Cybersecurity has never been more crucial today. With threats evolving constantly, it’s essential for businesses to stay one step ahead in safeguarding their IT infrastructure. A vulnerability assessment tool plays a vital role in identifying potential weaknesses in your organization’s infrastructure.
Let’s first understand what vulnerability assessment tools are and why they are essential. These tools scan your network systems and applications to discover vulnerabilities that cyber attackers could exploit. Organizations can proactively address these security issues and prevent potential breaches by identifying these weaknesses.
Vulnerability assessment solution goes beyond scanning and provides a view of an organization’s security posture. It involves scanning for vulnerabilities but also involves assessing the potential impact of these vulnerabilities and providing recommendations for mitigation.
Types of Vulnerability Assessment Tools
- Network-Based Scans – These tools focus on identifying vulnerabilities within network infrastructure, such as firewalls, routers, and switches.
- Application Scans – These tools assess the security of web applications and software by identifying vulnerabilities in the code.
- Host-Based Scans – These tools analyze individual devices or servers for security weaknesses, ensuring comprehensive protection for your endpoints.
- Database Scans – These tools specifically target vulnerabilities within your organization’s database, where sensitive data is stored.
Key Features to Consider:
When selecting a vulnerability assessment tool, several key features should be considered:
- Scanning Capabilities: Ensure the tool can perform the types of scans relevant to your organization, whether it’s network, application, host, or database scanning.
- Ease of Use: User-friendly interfaces and straightforward setup are essential, as they ensure that your security team can effectively utilize the tool.
- Reporting: Look for tools that provide comprehensive and then customizable reports with clear recommendations for remediation.
- Integration: Check if the tool can integrate with your existing security infrastructure for streamlined threat detection and response.
Top Vulnerability Assessment Tools:
Now that we have covered the basics, let’s discuss some of the top vulnerability assessment tools available:
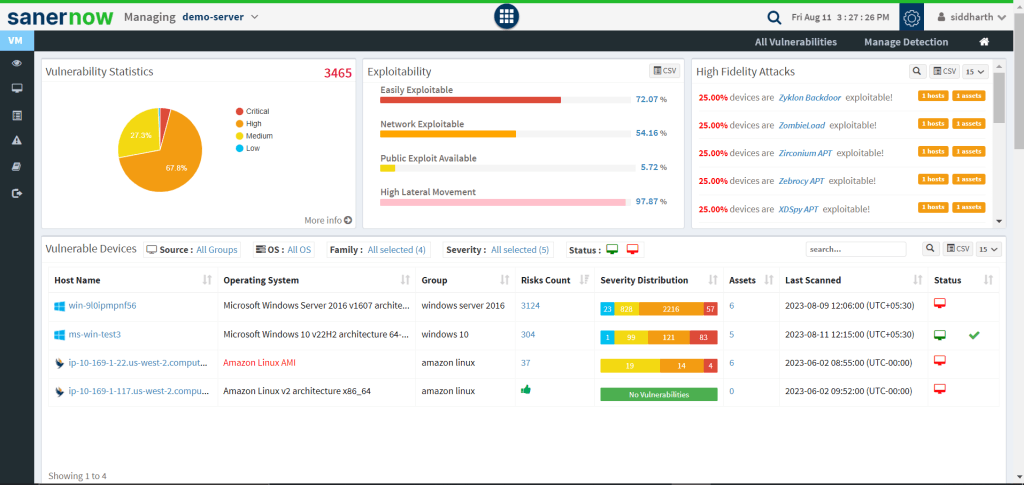
1. SecPod’s SanerNow:
- SanerNow is a Continuous vulnerability and exposure management solution.
- SecPod SanerNow offers a comprehensive vulnerability assessment solution with network, host, and application scan support.
- It provides detailed reports, prioritizes vulnerabilities, and offers integration options for seamless remediation.
- SanerNow supports patches for all major OSs, including Windows, Linux, and Mac, and supports over 550+ third-party applications.
- It has the world’s largest vulnerability database, with 190,000+ software vulnerability checks.
- SecPod’s SanerNow is the only vulnerability manager running the fastest automated vulnerability scans in less than 5 minutes.
- You can also get the complete picture of vulnerabilities all the time in a single unified dashboard.
