On this August 2023 Patch Tuesday, Microsoft addresses security issues in 87 vulnerabilities. Two vulnerabilities are currently being exploited, and twenty-three vulnerabilities could lead to remote code execution. A Vulnerability Management System can prevent these attacks and keep your system safe.
Although the fixes addressed twenty-three remote code execution vulnerabilities, Microsoft’s severity classification designates only six as ‘Critical.’
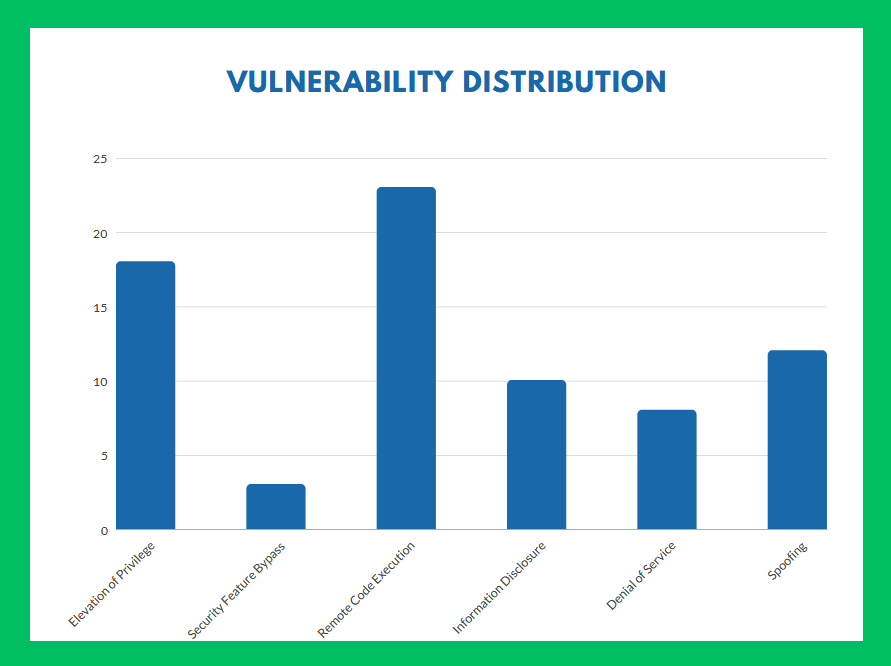
To provide further insight into the distribution of vulnerabilities, the list includes eighteen vulnerabilities related to privilege elevation, three vulnerabilities involving security feature bypass, ten vulnerabilities associated with information disclosure, eight vulnerabilities that could lead to denial of service, and twelve vulnerabilities related to spoofing these came to light by Microsoft August 2023 Patch Tuesday. Vulnerability Management Tool can resolve these issues.
Zero-day/Actively exploited Vulnerabilities
ADV230003 – Microsoft Office Defense in Depth Vulnerability. Microsoft issues an Office Defense in Depth update to address a patch bypass for the CVE-2023-36884 remote code execution vulnerability previously mitigated and actively exploited.
The CVE-2023-36884 enabled malicious actors to generate specially crafted Microsoft Office documents capable of circumventing the Mark of the Web (MoTW) security feature. This leads to opening files without showing a security warning, thus facilitating remote code execution.
CVE-2023-38180 – .NET and Visual Studio Denial of Service Vulnerability. Microsoft has patched a vulnerability in its .NET framework that could be exploited to launch denial-of-service (DoS) attacks against .NET applications and Visual Studio. However, the vulnerability, actively exploited in the wild, allows attackers to send specially crafted input to a vulnerable application.
Microsoft has not released any details about how the vulnerability was exploited in attacks or who discovered it. However, the company has advised users to update the latest version of the .NET framework to mitigate the risk.
Critical Vulnerabilities of Microsoft August 2023 Patch Tuesday
CVE-2023-29330 and CVE-2023-29328 – Microsoft Teams Remote Code Execution Vulnerability. An attacker can trick a user into joining a malicious Microsoft Teams meeting, allowing the attacker to execute code on the victim’s computer. This can be done without special privileges, leading to the theft of information, the alteration of data, or even downtime for the victim’s machine.
CVE-2023-35385 and CVE-2023-36911 – Windows Message Queuing Remote Code Execution Vulnerability. Successful exploitation of this vulnerability allows an unauthorized malicious user to execute code on the target server remotely. This means the attacker could take control of the server and do anything they want, including stealing data, installing malware, or disrupting operations.
CVE-2023-36910 – Windows Message Queuing Remote Code Execution Vulnerability. To exploit this vulnerability, the attacker would send a specially crafted malicious MSMQ packet to an MSMQ server. This packet could contain code executed on the server side, giving the attacker remote code execution on the server.
CVE-2023-36895 – Microsoft Office Outlook Remote Code Execution Vulnerability. To exploit this vulnerability, the attacker must send a specially crafted file to the victim. Once the victim opens the file, the attacker’s code executed on the victim’s computer, giving the attacker control.
Product: Windows Message Queuing
CVEs/Advisory: CVE-2023-35376, CVE-2023-35377, CVE-2023-35383, CVE-2023-35385, CVE-2023-36909, CVE-2023-36910, CVE-2023-36911, CVE-2023-36912, CVE-2023-36913, CVE-2023-38172 and CVE-2023-38254
Impact: Denial of Service, Remote Code Execution, and Information Disclosure
Product: Azure HDInsights
CVEs/Advisory: CVE-2023-36881, CVE-2023-36877, CVE-2023-38188, CVE-2023-35394 and CVE-2023-35393
Impact: Spoofing
Product: Microsoft Office SharePoint
CVEs/Advisory: CVE-2023-36890, CVE-2023-36891, CVE-2023-36892 and CVE-2023-36894
Impact: Information Disclosure and Spoofing
Product: Windows Kernel
CVEs/Advisory: CVE-2023-35359, CVE-2023-35380, CVE-2023-35382, CVE-2023-35386 and CVE-2023-38154
Impact: Elevation of Privilege
However, SanerNow Vulnerability Management and SanerNow Patch Management detect and automatically fix these vulnerabilities by applying security updates. Finally, use SanerNow and keep your systems updated and secure.