January 2018 saw the rise of Meltdown and Spectre vulnerabilities concerning speculative execution side channels. A subclass of speculative execution side-channel vulnerability, termed as Speculative Store Bypass (SSB) was announced by Microsoft in collaboration with Google researchers and was assigned CVE-2018-3639. While Microsoft released several updates as a fix to this vulnerability, some additional measures have to be followed in order to mitigate it fully. In this article, we will discuss the necessary steps that involve updating a few registry settings to be fully protected from CVE-2018-3639 vulnerability. With the correct patch management tool, you can easily detect and remediate this instantly.
Affected OS: All supported Microsoft Windows
Solution :
1. Install the patches recommended in the Microsoft advisory for CVE-2018-3639.
2. Create the registry entries as described below:
For processors other than ARM or AMD:
For Windows Clients (Windows 7, Windows 8.1 and Windows 10):
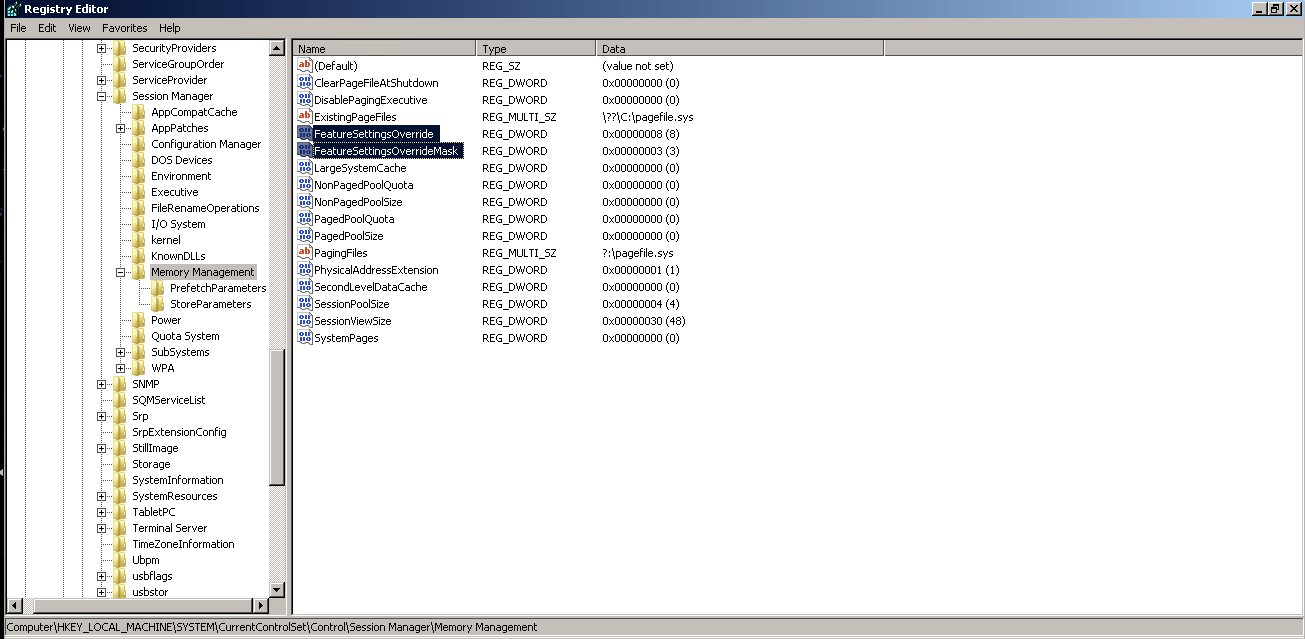
- Click Start, click Run, type regedt32 or type regedit, and then click OK.
- In Registry Editor, locate the following registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverride as the name of the newly-created DWORD and then press Enter.
- Double-click the DWORD FeatureSettingsOverride and change the value data field to 8.
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverrideMask as the name of the newly-created DWORD and then press Enter.
- Double Click FeatureSettingsOverrideMask and change the value data field to 3.
CVE-2018-3639 can be prevented by updating these registry settings and by using a good patch management software.

Please refer below image for registry changes.
CVE-2018-3639 Can be resolved in the Windows server by following these steps :
- Click Start, click Run, type regedt32 or type regedit, and then click OK.
- In Registry Editor, locate the following registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverride as the name of the newly-created DWORD and then press Enter.
