Dirty COW vulnerability(CVE-2016-5195) is a privilege escalation in the Linux Kernel, which allows an unprivileged local user to gain write access to otherwise read-only memory mappings. Thus increases their privileges on the system. Vulnerability management tool are essential to detect such critical vulnerabilities.
The caused issue is by a race condition in the way kernel handles copy-on-write(COW), an optimization strategy used in computer programming. Therefore, nicknamed Dirty COW vulnerability. The fundamental idea is that if multiple callers ask for resources which are initially indistinguishable, you can give them pointers to the same resource. This function can maintain its behavior until a caller tries to modify its “copy” of the resource. At that point, the system creates a true private copy to prevent the changes from becoming visible to everyone else. However, the broken copy-on-write implementation can lead programs to end up in a race condition, enabling a non-privileged user to alter root-owned files and setuid executables.
Dirty Cow Vulnerability affects Linux kernel versions since 2.6.22. A detection script can be employed to determine vulnerable kernel versions on Red Hat Enterprise Linux and CentOS. Linux kernel versions 4.8.3, 4.7.9, and 4.4.26 address the vulnerability. Patches have been released by Ubuntu, Redhat and Debian to mitigate the issue. Deploy these patches instantly with a good patch management software.
Proof of concept in detail:
Trying PoC (Kernel crash) on a Centos 7 Operating System:
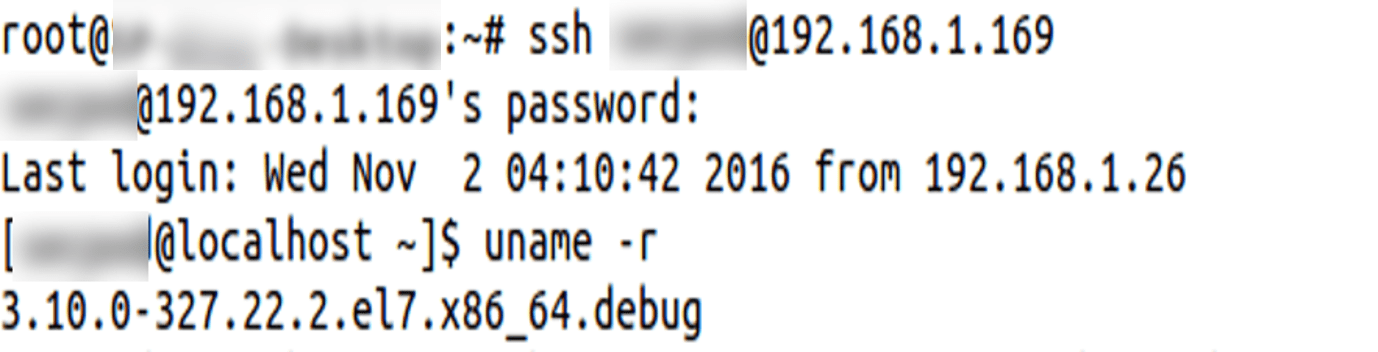
- Checking whether the Centos 7 kernel version is vulnerable to Dirty COW or not (Linux kernel version since 2.6.22)
Found the vulnerable kernel version.
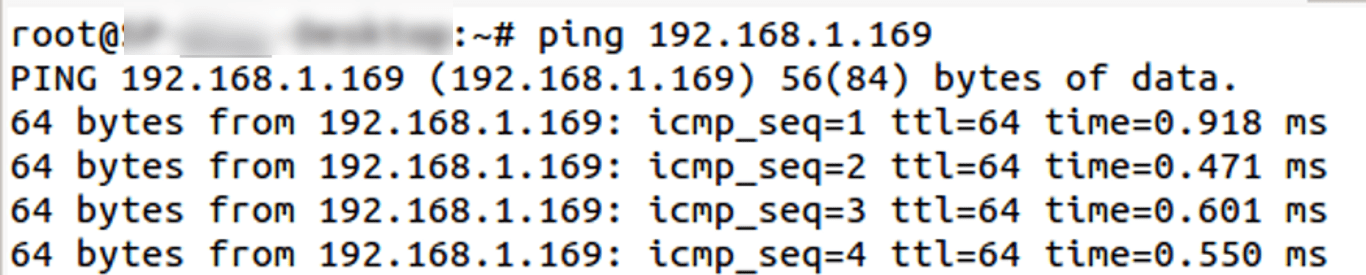
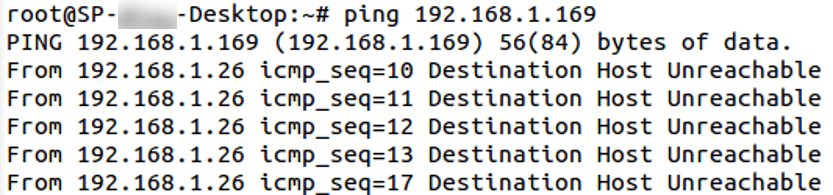
- Ping result to the above machine before trying dirty cow PoC
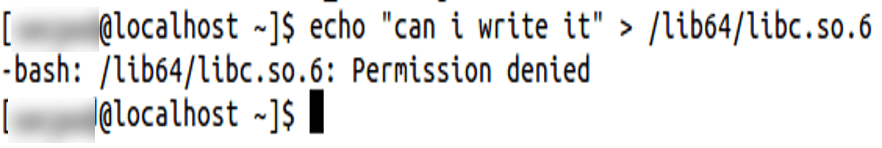
- Logged in as a local user and trying to write to a file, for which user has only read permission
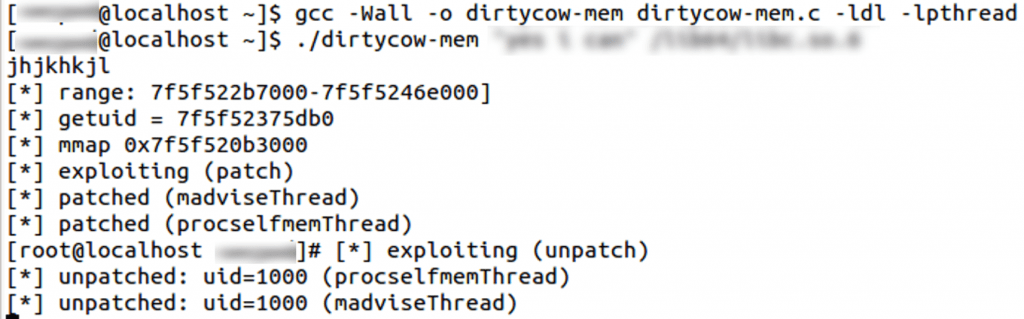
- Running the Dirty Cow Vulnerability PoC on Centos 7 as a local user, which is trying to write to the above-mentioned file and it results in kernel crash after few minutes. The PoC (dirtycow-mem.c) used here is sourced from https://github.com/dirtycow/dirtycow.github.io/blob/master/dirtyc0w.c. For more PoC’s, refer https://github.com/dirtycow/dirtycow.github.io/wiki/PoCs
- Ping result to the above machine after trying running PoC
Kernel crashed, which confirms the PoC worked.

How the PoC works?
- Here, the program opens a root-owned executable file in read-only mode.
