A new massive threat is making its rounds in the security world. A tricky yet nasty piece of ransomware called Fantom. Many organizations are being infected with this ransomware. But luckily, there are definite ways to evade it and also ways to mitigate the damage without letting the troublemakers win.
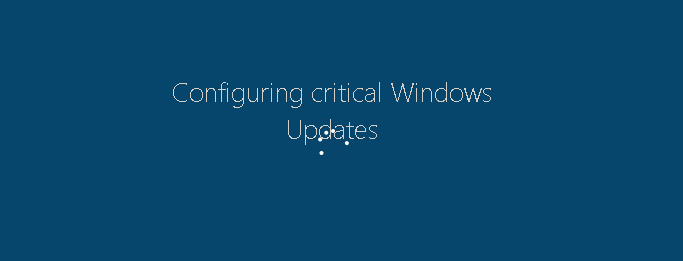
Fantom ransomware is a devious one. It is a huge threat to enterprises as it impersonates a screen most business users identify. It has an interesting feature of displaying a fake Windows updates screen that pretends Windows is installing a new critical update. The cyber criminals trust that employees will download the ransomware thinking that the upgrade prompt is legitimate. Fantom is distributed via emails, ads, malicious websites and many other methods.
Yes, you heard it right. As we suggest to update your operating system and software on a regular basis, Fantom uses the idea of updating Windows system with critical patch/update, by displaying a fake UI.
When a user clicks on this update thinking that it is a genuine one, the victim’s desktop will be changed to show a good looking critical update screen in full-screen mode, and in the meantime, it encrypts your files.
Threat indicators – Indicator of Compromise:
