In any organization, employees rely heavily on their devices to carry out their tasks efficiently. With legitimate applications and services, there is always a risk of unwanted applications and unique services running on employees’ systems.
These will present significant challenges and potential threats to an organization’s IT infrastructure. They can compromise the confidentiality, integrity, and availability of sensitive data and systems, leading to financial losses, reputational damage, and legal implications.
Let’s dive into the article and learn about vulnerabilities caused due to unwanted applications and services and a few real-time incidents. A vulnerability management tool will help make this process easier.
Vulnerabilities Due to Unwanted Applications and Unique Services
Unwanted applications and unauthorized services can introduce several vulnerabilities to a system or Organization’s network, potentially compromising its security. Here are some common vulnerabilities associated with unwanted applications and services:
a. Malware Infections:
Unwanted applications, particularly those obtained from untrusted sources, can contain malware such as viruses, Trojans, ransomware, or spyware. Once installed, these malware can exploit system vulnerabilities, compromise data integrity, steal sensitive information, or allow unauthorized access to the system.
b. Remote Access:
Certain unauthorized services may create hidden entry points or enable remote access to a system. Malicious actors can exploit these backdoors to gain unauthorized access, bypass security measures, and carry out malicious activities without detection.
c. Network Exploitation:
Illegal services running on a network can create additional entry points for attackers. Hackers can target these services if they have known vulnerabilities or if they are not properly patched, in order to gain access to the network and compromise other systems or sensitive data.
d. Resource Exhaustion:
Unauthorized services may consume excessive system resources, such as CPU, memory, or network bandwidth. This can lead to degraded system performance, affecting productivity and potentially causing service disruptions for legitimate users.
e. Lack of Security Updates:
Unwanted applications or unauthorized services typically don’t receive security updates or patches. This leaves them vulnerable to known exploits, making the system an easy target for attackers who can take advantage of these unpatched vulnerabilities.
Identify Unwanted Applications and Unique Services Through SanerNow
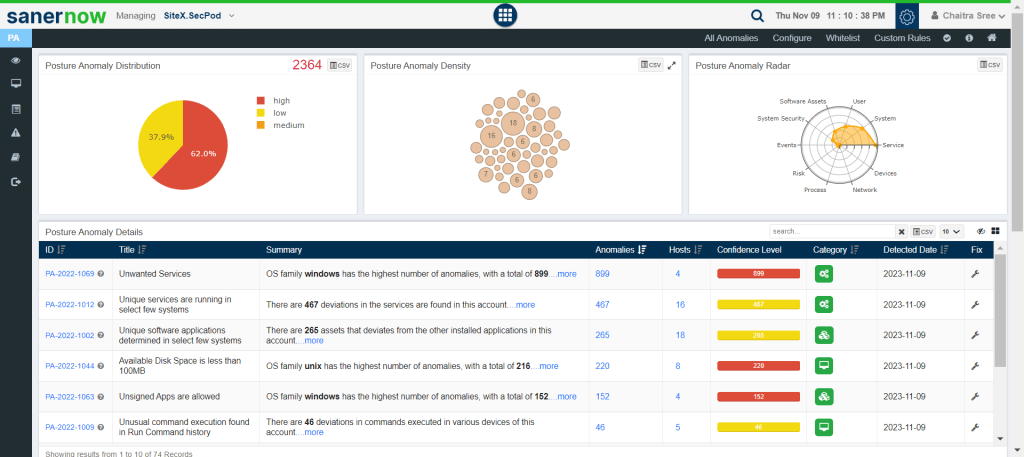
SanerNow Continuous Posture anomaly management helps you detect unwanted and unique services seamlessly with just a click of a button.
