary code on the targeted system. This component is also affected by multiple privilege escalation (CVE-2017-5708) vulnerabilities, which allows unauthorized process to access privileged content via unspecified vector.
Intel Server Platform Service in based on Intel ME, which allow remote configuration of Intel-powered servers over the network. Intel Server Platform Services affected by Multiple buffer overflow and privilege escalation vulnerabilities are found in the kernel (CVE-2017-5706, CVE-2017-5709).
Intel Trusted Execution Technology is a computer hardware technology assures that an authentic operating system starts in a trusted environment, which can then be considered trusted and verify the authenticity of a platform and its operating system. Intel TXE firmware is affected by multiple buffer overflow (CVE-2017-5707) vulnerabilities, which allow attackers with local access to execute arbitrary code on the targeted system. This component is also affected by multiple privilege escalation CVE-2017-5710) vulnerabilities, which allows unauthorized process to access privileged content via unspecified vector.
Impact:
These security vulnerabilities can be leveraged by logged-in users or malicious applications to extract confidential and protected information from the computer’s memory, potentially giving sensitive information passwords or cryptographic keys to trigger other attacks. The vulnerabilities can also be exploited by network administrators, or people masquerading as admins, to remotely infect machines with spyware and invisible rootkits, potentially. Most of these weaknesses are limited by the fact that it requires local access, either as an administrator or less privileged user; the rest require you to access the management features as an authenticated sysadmin.
Intel Security Vulnerability Summary:
Technology Affected : Intel Management Engine (ME)