Fantom is destructive, yes once it is executed as a Windows critical update, it will run ‘delbak.bat‘ script which in turn will be executing the below command, resulting in loss of all the backup copy of local files.
vssadmin delete shadows /all /quiet
Volume Shadow Copy Service is a technology included in Microsoft Windows that allows taking manual or automatic backup copies or snapshots of computer files or volumes. vssadmin.exe is responsible for managing the Shadow Volume Copies in the system, using vssadmin an administrator can list, create, and delete the snapshots.
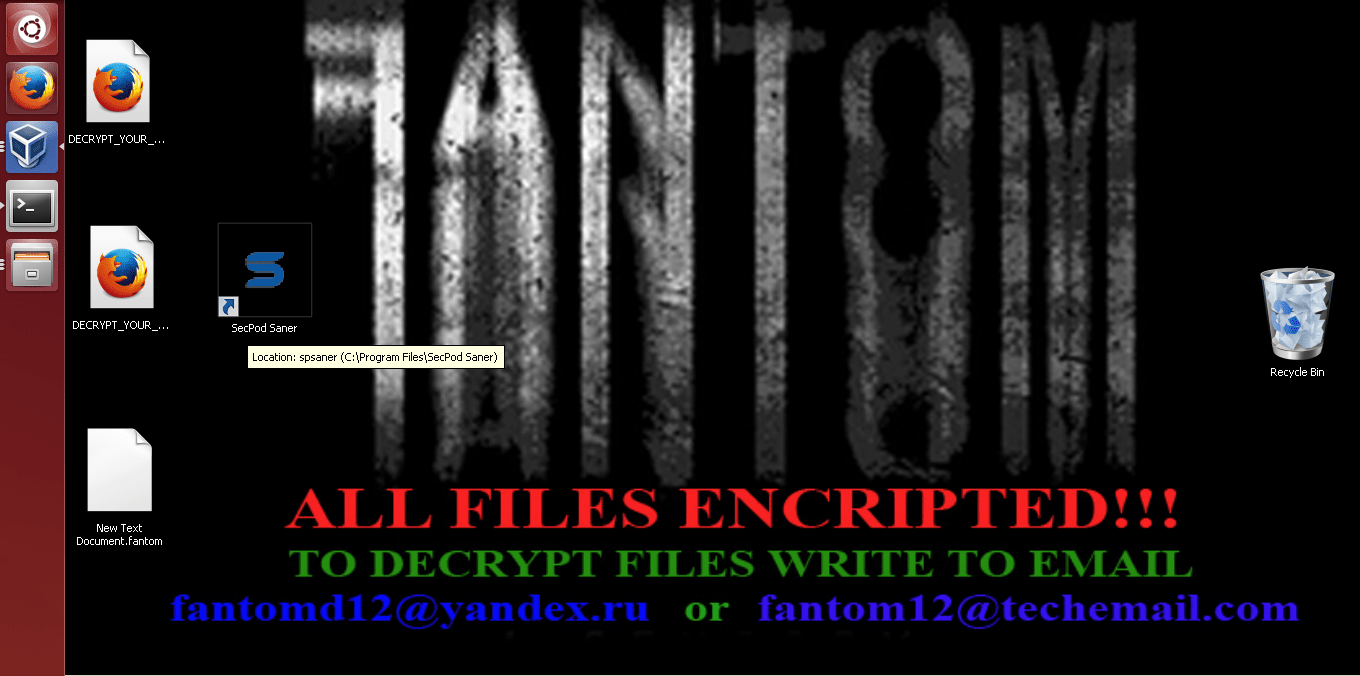
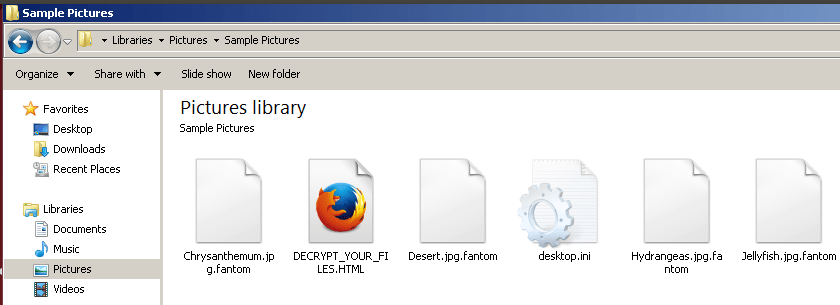
Fantom looks for some of the targeted extension file names, and start to encrypt victim’s files using AES and RSA encryption, after completion of encryption, ‘.fantom‘ extension will be added to each encrypted file. Fantom is quite smart enough to delete its traces and leaves DECRYPT_YOUR_FILES.HTML note in each folder it encrypted.
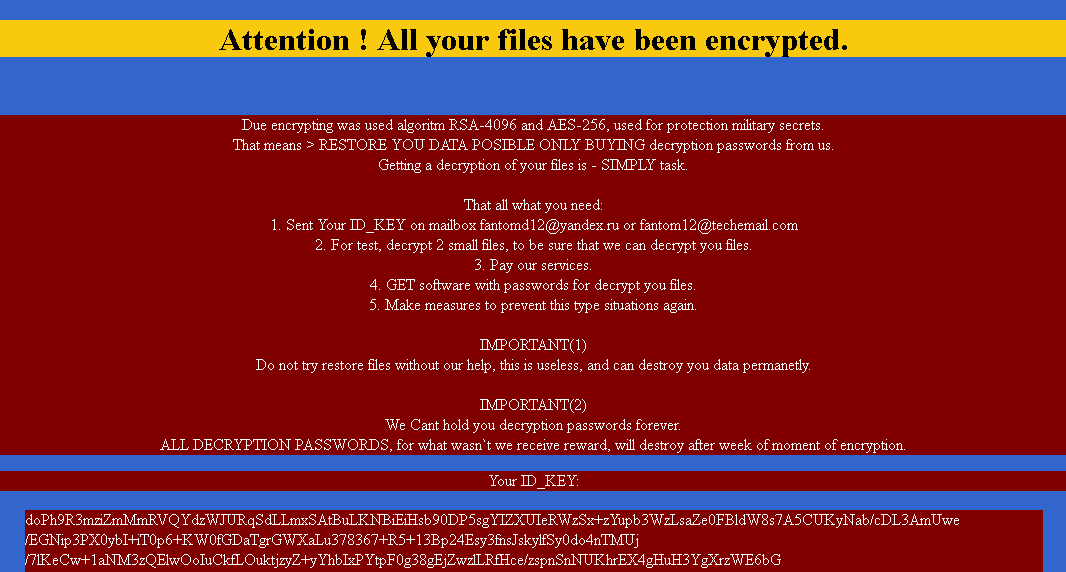
The DECRYPT_YOUR_FILES.HTML file contains information on how to decrypt files, here the victim has to mail the ‘ID_KEY’ generated after encryption to some of the mail address specified, and also they specify a very important note ‘5. Make measures to prevent this type situations again.’
