Welcome back to another episode of “The Story Behind a Cyberattack.” In this episode, we will explore a ransomware attack that occurred in 2017.
This ransomware attack mostly targeted Microsoft operating system users. It held their sensitive data and demanded a ransom in return.
If not guessed already, let’s now know the story behind WannaCry.
What is WannaCry?
WannaCry is a type of ransomware that targets Windows operating systems. It encrypts users’ files and demands payment in Bitcoin to unlock them. The attack leveraged a vulnerability in the Windows SMB (Server Message Block) protocol, allowing it to spread rapidly across networks.
This worm is also known as WannaCrypt, Wana Decrypt0r 2.0, WanaCrypt0r 2.0, and Wanna Decryptor. It is often called a worm due to its ability of transport mechanism to automatically spread itself.
Let’s dive deep and understand the story behind it.
How was WannaCry Discovered?
WannaCry first made headlines on May 12th, 2017. This worm targeted over 200,000 Windows OSs across 150 countries and used the eternal blue exploit to gain access to vulnerable systems.
Eternal Blue was an exploit developed by the US National Security Agency (NSA). It was based on a vulnerability in Windows that allowed users to gain access to any number of devices in the network. Later, the NSA discovered that Eternal Blue was stolen by a group of hackers known as Shadow Brokers.
Microsoft eventually found the vulnerability, and on Tuesday, 14th May 2017, it released a security patch for all Windows versions supported at that time. In the meantime, on May 15, a security researcher named Marcus Hutchins discovered a “kill switch” in the ransomware’s code, which allowed him to temporarily halt its spread.
The kill switch is known by multiple names: emergency stop (E-STOP), emergency brake, emergency off, or emergency power off. It is used to shut down a machine in case of emergency if it can’t be shut down normally. In the case of WannaCry, the kill switch was used to stop the affected system to further spread the risks across other devices.
According to reports, millions of devices and enterprises were attacked, causing total damage ranging from hundreds to thousands to millions of dollars. It was also rumored that North Korea or agencies working in the country were behind this attack.
In December 2017, the United Kingdom and the United States formally declared North Korea involved, but they denied any involvement related to the attack.
Can WannaCry really be fixed?
Experts quickly advised all the affected users not to pay the ransom since there are no records of users getting the data back. As of June 14th, 2017, after the attack was halted, 327 payments were made, totalling US$130,634.77, which has been transferred.
Microsoft released a security patch in February, but it was only available to those who paid for a custom support plan. Later, it was made available to everyone for both supported and outdated operating systems.
Microsoft’s Cyber Defense Operations Center, Adrienne Hall, said, “Due to the elevated risk for destructive cyber-attacks at this time, we made the decision to take this action because applying these updates provides further protection against potential attacks with characteristics similar to WannaCrypt [alternative name to WannaCry]”
Enterprises that constantly update their network and follow the strategy will not be affected by this WannaCry. Below are a few practices you can implement in your enterprise cybersecurity plan.
How to avoid attacks like WannaCry?
While the impact of WannaCry was severe, its lessons taught enterprises valuable strategies for future prevention. Here are key steps to protect against ransomware:
- Regular Updates: It is crucial to ensure that all devices/systems are up to date with the latest security patches.
- Backup Data: Regularly backing up data can help enterprises recover without paying ransoms.
- Employee Training: Educating staff about phishing attacks and safe browsing practices can reduce the impact of risk
- Limit User Privileges: Restrict user access rights to only what is necessary. This minimizes the potential data loss, and all devices being targeted
- Implement Multi-Factor Authentication (MFA): Adding an extra layer of security can protect accounts from unauthorized access, especially if credentials are compromised
- Conduct Regular Security Audits: Perform assessments of your systems to identify vulnerabilities, misconfigurations, exposures, and other weaknesses in your security posture.
Detecting WannaCry with SanerNow
SanerNow Continuous Vulnerability and Exposure Management (CVEM) tool can help enterprises proactively defend against threats like WannaCry by detecting, assessing, prioritizing, and remediating vulnerabilities in real time. Here’s how:
1. Asset Coverage: SanerNow provides comprehensive visibility into all hardware and software across the network, ensuring no asset is left unmonitored.
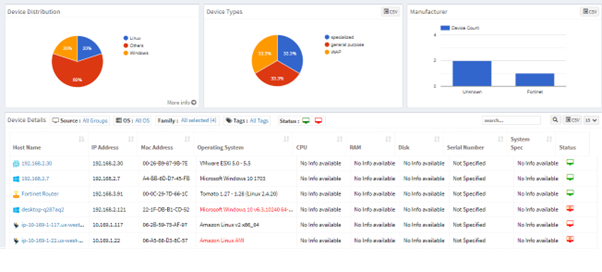
2. Continuous Monitoring: It automatically scans devices for vulnerabilities, misconfigurations, exposures, anomalies, and other security risks, allowing for immediate response.
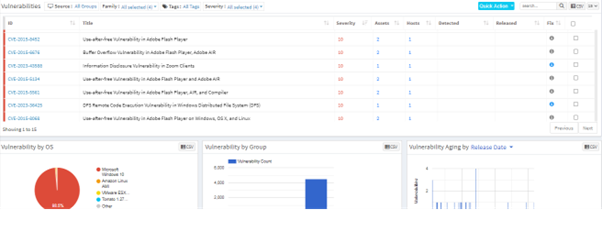
3. Prioritize Risks: SanerNow uses advanced algorithms to prioritize detected risks based on severity, CVSS score, technical impact, and business context, ensuring critical issues are addressed first.
4. Instant Patching: The tool supports integrated patch management for major operating systems and thousands of third-party applications, minimizing the window of exposure.
WannaCry was a wake-up call for enterprises worldwide, highlighting the importance of cybersecurity vigilance. By adopting proactive measures and leveraging tools like SanerNow, businesses can bolster their defenses against future cyber threats.
Stay tuned for our next episode, where we’ll dive into another compelling cyberattack story!