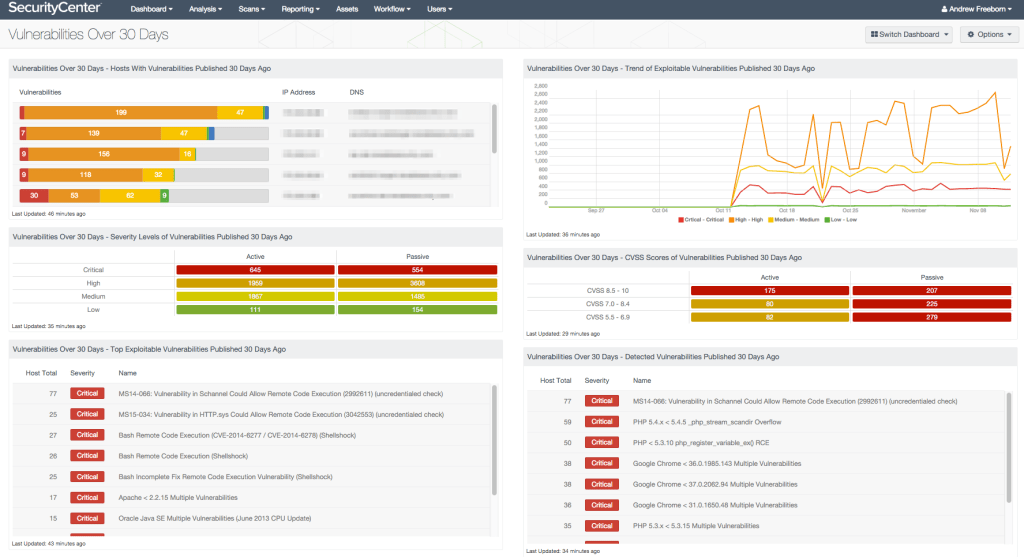
2. Tenable Nessus:
- Tenable provides you with vulnerability assessment capabilities you need to gain comprehensive visibility with deep insights across your entire environment.
- Nessus covers over 47,000 unique assets, including IT, IoT devices, operating systems, applications, and more.
- Nessus portability empowers you to run assessments whether you are in the headquarters or on another continent.
- However, Nessus can improve how they show the scan status while scanning.
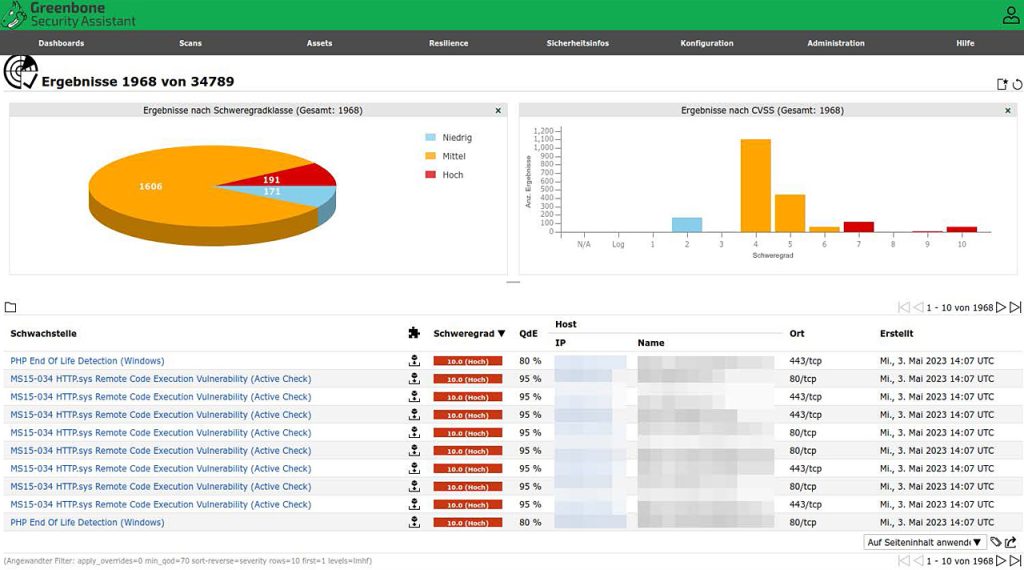
3. OpenVAS:
- OpenVAS is a full-featured vulnerability scanner.
- Its capabilities include unauthenticated and authenticated testing, high-level and low-level internet and industry protocols, performance tuning for large-scale scans, and a powerful internal programming language to implement any type of vulnerability test.
- OpenVAS is an open-source vulnerability scanner that is both powerful and cost-effective.
- However, OpenVAS covers fewer CVEs and test cases testing and assessment.
4. Qualys:
- Qualys alerts you in real time about network irregularities.
- Identifies threats and monitors unexpected network changes before they turn into cyber attacks.
- Qualys provides a cloud-based vulnerability management platform with a wide array of scanning options.
- It offers a user-friendly interface, strong reporting capabilities, and excellent scalability. However, navigation is pretty complex and involves a lot of pages to click through.
Conclusion
In conclusion, selecting the right vulnerability assessment tool is critical in securing your organization’s digital assets. Also, Understanding the types of tools available, considering key features, and exploring reputable options like SecPod SanerNow, Nessus, OpenVAS, and Qualys will empower you to make an informed decision. Remember, no tool is a one-size-fits-all solution, so choose the one that aligns with your organization’s needs and resources. Moreover, investing in the right tool can proactively protect your systems and data from potential threats and stay ahead in the ever-evolving cybersecurity landscape.