While the digital realm brings convenience and connectivity, it also introduces a bunch of vulnerabilities that can compromise the security and integrity of systems. As the number of unpatched vulnerabilities continues to rise, IT Security teams find themselves struggling with the task of securing their digital assets. With millions of vulnerabilities to address, it can be challenging to know where to start. Moreover, in this article, we will explore the challenges faced by IT Security Teams in handling the number of vulnerabilities and discuss effective strategies for prioritizing and addressing them.
The Mountainous Challenge of Keeping Unpatched Vulnerabilities Near-Zero
The immense growth of technology has given rise to an overwhelming number of vulnerabilities in software, networks, and systems. However, cyber attackers are quick to exploit these weaknesses, making it essential for individuals and organizations to stay ahead of the curve in terms of cybersecurity. Moreover, the sheer volume of vulnerabilities can be paralyzing, leading to a sense of helplessness and indecision.
- Vulnerability Overload: With the increasing complexity of software and the interconnectivity of devices, the number of potential vulnerabilities has skyrocketed. From outdated software to misconfigured systems, the attack surface has expanded, leaving a wide array of entry points for malicious attacks. Also, improper remediation plans end up resulting in huge vulnerability backlogs, which act as a blocker in effective cyberattack prevention.
- Resource Constraints: Many organizations, especially smaller ones, face resource constraints when it comes to cybersecurity. Limited budgets, inadequate personnel, and a lack of awareness contribute to the challenge of dealing with a multitude of vulnerabilities effectively.
Where Do We Start, and What’s the Mantra for Reducing Vulnerability Counts to Near-Zero?
While it may seem like an impossible task, managing a million vulnerabilities begins with a systematic and strategic approach using the Continuous Vulnerability and Exposure Management (CVEM) Framework. Here are key steps to help navigate this complex landscape:
The first step in dealing with a million unpatched vulnerabilities is to conduct regular vulnerability scans and cybersecurity.
- Daily Risk Assessment:
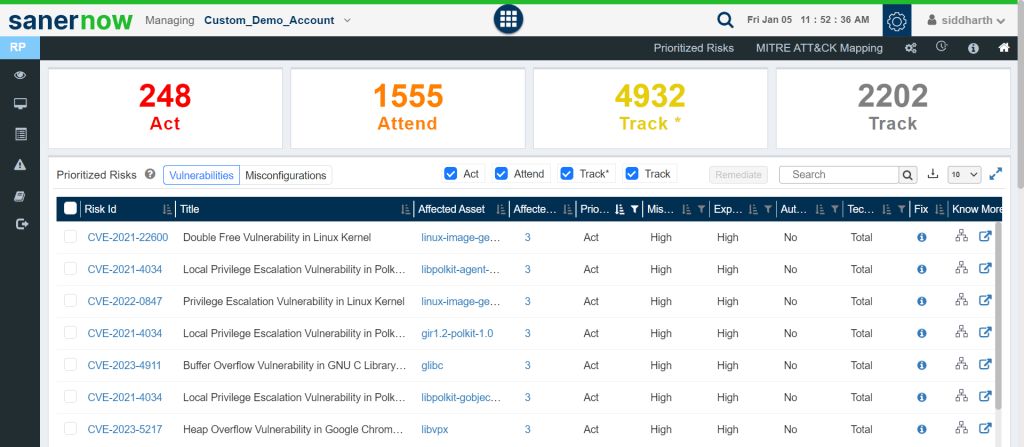
Conduct a thorough risk assessment to identify and prioritize vulnerabilities based on their potential impact on your business. Not all vulnerabilities are created equal, and understanding the specific risks to your assets is crucial in developing an effective mitigation plan. - Comprehensive Asset Inventory:
Create an inventory of your digital assets. Knowing what you have, where it is located, and its importance to your operations. It allows you to focus on securing critical components first. Also, this step is fundamental in understanding vulnerabilities’ scope and potential impact. - Integrated Patch Management:
Regularly update and patch software and systems. Many vulnerabilities arise from outdated software versions or unpatched systems. Implement a robust patch management strategy to stay current with security updates and minimize exposure to known vulnerabilities. - Prioritizing Vulnerabilities for a Sleek Remediation Plan:
Prioritizing vulnerabilities is crucial for efficient resource allocation and prompt remediation of the most crucial security gaps. Leverage vulnerability prioritization frameworks such as the Common Vulnerability Scoring System (CVSS) to assess and rank vulnerabilities based on severity. This allows you to promptly address the most critical issues, mitigating the highest risk first. - Workshops for User Education and Awareness:
Often overlooked, user education is a critical component of cybersecurity. Train employees and users to recognize and report potential security threats. Also, human error remains a significant factor in cyber incidents, and an informed user base can act as an additional layer of defense. - Continuous Monitoring of the entire framework:
Implement continuous monitoring tools and practices to detect and respond to vulnerabilities in real time. Also, automated solutions can help identify and remediate issues promptly, reducing the window of opportunity for attackers.
Conclusion
Dealing with a million vulnerabilities is a monumental task, but it becomes manageable with a continuous strategic and proactive approach. By conducting continuous risk assessments, prioritizing based on severity, and then implementing robust cybersecurity practices, IT Security teams can uplift their defences against the ever-growing threat landscape. While the challenge may persist, a well-informed and adaptive cybersecurity strategy will empower IT Security teams to navigate the complexities of the digital world securely.