- Double-click the DWORD FeatureSettingsOverride and change the value data field to 8.
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverrideMask as the name of the newly-created DWORD and then press Enter.
- Double Click FeatureSettingsOverrideMask and change the value data field to 3.
- In Registry Editor, locate the following registry path: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion and create a key named Virtualization.
- Right-click on Virtualization, point to New, and then click on String Value.
- Type MinVmVersionForCpuBasedMitigations as the name of the newly-created String Value and then press Enter.
- Double Click MinVmVersionForCpuBasedMitigations and change the value data field to 1.0.
For Windows systems with AMD processors:
CVE-2018-3639 can be solved for Windows Clients (Windows 7, Windows 8.1, and Windows 10):
- Click Start, click Run, type regedt32 or type regedit, and then click OK.
- In Registry Editor, locate the following registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverride as the name of the newly-created DWORD and then press Enter.
- Double-click the DWORD FeatureSettingsOverride and change the value data field to 72.
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverrideMask as the name of the newly-created DWORD and then press Enter.
- Double Click FeatureSettingsOverrideMask and change the value data field to 3.
CVE-2018-3639 can be solved for Windows Servers:
- Click Start, click Run, type regedt32 or type regedit, and then click OK.
- In Registry Editor, locate the following registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverride as the name of the newly-created DWORD and then press Enter.
- Double-click the DWORD FeatureSettingsOverride and change the value data field to 72.
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverrideMask as the name of the newly-created DWORD and then press Enter.
- Double Click FeatureSettingsOverrideMask and change the value data field to 3.
- In Registry Editor, locate the following registry path: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion and create a key named Virtualization.
- Right-click on Virtualization, point to New, and then click on String Value.
- Type MinVmVersionForCpuBasedMitigations as the name of the newly-created String Value and then press Enter.
- Double Click MinVmVersionForCpuBasedMitigations and change the value data field to 1.0.
For Windows systems with ARM processors:
CVE-2018-3639 can become a hassle if you don’t follow these steps.
For Windows Clients (Windows 7, Windows 8.1, and Windows 10):
- Click Start, click Run, type regedt32 or type regedit, and then click OK.
- In Registry Editor, locate the following registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverride as the name of the newly-created DWORD and then press Enter.
- Double-click the DWORD FeatureSettingsOverride and change the value data field to 64.
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverrideMask as the name of the newly-created DWORD and then press Enter.
- Double Click FeatureSettingsOverrideMask and change the value data field to 3.
Windows Servers:
- Click Start, click Run, type regedt32 or type regedit, and then click OK.
- In Registry Editor, locate the following registry path: HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverride as the name of the newly-created DWORD and then press Enter.
- Double-click the DWORD FeatureSettingsOverride and change the value data field to 64.
- Right-click on Memory Management, point to New, and then click DWORD (32-bit) Value.
- Type FeatureSettingsOverrideMask as the name of the newly-created DWORD and then press Enter.
- Double Click FeatureSettingsOverrideMask and change the value data field to 3.
- In Registry Editor, locate the following registry path: HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion and create a key named Virtualization.
- Right-click on Virtualization, point to New, and then click on String Value.
- Type MinVmVersionForCpuBasedMitigations as the name of the newly-created String Value and then press Enter.
- Double Click MinVmVersionForCpuBasedMitigations and change the value data field to 1.0.
CVE-2018-3639 can be resolved for windows clients and servers by following the above steps.
Automate Patching with Saner:
CVE-2018-3639 can be prevented by utilizing patch automation. Saner can automate the above patching across the organization with ease. Click to explore patching steps using Saner.
Saner Personal Users:
1. Download the Processor_mitigation_fix and unzip to get Processor_mitigation_fix.exe
2. Open the cmd.exe as ‘Administrator’
3. Go to the path where exe “Processor_mitigation_fix.exe” is extracted
4. Run the below command with “/S” silent option to fully patch this vulnerability.
C:\>Processor_mitigation_fix.exe /S
These steps will resolve this CVE-2018-3639 vulnerability completely. Saner will stop reporting about this vulnerability from the next manual or scheduled scan.
Note: In case of any issues faced, unzip Processor_mitigation_fix_revert and use the file Processor_mitigation_fix_revert.exe in a manner similar to the one described above.
Have any questions on how to fix CVE-2018-3639 specific to your IT? Let’s discuss.