An outbound connection is a network connection going out of a particular device or network. Most, if not all, applications and devices in a network make outbound connections to send and receive data. So what if a hacker gets into the network by exploiting a vulnerable application and starts making dangerous outbound connections to their advantage? A good vulnerability management tool can help to combat these vulnerabilities.
An outbound connection from a vulnerable application can cause worry, or it can just be the application performing its function, but it’s a dangerous security risk nonetheless. A hacker can export sensitive data or import dangerous ransomware right under your nose by veiling it as a legitimate connection, which can be catastrophic. A Vulnerability Management Software can stop these attacks.
SanerNow Continuous Posture Anomaly Management to the Rescue
Anomalies are outliers in your IT network when the network is evaluated collectively against the known good. Vulnerable processes, unusual and unsigned applications, unwanted applications, and dangerous outbound connections are a few examples of posture anomalies that can devastate your IT posture. And SanerNow CPAM allows you to detect and fix these anomalies to normalize your IT network and strengthen your IT security posture. But SanerNow can also detect vulnerabilities and other security risks and instantly remediate them as well.
Combating Outbound Connections from Vulnerable Applications with SanerNow
There are three major steps in combating outbound connections. Before you detect outbound connections from vulnerable applications, you need to detect which application in your network is vulnerable first. Following that, you must detect which applications are creating outbound connections and, lastly, block the applications to ensure nothing untoward can happen.
1. Vulnerable applications are apps in your network that contain vulnerabilities and potential risks to your network. These applications might be compromised, and hackers might use them to mask shady connections as legitimate ones. SanerNow’s vulnerability management module detects vulnerabilities in applications installed in your network, which allows you to have visibility over the security risk in your network.
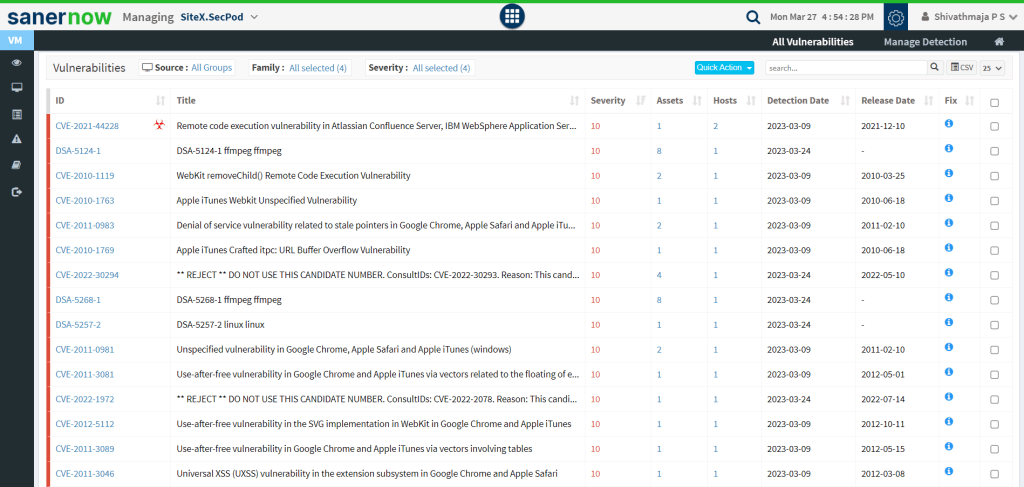
2. All vulnerable applications do not necessarily create outbound connections. So it’s important to detect which vulnerable applications are creating them. Therefore, SanerNow detects which application connects with what and provides insights on whether the connection is unusual. This helps determine if the connection is dangerous or legitimate.
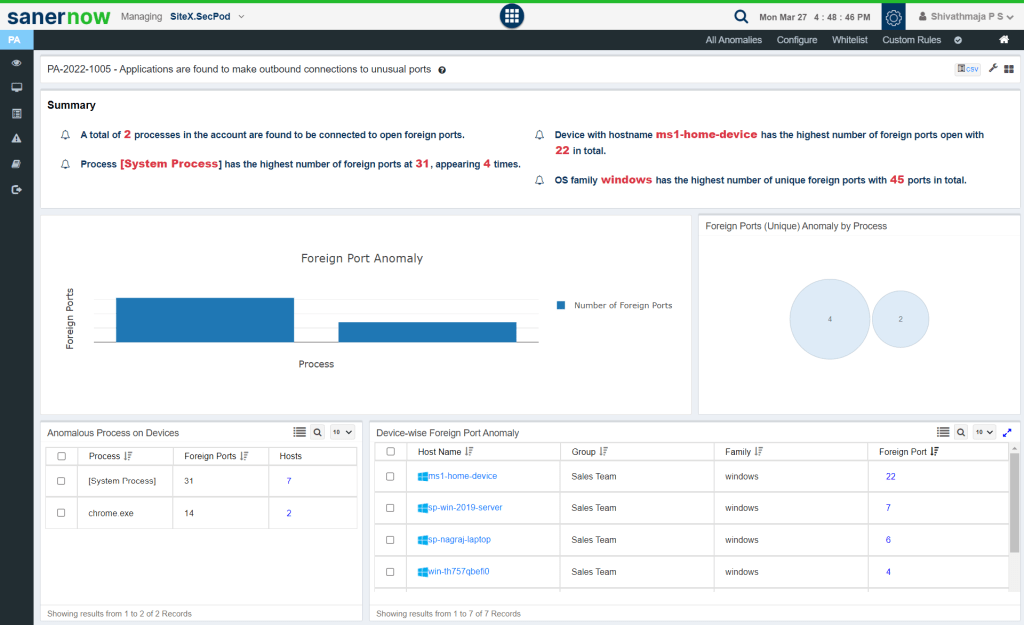
3. Once the vulnerable application is determined, you can simply block or remove the application from your network with SanerNow to mitigate the risk.
Conclusion
In the present day, looking at software vulnerabilities alone doesn’t cut anymore. Hackers use, abuse, and exploit every risk in every nook and corner of your network, and the onus is on you to protect your network. Because a small mistake, a single vulnerability, or an outbound connection can bring your organization to its knees.