Firmware versions : 11.0/11.5/11.6/11.7/11.10/11.20
CVE’s : CVE-2017-5705, CVE-2017-5708, CVE-2017-5711, CVE-2017-5712
Impact : Arbitrary Code Execution, Privilege Escalation
Technology Affected : Active Management Technology (AMT) for the Intel ME Firmware
Firmware versions : 8.x/9.x/10.x/11.0/11.5/11.6/11.7/11.10/11.20
CVE’s : CVE-2017-5711, CVE-2017-5712
Impact : Arbitrary Code Execution
Technology Affected : Server Platform Service
Firmware versions : 4.0.x.x
CVE’s : CVE-2017-5706, CVE-2017-5709
Impact : Arbitrary Code Execution, Privilege Escalation
Technology Affected : Intel Trusted Execution Engine
Firmware versions : 3.0.x.x
CVE’s : CVE-2017-5707, CVE-2017-5710
Impact : Arbitrary Code Execution, Privilege Escalation
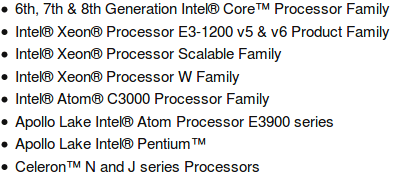
List of processor chip sets including the vulnerable firmware:
How To Detect System is Vulnerable:
Intel has published a detection tool to help users to check, if their systems are exposed to these vulnerabilities. Separate downloads are available for Window And Linux.
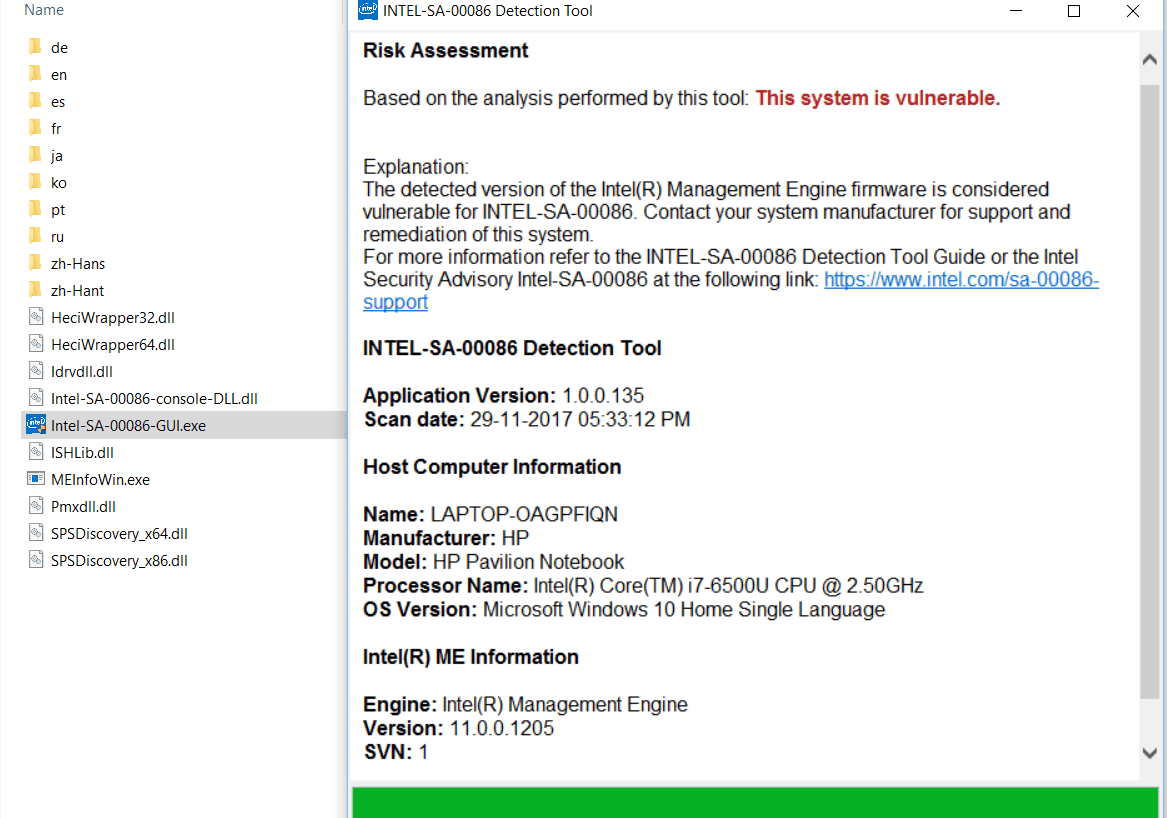
On Windows, download and run Intel-SA-00086-GUI.exe executable, which analyses Intel components on your local system and shows report saying your system is vulnerable or not as show in the below image.
The system is detected as vulnerable according to Intel-SA-00086 Detection tool. Here the Intel processor is having Intel ME with vulnerable firmware version (11.0.0.1205).
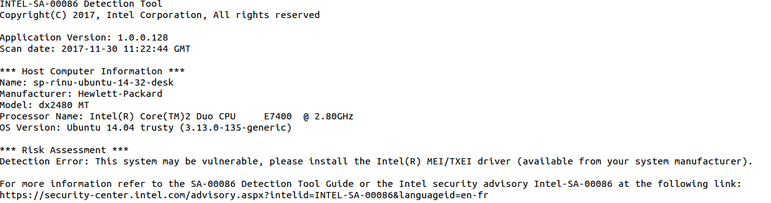
Similarly, On Linux download and run intel_sa00086.py python script, which analyses Intel components on your local system and shows report saying your system is vulnerable or not as show in the below image.
Solution:
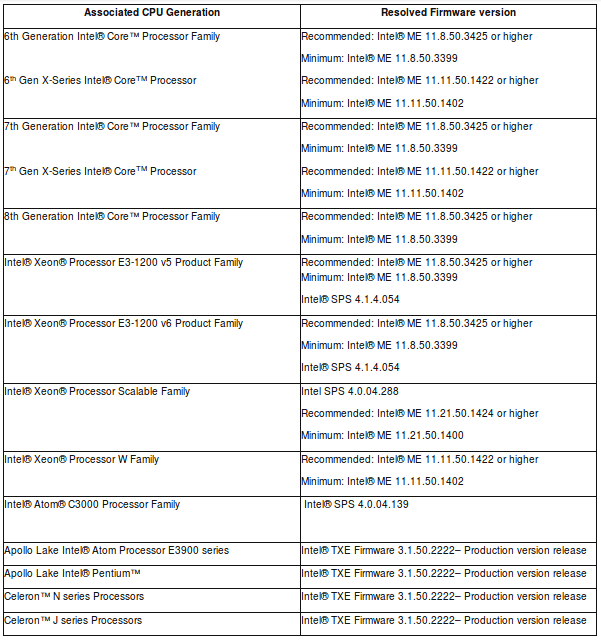
Intel recommend customers to update firmware versions on the impacted platforms as shown below: