How to secure Java code?
Every software developer must follow certain standards and practices while coding and writing, secure code is one such practice. Everyone who loves to code must ensure their software is not vulnerable to exploits or being a principal cause of a cyber-attack. Here are the few best Java code security practices below. The solution for the problems causing by these vulnerabilities is a good vulnerability management system.
Anyone can code, but it is of no use in the long run if our code is unreliable enough. There are numerous hackers who prey on vulnerable software. By not coding securely, we let those cyberpunks compromise our applications. A good vulnerability management tool can stop these cyberpunks.
To build secure Java code applications, we must adhere to certain principles:
- Follow the secure coding standards.
- Review code for security.
- Design a framework for attaining an unremitting process for secure software.
Follow the secure coding standards.
Here are a few pointers with examples of mistakes developers often make:
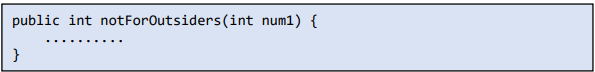
1. Use the access modifiers available in Java to their fullest by restricting access to methods and classes when required. For example, we often use public access specifiers without thought.
Do not make any functions and variables public unnecessarily if they need not be of use in other packages.
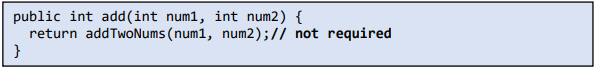
2. Avoid writing complex code, as it could have hidden security loopholes and the process of debugging errors or bugs in your code. Often, coders write redundant methods and complicate the code.
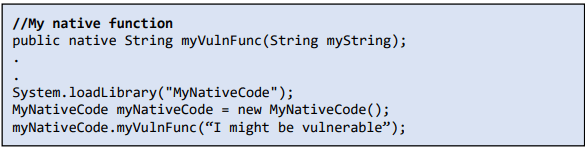
3. Java automatically checks array bounds and buffer overflows, but the code can be made vulnerable is a special case when one uses JNI to call native code.
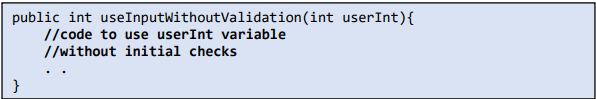
4. To protect your software, validate all the inputs given by a user and avoid blindly trusting a function input. A developer might not be validating the input given by users.
Tip: If any user enters a non-positive value, it can cause trouble, so make sure to validate the input.
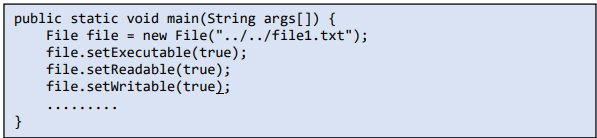
5. Do not provide unnecessary permissions or privileges to a file or folder. For example, as in the code below, providing all permissions to a file might not be necessary. Relative paths can cause files to be written and execution is inside unintended directories.
Tip: Provide only required permissions. Otherwise, anyone can modify the file and cause harm to the system.
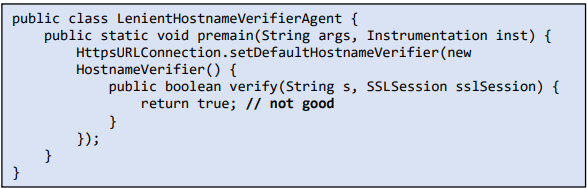
6. Always communicate with external systems over SSL and verify the certificate provided by the server. Often Java developers override the setDefaultHostNameVerifier function with a non-strict version of allowing all host names without verification.
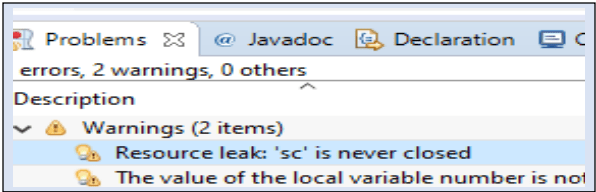
7. Try not to ignore compiler warnings, as few of them could be security related warnings. We often hear developers saying ‘It is just a warning’ but beware these might be the source of the problem at run-time.
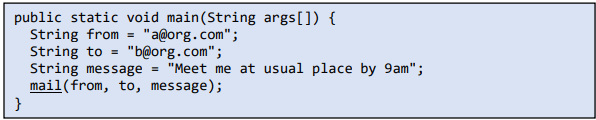
8. It is always better to encrypt and encode your data. Always keep a look-out for unintentionally transferring confidential information in a plain message.
Tip: Sending a plain message directly is not a good practice, always encrypt and encode any message that is going via mail or through the network. It is also appreciative if you can use effective techniques to hide email addresses from spam bots.
9. Learn to handle errors and exceptions correctly. Please ensure that you are handling a known error effectively. Known errors and exceptions can be handled beforehand using try-catch blocks, throws, etc.
