Researchers have discovered another interesting vulnerability in the line of speculative execution attacks in Intel processors. This vulnerability named Load Value Injection (LVI), and is tracked as CVE-2020-0551. However, tracked using a vulnerability scanning tool. LVI is a new class of side-channel attacks that abuses microarchitectural flaws in processors to steal data.
Modern processors resistant to Meltdown, Foreshadow, ZombieLoad, RIDL and Fallout attacks known to be vulnerable to LVI. Researchers also mention that this attack is harder to mitigate than the previous ones as it can gain access to any memory virtually. LVI attacks leave no trace in traditional log files and make it nearly impossible to spot an attack. The mitigations would include expensive software patches by a patch management tool and could slow down the system by a factor of 2 to 19 times.
Understanding LVI: Cross-Domain Transient Execution Attacks
CVE-2020-0551 is a class of transient-execution attacks that adopts techniques from Spectre and Meltdown to cause a much deeper impact. There are two kinds of channels during processor operations namely: legitimate channels and incident channels. Legitimate channels are those that specifically designed to carry the data. The other channels which could contain information about variations in power consumption, state of CPU cache, etc. are incident channels. The incident channels whose inputs and outputs controlled called covert channels. Those incident channels which allow an attacker to only read from it called side channels.

Speculative Prediction and Transient Execution
Source: https://software.intel.com/security-software-guidance/insights
Modern-day processors use speculative execution to improve their performance. If the CPU’s speculative value is correct, the processor continues the operation. In case the speculated value is wrong, then that value has to be discarded and the CPU resumes its operations with a correct value. These instructions that are created in case of wrong speculative values are called transient instructions. Although these instructions get discarded eventually, they leave an impact on the microarchitectural processor state in terms of creating incident channels.
Transient Execution Attack
Attackers intend to capture and monitor the information contained in incident channels and use it to their benefit. An attacker who can access the sensitive data; receive and transmit it over covert channels can launch a transient execution attack. A transient execution attack allows an attacker to make use of the side effects of transient instructions on the microarchitectural processor, thereby allowing him to access data that protected by access control mechanisms.
There are three known types of transient execution attacks:
- Domain-Bypass Transient Execution Attack
- Cross-Domain Transient Execution Attack
- In-Domain Transient Execution Attack
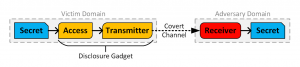
Cross-Domain Transient Execution Attack
Source: https://software.intel.com/security-software-guidance/insights
The LVI Attack
The LVI attack is a Cross-Domain Transient Execution Attack. This attack could involve the use of Branch Target Injection(Spectre variant 2). A malicious ring 3 application (attacker) can control a branch predictor involved in speculative execution and connected to another ring 3 application(victim), and trick it into picking data such as a memory address of the attacker’s choice. This predicted data could help the attacker in transiently accessing and transmitting data over a covert channel before discarded.
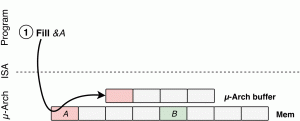
Source: https://lviattack.eu/
Click to view the LVI attack process
To sum up, under certain circumstances, the attacker can inject arbitrary data, thereby replacing the already existing data that loads into the memory. The application will use this injected value until it realizes a fault has occurred and then rolls back all its operations. A short window when attacker induced data processed jeopardized to control the flow of data.
A number of variants of LVI could come into existence. Jo Van Bulck and his fellow researchers have outlined the variants that could come into existence. The attacks in the first level are those which use fault or assist type to trigger the transient execution. The variants in the second level use microarchitectural buffer as the injection source.
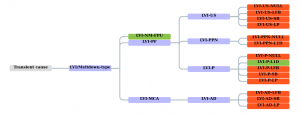
Two-level LVI classification tree
Source: https://lviattack.eu/
This attack is very complex in nature and Intel has itself declared that “LVI is not a practical exploit in real-world environments where the OS and VMM are trusted.”
Affected Products
Intel provides a full list of processors affected by this vulnerability.
Impact
An attacker can steal sensitive data such as fingerprints, passwords and keys from secure vaults on Intel processors. Bitdefender states that this vulnerability could be much devastating in
Solution
Intel has released a security advisory to help mitigate this vulnerability in Intel SGX SDK. Although software workarounds are available, the vulnerability primarily affects the underlying processors and therefore the software fixes cannot completely mitigate the flaw. It recommended to install the software updates on applicable systems as soon as possible.
Read about SanerNow Vulnerability Management

