Discourse is one of the most popular open-source community forums and mailing list management software applications. A critical code execution vulnerability (CVE-2021-41163) identifies in Discourse, allows an attacker to execute arbitrary code on the affected system. This vulnerability recognizes with CVE-2021-41163. A good Vulnerability Management Tool can prevent these attacks.
The NIST doesn’t calculate the severity score, but this flaw is considering as Critical severity as it allows unauthenticated RCE on the affecting systems. Due to the widespread use of Discourse, CISA (Certified Information Systems Auditor) has also published an alert asking administrators to update Discourse to the latest patched versions. Vulnerability Management System can resolve these issues. It also boosts your organization’s cyber security defense, hence keeping your organization safe and secure from all forms of threats.
Vulnerability Details
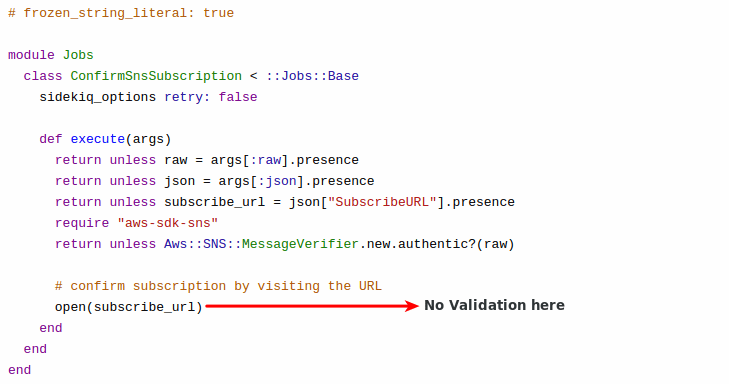
The vulnerability lies in the AWS notification webhook handler due to a validation bug in subscribe_url as shown below. It does not require any authentication and can be triggered by an attacker using https://somedicourseinstance/webhooks/aws request.
A PoC code is also available for this vulnerability. It is on the same factor where attacker-supplies input passes to the open() function leading to OS command execution.
Affected products by CVE-2021-41163
Discourse stable versions 2.7.8 and prior.
Impact of CVE-2021-41163
Successful exploitation of this vulnerability allows an attacker to execute arbitrary code on the affected system.
Solution for CVE-2021-41163
The vendor has released a patch for this vulnerability. It fixed in Discourse stable version 2.7.9 and later. If updating Discourse is not possible, users are advised to block requests with a path starting /webhooks/aws using some additional security tools.
SanerNow VM detects these vulnerabilities. We strongly recommend applying the security updates for this vulnerability on high priority.