10. Many useful secure Java code libraries are available but use only efficient, known, and tested libraries.
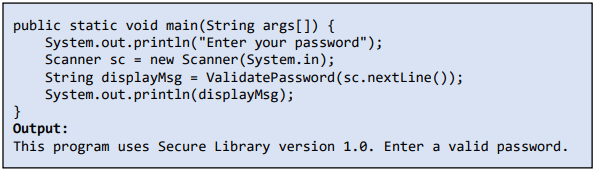
11. Keep your error messages short and simple; don’t expose your implementation through error display messages. Often errors and stack traces expose too much information.
Tip: Providing precise or detailed error messages is not a safe way to code; hide the implementation from the user.
12. Beware of serializing objects containing sensitive data, as important information leaking could lead to losing customers’ trust, creating a huge financial predicament and other reputational damage.
13. Audit all user actions to know what they are up to, because even if something goes wrong and eventually affects your software, at least you must know what went wrong. For example, designing a logging mechanism that does not journal all the user actions provides less visibility to a possible security bug.
Tip: Don’t just log information; audit every crucial action the users perform and raise alerts when an unintended action occurs.
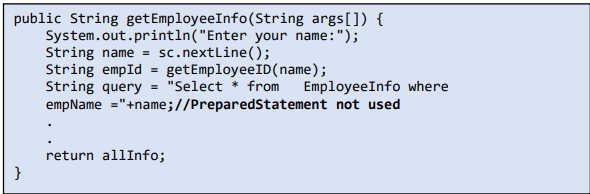
14. Use the PreparedStatement class of the Java.sql package because it escapes special characters automatically, which prevents SQL injection.
An example that showcases input that is not processed before use.
Tip: Using an unprocessed SQL input directly could leak the sensitive data stored in your database, so it is advised to process such inputs with PreparedStatement.
15. Use the Security manager class provided by Java to enforce or grant permissions and restrict certain operations. The security manager class allows applications to implement a security policy. It allows an application to determine, before performing a possibly unsafe or sensitive operation, what the operation is and whether it is being attempted in a security context that allows the operation to be performed (source: docs.oracle.com).
Review code for security
Reviewing the code is an essential step during development of your software, as it brings consistency between design and implementation of your project by identifying bugs and other performance concerns related to time and space complexity. Code review can be done manually or using automation tools.
Using automation tools is a good practice, but that alone is not sufficient to find flaws in your code and verify if it is secure, but a mix of human review along with automation can make your software less prone to manipulation using exploits.
Automation helps you test your application quickly and reveal its performance basing it on different contexts where it is in use. They can detect most of the known vulnerabilities, such as an SQL injection or a Cross-Site Scripting issue. But they cannot handle unfamiliar behaviors. Whereas humans can find those undecipherable errors through accurate design, data validation, and uncovering logical errors.
Here are the top 10 Static Code Analysis Tools for Java, C++, C# and Python- Raxis, RIPS Technologies, PVS-Studio, Kiuwan, Gamma, DeepScan, reshift, CodeScene Behavioral Code Analysis, Visual Expert, Veracode, Code Compare, Fortify Static Code Analyzer and Parasoft (source: softwaretestinghelp.com, last updated March 11 2020).
Design a framework for attaining an unremitting process for secure software.
Automation frameworks are common in every field; each is used for a different purpose, but they all share a common goal: reducing human work and plausible errors. Likewise, in Java, frameworks like JUnit can be in use to write unit test cases for your code, Selenium to test the UI, REST Assured for integration testing of REST API, etc.
A single framework might not be sufficient to automate tests related to your code. Each tool, such as JUnit, TestNG, and JWalk, has its own limitations; at times, none of them might be compatible with your code and help us easily substantiate code security.
The preeminent solution for a secure Java code could be designing a framework that focuses on characteristics vital to your software combined with the best security practices certification module.
Certain ideas that one can pitch to create our own framework,
- Developing a single automation tool to cover all the required functionalities. For example, unit testing, integration testing, web-based testing, and automation. These can be integrated and interrelated to diagnose and fix issues asap.
- Creating orchestration software for release automation and continuous delivery so that every stakeholder in the software development is aware of the software’s quality. Developers and testers can spend more time on security testing.
- Designing a mechanism to update all the libraries to its latest version. This ensures our software uses libraries with recent security fixes and performance enhancements.
- Understanding static code analyzing tools and evolving the framework to include enhancement features with minimal changes. This can be achieved if we design the functionalities with loosely coupled architecture bearing resilience to changes, flexibility, re-usability, and security.
Conclusion
In today’s world, much information is transfering and processing by systems through the internet, and data protection against breaches is inevitable. To achieve this, secure coding practices must be followed by developers, and the experienced coders must bring awareness about repeated coding issues or patterns resulting in insecure code to the ingenuous developers. Your Java code cannot be 100% secure, but these practices increase the percentage of “how secure you can code.”