Bar Mitzvah Attack, a critical vulnerability discovered in Rivest Cipher 4 software stream cipher. A vulnerability management tool can detect this attack. In cryptography, RC4 is one of the most used software-based stream ciphers in the world. Proper protocols such as Transport Layer Security (TLS) include the cipher.
It is a very simple cipher when compared to competing algorithms of the same strength and boasts one of the fastest speeds of the same family of algorithms. Experts estimate that it protects as much as 30% of SSL traffic. Though it is the most popular binary additive stream cipher, it suffers a long known (a 13-year-old vulnerability!!!) weakness known as Invariance Weakness. A vulnerability management software can prevent attacks such as the bar mitzvah.
From Mitre : “The RC4 algorithm, as used in the TLS protocol and SSL protocol, does not properly combine state data with key data during the initialization phase, which makes it easier for remote attackers to conduct plaintext-recovery attacks against the initial bytes of a stream by sniffing network traffic that occasionally relies on keys affected by the Invariance Weakness, and then using a brute-force approach involving LSB values, aka the “Bar Mitzvah” issue.”
TLS protocols use the above RC4 cipher, which means all Clients and Servers with RC4 cipher enabled are vulnerable.
How to check if RC4 is enabled in web browser to avoid Bar Mitzvah Attack?
Click here to check SSL cipher suite details of your browser, which will list RC4 in the cipher suite list if RC4 is enabled in your browser as show in the below picture.
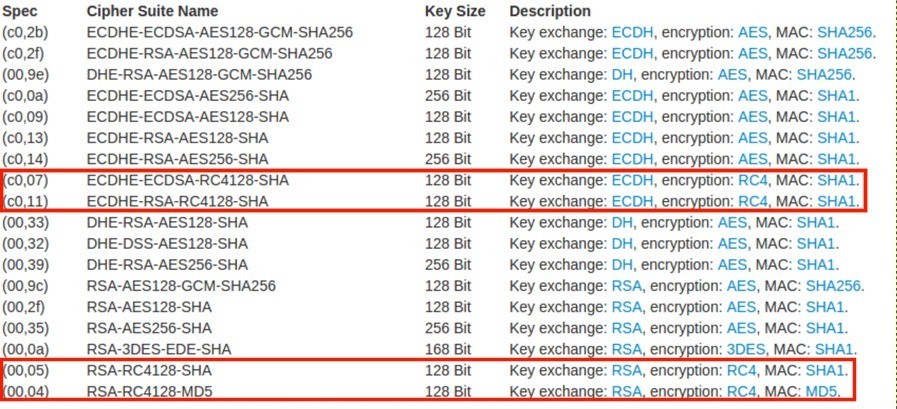
How to check if RC4 is enabled in web server ?
- Run the following openssl command (testing server is test_your_website.com):
openssl s_client -cipher RC4 -connect test_your_website.com:443
- Output of the above command:
Case 1
- : If RC4 is enabled in test_your_website.com, command should produce something like
.................. New, TLSv1/SSLv3, Cipher is ECDHE-RSA-RC4-SHA ................... Cipher : ECDHE-RSA-RC4-SHA ...................
Case 2
- : If RC4 is disabled in test_your_website.com, command should produce something like
140355035514528:error:14077410:SSL routines:SSL23_GET_SERVER_HELLO:sslv3 alert handshake failure:s23_clnt.c:770:

How to disable RC4?
- In Web Browsers:
Google Chrome and Opera:
To disable RC4 cipher in Google chrome and Opera you will have to start those applications with the following parameters:
–cipher-suite-blacklist=0x0005,0x0004,0x002f,0xc012,0xc011,0x003c,0xc011,0x0032,0xc007,0xc00c
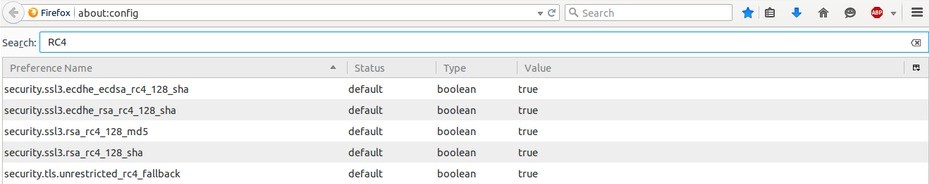
Mozilla Firefox:
-
- Open configuration page by typing
about:configin the address bar of Mozilla Firefox. - Enter RC4 in ‘Search’ bar.
- As search result you see the various cipher combinations that use this encryption standard. Double-click on each lines to toggle them from “true” to “false”.
- Open configuration page by typing
Internet Explorer:
- The RC4 cipher can be completely disabled on Windows platforms by setting the
“Enabled”
00000000
- in the following registry locations:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 128/128
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 40/128
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 56/128
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Ciphers\RC4 64/128
- In Web Servers:
Apache:
:!RC4:
SSLCipherSuite
SSLCipherSuite HIGH:!aNULL:!eNULL:!EXPORT:!DES:!MD5:!PSK:!RC4:!SSLv2
Microsoft Internet Information Server:
JBoss:
Update your conf/jboss-service.xml to disable RC4 cipher. You have to remove RC4 cipher from cipher suite list
<Connector port="8443" address="${jboss.bind.address}"
maxThreads="150" strategy="ms" maxHttpHeaderSize="8192"
emptySessionPath="true"
scheme="https" secure="true" clientAuth="false"
sslProtocol = "TLS"
keystoreFile="${jboss.server.home.dir}/conf/keystore/yourkeystore.keystore"
keystorePass="your-keystore-password"
protocol="HTTP/1.1"
ciphers="SSL_DHE_DSS_WITH_RC4_128_SHA,
SSL_DH_anon_WITH_RC4_128_MD5,
SSL_RSA_WITH_RC4_128_MD5,
SSL_RSA_WITH_RC4_128_SHA,
TLS_DHE_DSS_WITH_AES_128_CBC_SHA,
TLS_DHE_DSS_WITH_AES_256_CBC_SHA,
TLS_DHE_RSA_WITH_AES_128_CBC_SHA,
TLS_DHE_RSA_WITH_AES_256_CBC_SHA,
TLS_DH_anon_WITH_AES_128_CBC_SHA,
TLS_DH_anon_WITH_AES_256_CBC_SHA,
TLS_KRB5_WITH_RC4_128_MD5,
TLS_KRB5_WITH_RC4_128_SHA,
TLS_RSA_WITH_AES_128_CBC_SHA,
TLS_RSA_WITH_AES_256_CBC_SHA"
SSLEnabled="true">
</Connector>
We strongly suggest configuring your web server and browser as shown above to avoid attacks such as the Bar Mitzvah Attack.
However, SanerNow detects these vulnerabilities. Moreover, download SanerNow and keep your systems updated and secure.
– Kumarswamy S

Hi there to every one, the contents present at this site
are actually remarkable for people knowledge, well, keep up the good work fellows.
Thank You