Spearphishing is a key weapon for attackers these days. Spam emails with malicious decoy documents are a dime a dozen. The social engineering used to lure users into opening these mails is elaborate and is unique to every attacker.
To break the news, an ongoing malicious campaign was found sending fake Windows Update emails to install ransomware. It is definitely interesting to see how well the story fits in. With Microsoft Patch Tuesday Updates released recently, it hardly seems suspicious to receive an alert about installing a missing update on Windows.
The story behind Windows Update Alert!
Researchers at Trustwave SpiderLabs analyzed emails with an admonishing subject line.
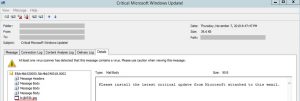
Install Latest Microsoft Windows Update now! Critical Microsoft Windows Update!
The body of the email contained a line urging users to install the latest critical Microsoft Windows Update from the attachment.
 Credits:https://www.trustwave.com
Credits:https://www.trustwave.com
The attachment seemed like a ‘.jpg’ file at first glance. But, it was revealed on further analysis that the ‘.jpg’ file was a malicious .NET downloader that delivers malware. The malicious executable was downloaded from GitHub, the link to which was hidden in a #STRINGS section in the executable.
The malicious executable
A file named ‘bitcoingenerator.exe‘ is downloaded from a GitHub account named misterbtc2020. This executable is the Cyborg Ransomware, a .NET compiled malware. The ransomware encrypts the files and leaves a ransom note. It is also known to drop a copy of itself at the root of the infected drive.
The analysis further reads that the ransomware builder files can be easily found on GitHub. This can be used by anyone with a nasty intent to spread Cyborg.
We advise Microsoft Windows users to be extremely cautious while opening any attachments received through emails. While it is important to keep your systems up-to-date with the latest patches, it would also be crucial to install updates from a legitimate source. Please install verified Microsoft Windows updates using SanerNow.

