A campaign targeting government organizations in Central Asia was discovered delivering a backdoor named HAWKBALL Exploit. This backdoor can collect information from the victim’s system and it can also deliver various payloads. It also offers an attacker a range of malicious capabilities that includes examining the host, executing native Windows commands, terminating processes, creating, deleting files, uploading files, searching for files, and enumerating drives. However, a vulnerability management tool can stop this.
HAEKBALL Exploit
The campaign uses well-known Microsoft Office vulnerabilities CVE-2017-11882 and CVE-2018-0802 to infect its targets with the malware. Once infected, the main payload’s shell-code is dropped, decrypted, and executed on the victim system. However, a patch management solution can help this not to get infected. The payload also includes an encrypted configuration file that defines the C2 IP address to communicate with. After establishing the connection with C2 server, HAWKBALL’s actions defined by the commands received from C2 server.
Various commands supported by HAWKBALL Exploit include :
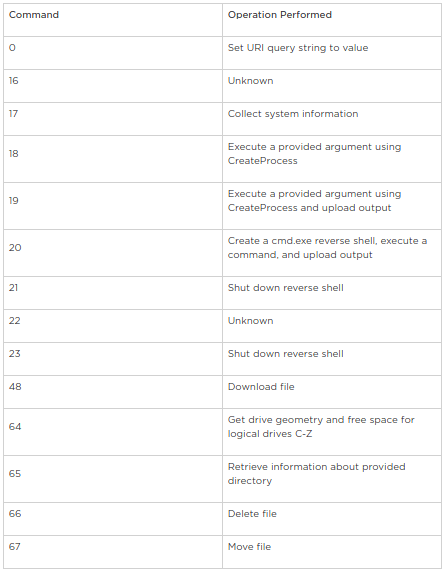
HAWKBALL Exploit also includes anti-debugging techniques like,
- Querying the value for the flag ‘BeingDebugged’ from PEB to check whether the process debugs.
- Using NtQueryInformationProcess API to detect if the process debugs
Microsoft Spam Campaign Warning:
Also, On 7th June 2019, Microsoft issued a warning about an active malware campaign using emails in European languages. However, The emails contain RTF files that carry the CVE-2017-11882 exploit and allows attackers to automatically run malicious code without user interaction.
The warning was provided via a tweet that reads as,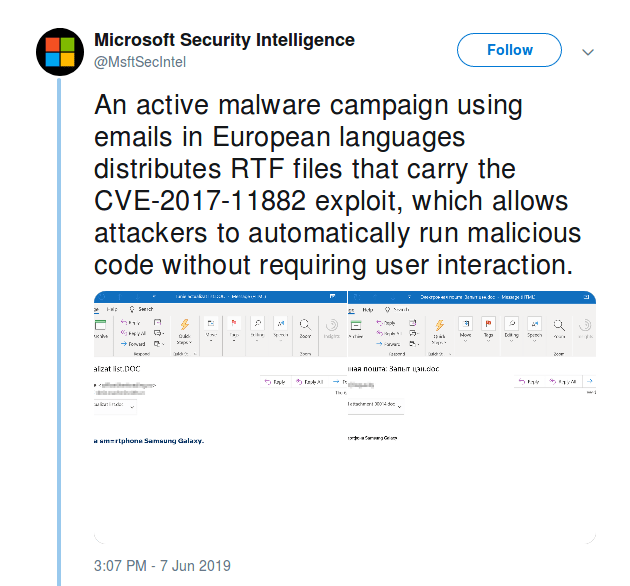
The vulnerability can simply exploited by simply enticing users to opening the attached document. When the attachment opened, it executes multiple scripts of different types (VBScript, PowerShell, PHP, others) to download the payload. Microsoft added that the final payload executable is a backdoor waiting to connect to its C2 server.
Affected:
Microsoft Office 2007, Microsoft Office 2010, Microsoft Office2013, Microsoft Office 2016
Impact:
Successful exploitation of these vulnerabilities could allow an attacker to run arbitrary code in the context of the current user, taking complete control of an affected system.
Solution:
Please refer to this KB article.

