EmbedThis GoAhead is a simple and compact embedded web server which can be used to efficiently host embedded web applications. GoAhead is a very popular web server and is known to have 1.3 million installations worldwide. The only way to not have got these vulnerabilities is to have a vulnerability management tool.
A researcher from Cisco Talos discovered two security GoAhead Vulnerabilities Embedded Web Server. The two vulnerabilities are tracked as CVE-2019-5096 and CVE-2019-5097. These vulnerabilities arise due to a flaw in the processing of a multi-part/form-data HTTP request. HTTP requests use the multi-part/form-data content type for submitting forms that contain files, non-ASCII data, and binary data. Patch management software emits these vulnerabilities.
The chief in mischief: CVE-2019-5096
CVE-2019-5096 is a use-after-free (CWE-416) issue that occurs during the processing of HTTP requests within the base GoAhead web server application. An attacker who sends a crafted HTTP request can corrupt heap structures and achieve code execution.
Processing a multipart/form-data in HTTP GET/POST requests with multiple Content-Disposition headers in the same request can give rise to a use-after-free condition when cleaning the heap structures used to store different parts of the proposals.
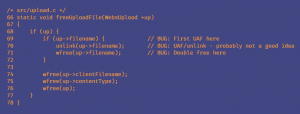
The vulnerability resides in ‘freeUploadFile()‘ in upload.c . A double free memory vulnerability exists here as the product calls free() twice on the same memory address. It potentially leads to modification of unexpected memory locations.
CVE-2019-5097 is a denial of service vulnerability that occurs during the processing of HTTP requests within the base GoAhead web server. An attacker can create an infinite loop during processing by sending a crafted HTTP request.
The infinite loop created using the crafted request leads to 100% CPU utilization. If the client connection ends before receiving the entire length of data specified by the Content-Length header, the server will continuously try to respond to the disconnected socket. Though the process handles the requests now, attackers can create further denial of service conditions depending on the available system resources.
The crafted data used could be an unauthenticated GET or POST request and does not require the requested resource to be present on the server. While certain route configurations could deny access to the vulnerabilities, attackers can use the default build configuration for exploitation. This is true because the default build configuration inherits permissions from the parent path. It does not require the existence of the requested page. The advisory indicates that successful exploitation requires enabling the MEGOAHEADUPLOAD compile-time flag and the existence of the path specified in MEGOAHEADUPLOAD_DIR. As a result, the default configuration is vulnerable. Also, the pages that require proof would not give way to access vulnerability without authentication.
Affected Products
EmbedThis GoAhead Web Server versions 5.0.1, 4.1.1 and 3.6.5
Impact of GoAhead Vulnerabilities
Successful exploitation allows an attacker to remotely execute code or conduct denial of service attacks.
Solution to GoAhead Vulnerabilities
EmbedThis has issued an update to resolve the vulnerability. We strongly recommend o install the latest updates without further delay.