DarkIRC is a multi-featured botnet. The bot comes with a variety of capabilities like keylogging, the ability to download files and execute commands on the infected server, steal credentials, spread to other devices via MSSQL and RDP (brute force), SMB, or USB, as well as perform several versions of DDoS attacks. A vulnerability management solution can mitigate this.
The botnet also has anti-sandbox and anti-detection techniques which allow it to check if the server is running any virtual environments, including those from VMware, VirtualBox, VBox, QEMU and, Xen before deploying the final malware. The attack stopped if any of these is detected otherwise the malware is unpacked and installed in a Chrome file to help maintain persistence. It also achieves persistence by creating an autorun entry, cron jobs, kill competing mining tools, and even uninstall Endpoint detection and response (EDR) tools. Auto patching can stop these attacks.
The bot also acts as a bitcoin clipper by changing bitcoin wallet addresses copied to the clipboard to one controlled by its operators in real-time to reroute Bitcoin transactions. It also performs a unique command and control domain generation algorithm. This relies on the sent value of a particular crypto wallet. Also, DarkIRC is being sold on hack forums by the name of Freak_OG, which is to be the threat actor behind this botnet.
Description
Malware Capabilities
- Anti-sandboxing and Anti-analysis functions
- Launching several versions of distributed denial of service attacks.
- Download Files and Execute Commands
- Worm or spread itself in the network
- Browser Stealer
- Keylogging
- Achieves persistence on the compromised device
Malware Infection Methods
WebLogic flaw (CVE-2020-14882): DarkIRC botnet is actively targeting thousands of Oracle WebLogic servers to exploit a critical vulnerability, which allows unauthenticated remote code execution. Oracle WebLogic Server is a platform for developing, deploying, and running enterprise Java applications in any cloud environment as well as on-premises. The flaw, dubbed CVE-2020-14882 affects WebLogic Server versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0, and 14.1.1.0.0. Thousands of unpatched Oracle WebLogic servers are accessible on the Internet. The malware is delivered on vulnerable systems by sending a simple HTTP GET request and using a PowerShell script. DarkIRC botnet attackers are exploiting this critical flaw to steal credentials, execute arbitrary commands on compromised machines, spread laterally across the network, download files and record keystrokes.
SanerNow lists the potential targets for malware in an enterprise network (shown in the figures below).
[contact-form][contact-field label=”Name” type=”name” required=”true” /][contact-field label=”Email” type=”email” required=”true” /][contact-field label=”Website” type=”url” /][contact-field label=”Message” type=”textarea” /][/contact-form]
Fig1. SanerNow listing of potential targets in an organization for DarkIRC Malware
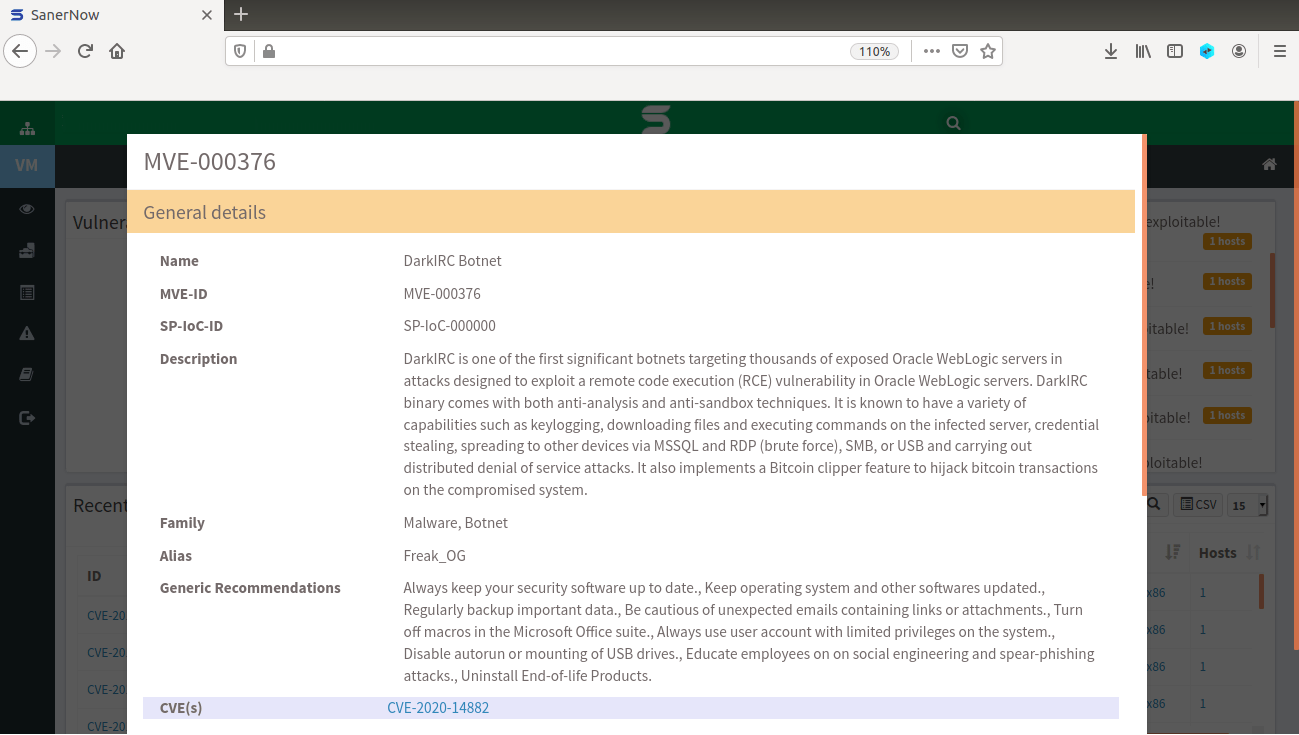 Fig2. Details about DarkIRC Malware
Fig2. Details about DarkIRC Malware
SanerNow detects the vulnerability used as infection vectors for spreading DarkIRC Malware. Download SanerNow and keep your systems updated and secure.
General Recommendations
1) Keep your systems up-to-date with the latest security patches.
2) Use strong and complex passwords.
3) Refrain from opening any suspicious emails or links.
4) Manage network shares and disable anonymous logins.

