Two new critical vulnerabilities discovered affects every processor since 1995, which allow malicious programs to steal information from other programs’ memory. These vulnerabilities named Meltdown (CVE-2017-5754) and Spectre (CVE-2017-5753 and CVE-2017-5715). Using a patch management solution, we can mitigate this vulnerability.
Meltdown and Spectre vulnerabilities affect all processors since 1995 including AMD, ARM, and Intel. These vulnerabilities allow an attacker to access and read the data from the memory of another process. This might include passwords from password manager or browser, personal and business-critical documents, emails, instant messages, etc. Having a vulnerability management tool is essential.
According to Google, everything and everyone is affected. This includes all major chipset vendors (Intel, AMD, ARM), all major operating systems (Windows, Linux, MacOS, Android, ChromeOS), cloud providers (Amazon, Google, Microsoft), and application makers.
Meltdown (CVE-2017-5754):
Meltdown breaks the basic isolation between an operating system and user process. The isolation between the kernel and user processes is typically realized by a supervisor bit of the processor that defines whether a memory page of the kernel accessed or not. The basic idea is that this bit set when entering kernel code and it is cleared when switching to user processes. This hardware feature allows operating systems to map the kernel into the address space of every process and to have very efficient transitions from the user process to the kernel, e.g., for interrupt handling. Consequently, in practice, there is no change of the memory mapping when switching from a user process to the kernel.
Google says "it chose the Meltdown codename because the bug basically melts security boundaries which are normally enforced by the hardware, and verified Meltdown only against Intel CPUs, but not ARM and AMD".
Meltdown technical research paper is here
There are software patches avaiable for Linux (KPTI (formerly KAISER) patch), Windows and Mac OS X to mitigate this vulnerability.
Spectre(CVE-2017-5753 and CVE-2017-5715):
Spectre breaks the isolation between two different programs and as per researchers "Spectre allows an attacker to trick error-free programs, which follow best practices, into leaking their secrets. In fact, the safety checks of said best practices actually increase the attack surface and may make applications more susceptible to Spectre."
Spectre technical research paper is here
Impact:
A successful exploitation could allow attackers to gain unauthorized access to sensitive data, which might include passwords from password manager or browser, personal and business-critical documents, emails, instant messages etc.
The Meltdown attack allows reading of kernel memory from userspace. This can result in privilege escalation, the disclosure of sensitive information and Spectre attack can allow inter-process or intra-process data leaks.
Which systems are affected by Meltdown CVE-2017-5754?
All Desktops, Laptops, Cloud computer with Intel Processor which implements out-of-order execution. i.e every Intel processors since 1995 (except Intel Itanium and Intel Atom before 2013) and currently it is not clear, ARM and AMD processors affected by Meltdown.
Which systems are affected by Spectre?
All Desktops, Laptops, Cloud computers and even Smartphones with modern processors capable of keeping many instructions in flight.
Mitigations and Patches:
Microsoft Windows:
Microsoft has released an emergency security updates to Windows 10 to mitigate these vulnerabilities.
Other Windows versions patched on the regular “Patch Tuesday on January 9, 2018”.
MacOS:
Apple had already fixed these security vulnerabilities in MacOS High Sierra 10.13.2 last month, but MacOS 10.13.3 will enhance or complete these mitigations.
Linux:
Linux vendors had released a patch by implementing kernel page-table isolation (KPTI) to move the kernel into an entirely separate address space.
Android:
Google has released security patches for Pixel/Nexus users as a January security patch update and other users have to wait for their respective device manufacturers to release a security patch.
Chrome Users:
Since attacks can happen through the website, Chrome users can turn on Highly experimental security feature called “Strict site isolation”.
How to turn on “Strict site isolation” on Google Chrome:
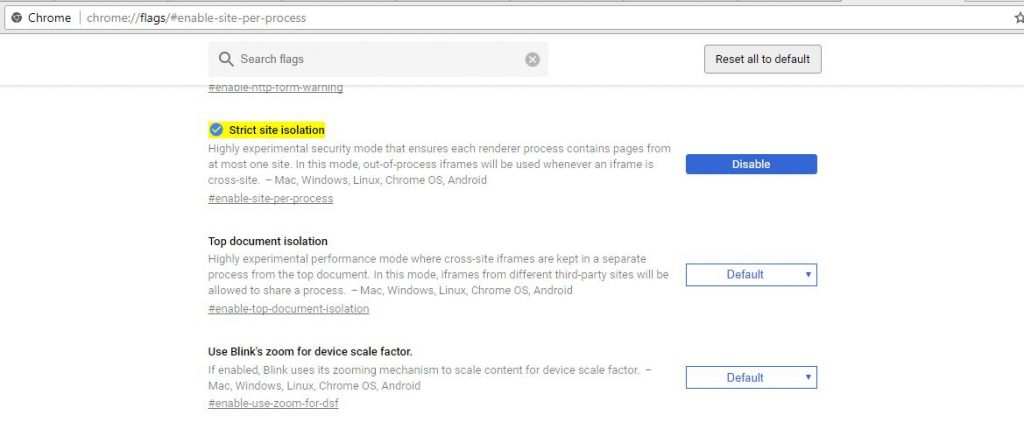
- Copy “chrome://flags/#enable-site-per-process” and paste it into the URL field at the top of your Chrome web browser, and then hit the Enter key.
- Look for Strict Site Isolation and click on “Enable” as shown in the above diagram.
- Restart your Chrome browser.
SecPod Saner detects these vulnerabilities and automatically fixes it by applying security updates. . Download Saner now and keep your systems updated and secure.

