The Blackhats have created a new strain of malware that targets the same vulnerability as the WannaCry ransomware from the first week of May. However, these targeted vulnerabilities can be patched using auto patching.
The Malware is called as EternalRocks, which uses the same flaw in Microsoft’s SMB networking protocol to infect other Windows systems that haven’t yet been patched with MS17-010. However, this new malware is far deadlier than WannaCry. Thus, Vulnerability Management solution can keep these attacks at bay.
WannaCry Ransomware created havoc and tensions around the globe in the first half of May 2017. However, this ransomware just used 2 NSA hacking Tools ETERNALBLUE to compromise a machine and DOUBLEPULSAR to move around the network to find its victim and infect. Hence, Vulnerability Management Tools can resolve these issues. Discovery of this new worm is spreading via SMB.
It uses 7 NSA hacking tools which are leaked by a mysterious group calling themselves Shadow Brokers:
- EternalBlue — SMBv1 exploit tool
- EternalRomance — SMBv1 exploit tool
- EternalChampion — SMBv2 exploit tool
- EternalSynergy — SMBv3 exploit tool
- SMBTouch — SMB reconnaissance tool
- ArchTouch — SMB reconnaissance tool
- DoublePulsar — Backdoor Trojan
ETERNALBLUE, ETERNAL CHAMPION, ETERNAL ROMANCE, and ETERNALSYNERGY, which are SMB exploits used to compromise vulnerable computers, while SMBTOUCH and ARCHITOUCH are two NSA tools used for SMB reconnaissance operations are used to scan for active SMB ports.
EternalRocks malware fakes itself as WannaCry to fool security researchers, but instead of dropping ransomware and encrypting the user files, it gains unauthorized control of the affected computer to launch future cyber attacks. The victim is always prey for attacks until the malware is found and taken required steps to eradicate such threats.
Now let’s see how the attack takes place
Infection of EternalRocks malware takes place in two stages.
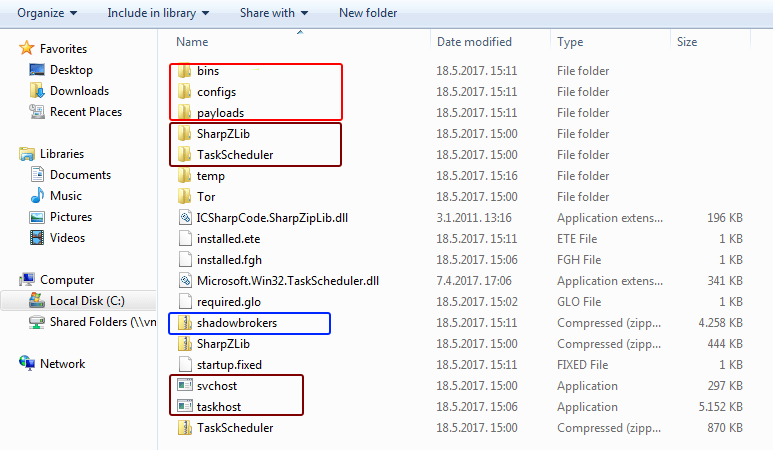
In the first stage, malware entering a machine downloads necessary .NET components TaskScheduler and SharpZLib from the internet while dropping svchost.exe and taskhost.exe. Component svchost.exe used for downloading, unpacking, and running Tor from archive.torproject.org along with C&C (ubgdgno5eswkhmpy.onion) communication requesting further instructions.
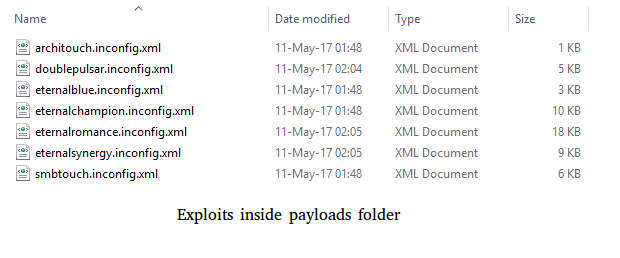
After infection, in the second stage, the malware taskhost.exe downloads after a predefined period (usually 24hrs) from http://ubgdgno5eswkhmpy.onion/updates/download?id=PC and execute. After initial execution, it drops a bunch of exploits through shadowbrokers.zip and unpacks the directories payloads/, configs/, and bins/. It starts a random scan of opened 445 (SMB) ports on the internet while running contained exploits (available inside bins/) and pushing the first-stage malware through payloads (inside payloads/ – shown in the image below). Also, it expects running the Tor process from the first stage to get further instructions from C&C.
Once compromised with ETERNALROCKS the system can be used for any future attacks. It may cause damage beyond imagination. Saner will detect this threat easily.