- The program calls the mmap function, which maps the file into a new memory area. The permission flag indicates that the mapped file is read-only, and the map_private flag enables the copy-on-write mechanism. The mechanism ensures that it provides a single shared copy of the same data to everyone until someone writes to it. At that point, it makes a copy.
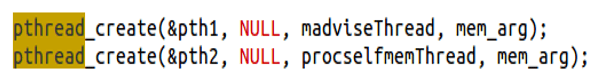
- Next, you start 2 threads that run in parallel. Dirty cow is a race condition on ability, certain events have to occur in a particular order. Here both threads are “racing” to access/change the data.
- The madwiseThread repeatedly calls the madvise function on that mapping with the advice value MADV_DONTNEED set. Informing the kernel that the memory area mapped to the file will probably not be needed soon or will not expect access in the near future allows the kernel to free resources associated with it. The application’s completion with the given range is the reason for freeing resources associated with it.
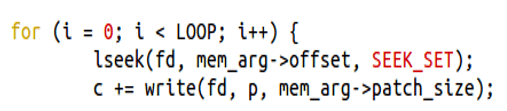
- procselfmemThread opens a special file /proc/self/mem with read-write access which is the representation of the current process memory. Using normal seek and write operations, you repeatedly overwrite part of the memory that’s mapped to the root-owned executable. The overwrite shouldn’t affect the executable on disk.
- Due to the race condition issue, repeatedly attempting these actions (using the madvise function to tell the kernel to discard the pages holding the mapped area and calling this while writing to /proc/self/mem) will eventually result in an inconsistent state. In this state, the kernel removes the pages holding the mapped executable, and it attempts to write to the memory area. The kernel commits these changes to storage.
Impact of Dirty COW vulnerability:
The Dirty COW vulnerability allows an unprivileged local user to modify files, bypassing the standard permission mechanisms thus leading to privilege escalation on the system. Once the attacker has control over the system as a normal user, he can use an exploit which uses this vulnerability to gain full control of a Linux system and can install malware and steal data etc.
And another problem with Dirty COW vulnerability is that it is almost impossible to detect by Antivirus or any security software and no evidence left for the actions taken. The real risk of vulnerability is when user-level access, as well as code execution ability, exists on the device.
However, SanerNow detects these vulnerabilities and automatically fixes them by applying security updates. Furthermore, download SanerNow and keep your systems updated and secure.