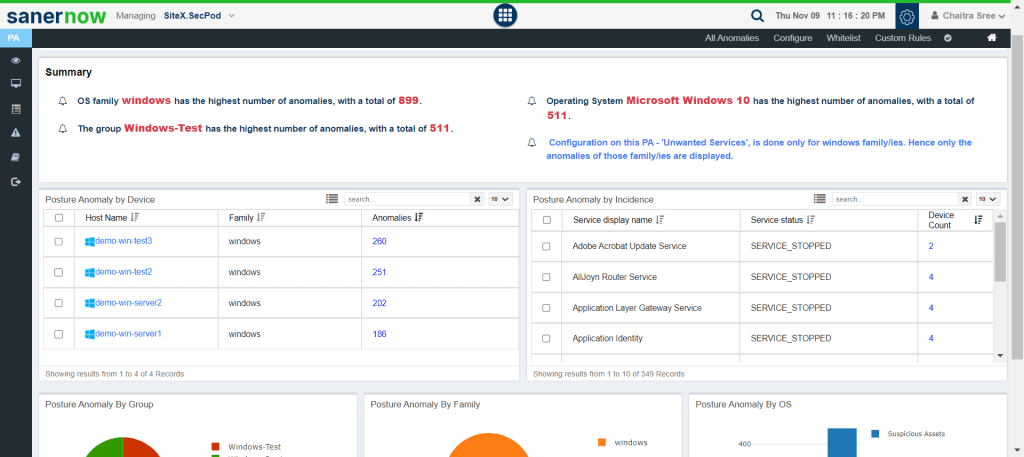
From the SanerNow unified dashboard, choose ‘Posture Anomaly,’ and you will see a very insightful dashboard that contains all the anomalies present in your organization, in addition they will be categorized based on group, family, and devices.
Click on configure; you will be given a list of which SanerNow supports. It consists of unwanted ports, unwanted services, unwanted startup applications, unwanted devices, and unwanted environment variables.
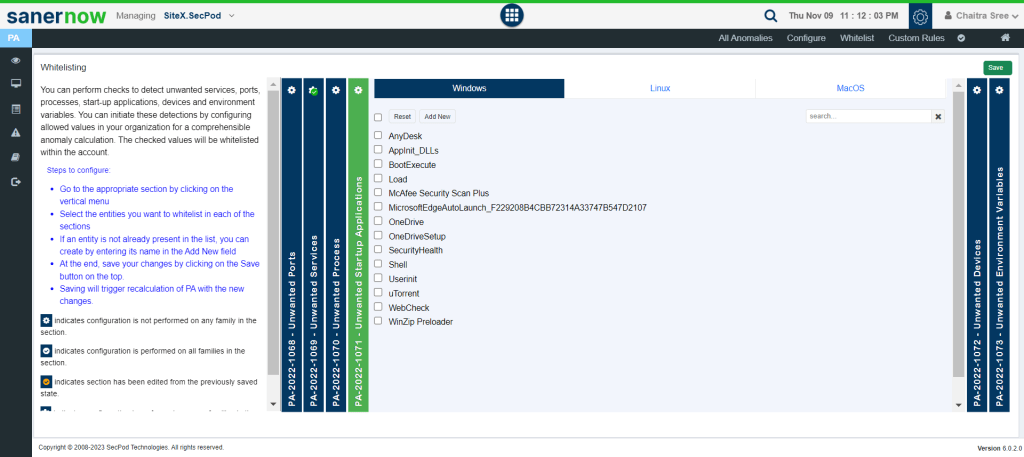
In this section, you can initiate the detection of unwanted applications and services by allowing the selected values. Additionally, to view if any suspicious applications or services are running, you can find them in the Continuous Posture Anomaly dashboard in the posture anomaly details section.
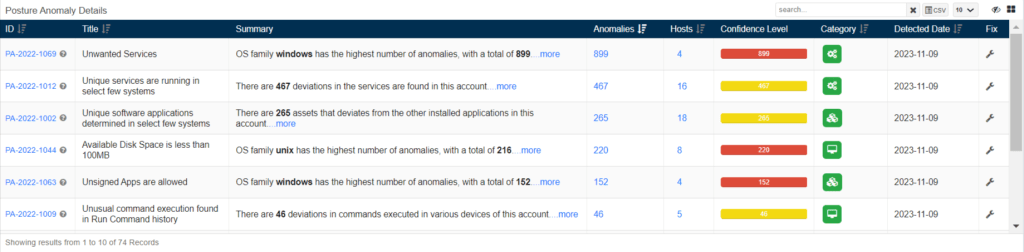
Furthermore, click the ID if you need more description
Click the fix button presented on your right to remediate them.
Conclusion
Unwanted applications and unique services pose a significant threat to any organization. They can compromise your privacy, exploit system vulnerabilities, and cause financial losses. However, by adopting preventive measures, staying informed, and implementing robust security practices, we can mitigate these risks and safeguard our digital lives. The continuous effort to stay ahead of evolving threats is crucial for maintaining a secure and resilient IT environment.