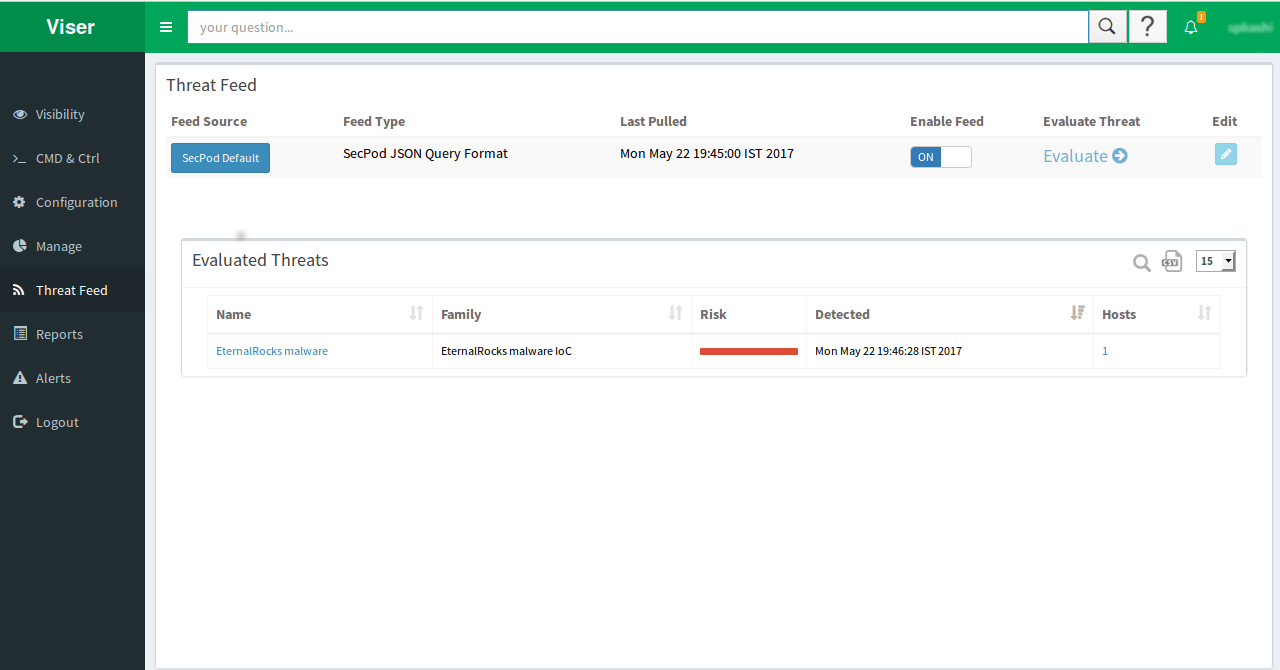
Saner caught this malware with Indicators (as seen in the image below).
The threats are detected in Viser.
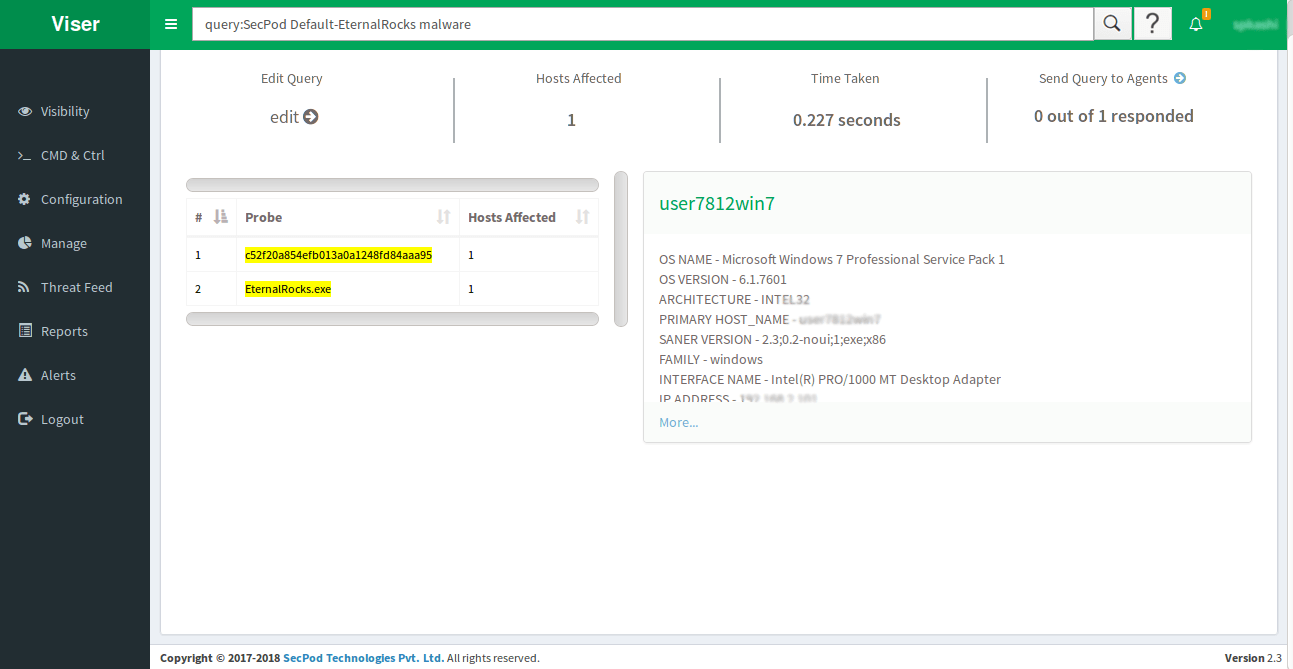
EternalRocks can be weaponized instantly. Because of its larger exploit arsenal, the lack of detection and remediation, and because of its initial inactive state, EternalRocks could pose a serious threat to computers with vulnerable SMB ports exposed to the Internet, if its author would ever decide to weaponize the worm with ransomware, a banking trojan, RATs, or anything else.
Few of the exploits used by the NSA Hacking tools are already fixed in older Microsoft Patch updates
| Code Name | Solution |
| “EternalBlue” | Addressed by MS17-010 |
| “EmeraldThread” | Addressed by MS10-061 |
| “EternalChampion” | Addressed by CVE-2017-0146 & CVE-2017-0147 |
| “ErraticGopher” | Addressed prior to the release of Windows Vista |
| “EsikmoRoll” | Addressed by MS14-068 |
| “EternalRomance” | Addressed by MS17-010 |
| “EducatedScholar” | Addressed by MS09-050 |
| “EternalSynergy” | Addressed by MS17-010 |
| “EclipsedWing” | Addressed by MS08-067 |
source: Microsoft
Easy remediation of these issues is possible via SecPod Saner. Install Saner to detect these type of threats and stay secure.