A zero-day vulnerability (CVE-2014-1761) in Microsoft Word is being exploited in the wild, which was discovered by the Google security team. A good vulnerability management software can prevent these attacks.
A zero-day vulnerability (CVE-2014-1761) in Microsoft Word is being exploited in the wild, which was discovered by the Google security team. A good vulnerability management software can prevent these attacks.
The vulnerability triggers while parsing malicious Rich Text Format (RTF) content that can be of use to execute arbitrary code. Vulnerability management tool can resolve these issues.
According to Microsoft Security Advisory (2953095), vulnerability is present in Microsoft Word that can be of use to execute arbitrary code. Therefore, the flaw allows attackers to take complete control of the system.
An attack is present by convincing users to open specially crafted Rich Text Format (RTF) content using Microsoft Word or previews or through email messages in Microsoft Outlook.
According to Microsoft’s blog, the attack is in limit and very targeted in nature. The attacker included the component to bypass ASLR using Return Oriented Programming techniques and Egg Hunter techniques. However, To search and execute the main shellcode. After successful exploitation, the back door is dropping into the system. The drop backdoor is a generic malware in Visual Basic 6, which communicates over encrypted SSL traffic. To the C&C server @ IP: 185.12.44.51 Port: 443 and can install/run additional MSI components.
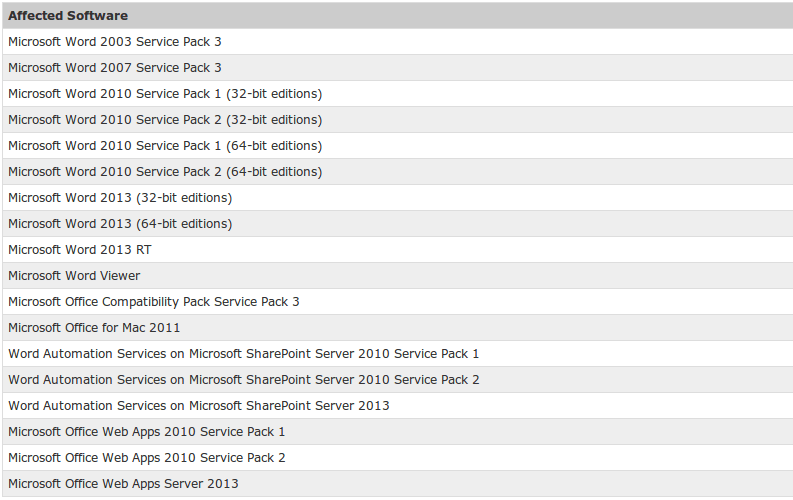
Affected Software list:
Microsoft is working on an official patch, and the release is in expectation for the upcoming Patch Tuesday. Meanwhile, Microsoft released a workaround, Fix an automated tool that disables the opening of Rich Text Format (RTF). Content in Microsoft Word to prevent the exploitation of this issue.
SanerNow will have the facility to fix this vulnerability soon after Microsoft presents the patch.
– Veerendra GG