Registry entries:
Adds an entry of its extension - Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts.fantom
Disables task Manager by setting DisableTaskMgr=1 under Software\Microsoft\Windows\CurrentVersion\Policies\System key
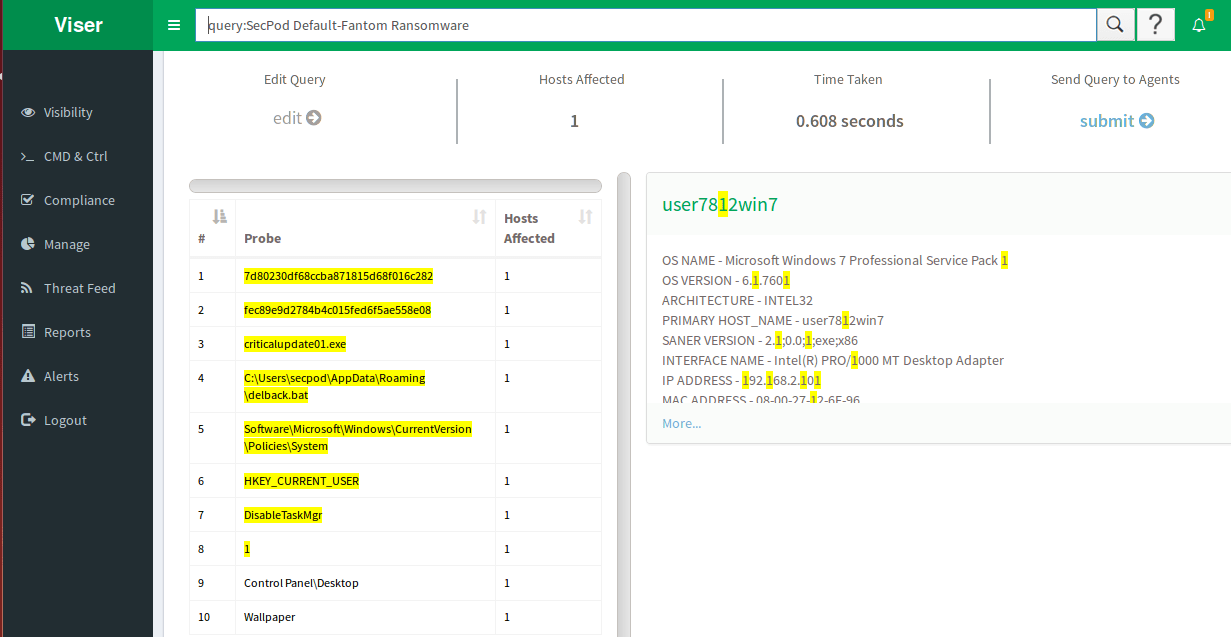
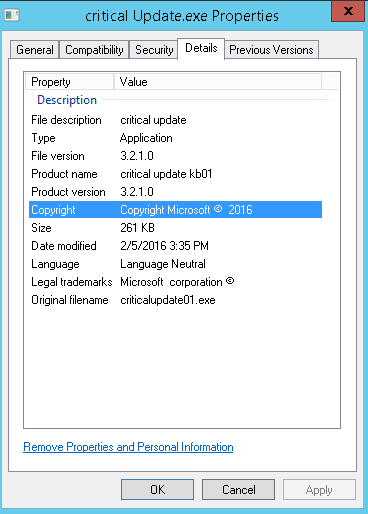
Fantom samples found to have unique original_filename -> criticalupdate01.exe, can be seen in below screenshot of a sample's properties.
MD5’s of some of the tested samples:
7D80230DF68CCBA871815D68F016C282
65E9E1566DEC1586358BEC5DE9905065
86313D2C01DC48D617D52BC2C388957F
60DBBC069931FB82C7F8818E08C85164
fec89e9d2784b4c015fed6f5ae558e08
52df26f735033f496e3739a43bc991b1
94328ca2cb87230a5b0c734e2321e993
f9284e8e84b1f4675bf8665bffa6e6ac
b65c44c3155dc2e50d6848a20fea3126
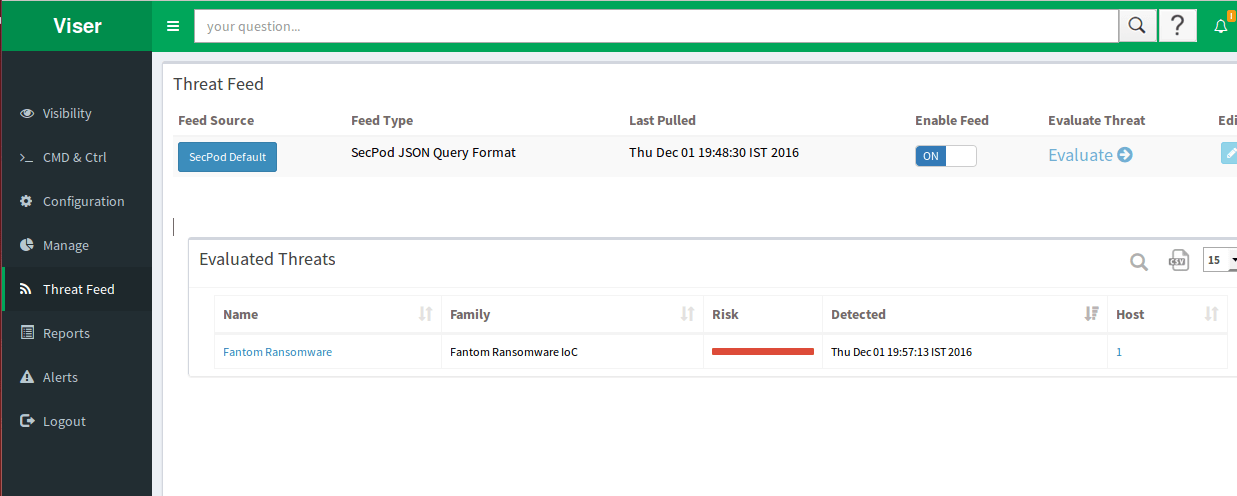
Saner in Action:
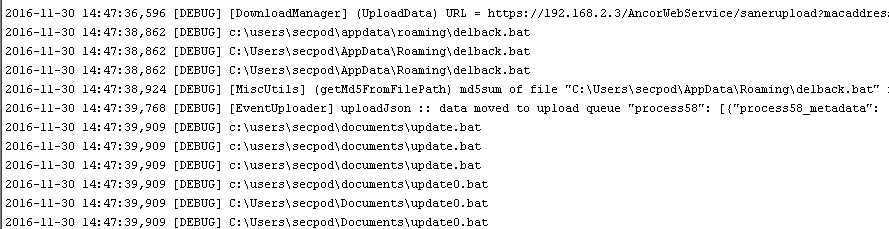
The snapshots below shows how Fantom ransomware will be detected by Saner in real-time.
Fantom indicators can be seen in the screenshot below.
Saner catches Fantom in real-time before complete encryption takes place, We’re always on the hunt for new threats. Be careful about opening skeptical items on the internet as much as possible, to avoid running into such malicious software in the future. Recognize Fantom malware alerts, trust Saner updates.
Also, see our whitepaper “Ransomware: A Billion Dollars a Year Cyber Crime” on how to stay protected against ransomware.
- Kashinath T (Security Research Engineer)