It’s that time of the month again! The second Tuesday of April 2025 has arrived, bringing Microsoft’s latest batch of security updates and non-security improvements for its suite of products.
Microsoft Patch Tuesday, April 2025, addressed 137 flaws through security updates. Alarmingly, this release includes one zero-day vulnerability. Furthermore, 11 are classified as critical, indicating vulnerabilities that could allow for remote code execution or significant system compromise without user interaction.
Beyond the urgent security imperatives, this Patch Tuesday also brings essential non-security updates, notably improvements and bug fixes for Microsoft Edge (Chromium-based).
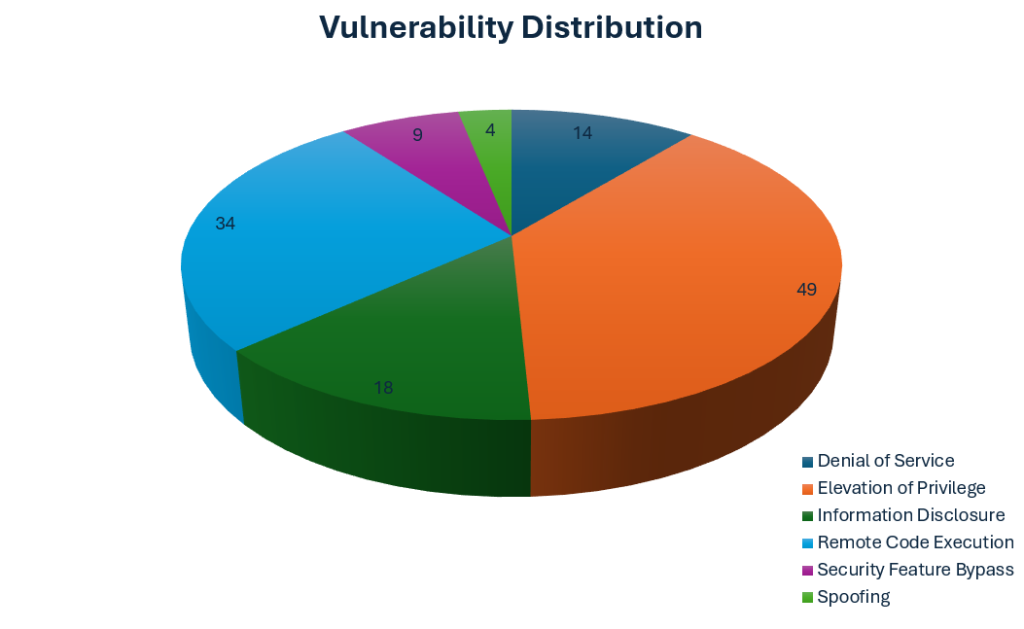
The above distribution doesn’t include Microsoft Edge (Chromium-based) non-security releases.
Zero-Day Vulnerability
CVE-2025-29824 – Windows Common Log File System Driver Elevation of Privilege Vulnerability. A use-after-free vulnerability affecting the Windows Common Log File System (CLFS) Driver, allowing a local attacker to gain SYSTEM privileges.
This zero-day vulnerability was actively exploited in the wild by the RansomEXX ransomware gang and a threat actor group known as Storm-2460, who deployed the PipeMagic malware. The vulnerability, classified as high severity with a CVSSv3 score of 7.8, impacts all supported versions of Windows OS and Windows Server, making it a significant threat requiring immediate patching to prevent potential system compromise and ransomware attacks.
Critical Vulnerabilities in Microsoft Patch Tuesday, April 2025
CVE-2025-26686 – Windows TCP/IP Remote Code Execution Vulnerability. It stems from sensitive data stored in improperly locked memory, potentially allowing an attacker to execute arbitrary code over a network. Exploitation requires a specific sequence involving a user initiating a connection and the attacker responding with a crafted DHCPv6 response.
CVE-2025-27482 and CVE-2025-27480 are critical remote code execution vulnerabilities in Windows Remote Desktop Services. An attacker could exploit these by connecting to a system with the Remote Desktop Gateway role and triggering a race condition, potentially leading to arbitrary code execution.
CVE-2025-29791 and CVE-2025-27752 – Microsoft Excel Remote Code Execution vulnerabilities.
CVE-2025-29791 – This is a Critical Remote Code Execution vulnerability in Microsoft Excel with a CVSSv3 score 7.8. An attacker could exploit this flaw by sending a specially crafted Excel document to a victim. When the victim opens this malicious file, it can trigger confusion and vulnerability. This confusion can lead to executing arbitrary code on the victim’s system, potentially granting the attacker complete control. The Preview Pane in Excel could also serve as an attack vector.
CVE-2025-27752 is a Critical Remote Code Execution vulnerability affecting Microsoft Excel with a CVSSv3 score of 7.8. An attacker could exploit this vulnerability by convincing a user to open a specially crafted Excel file. Successful exploitation could allow the attacker to execute arbitrary code on the victim’s system, potentially gaining control of the affected machine.
CVE-2025-27745, CVE-2025-27749, and CVE-2025-27748 – Microsoft Office Remote Code Execution vulnerabilities.
CVE-2025-27745—This is another Critical Remote Code Execution vulnerability, this time affecting Microsoft Office. It also has a CVSSv3 score of 7.8. This vulnerability is a use-after-free flaw. An attacker could exploit it by convincing a victim to open a specially crafted file. Triggering the use-after-free condition allows the attacker to execute arbitrary code locally with the same privileges as the current user. Like the Excel vulnerability, the Preview Pane could also be a potential attack vector.
CVE-2025-27749 – This is a severity Use After Free vulnerability affecting Microsoft Office with a CVSSv3 score of 7.8. The core issue is that the software fails to manage memory after it has been freed properly. An attacker could exploit this by enticing a user to open a specially crafted file. If successful, this could allow the attacker to execute arbitrary code on the victim’s system with the privileges of the logged-in user.
CVE-2025-27748—This is also a high-severity Use After Free vulnerability in Microsoft Office, sharing the same CVSSv3 score of 7.8. Similar to CVE-2025-27749, this vulnerability arises from improper memory management after it has been freed. An attacker could exploit this by convincing users to open a specifically crafted file. Successful exploitation could lead to executing arbitrary code on the victim’s machine within the context of the current user’s permissions.
CVE-2025-27491 – Windows Hyper-V Use After Free Vulnerability. An authenticated attacker with guest privileges could execute arbitrary code over a network by convincing a user to open a malicious site.
CVE-2025-26670 and CVE-2025-26663 are Windows Lightweight Directory Access Protocol Remote Code Execution (RCE) vulnerabilities. An unauthenticated attacker could exploit these by sending specially crafted LDAP requests to a vulnerable LDAP server, potentially leading to a use-after-free and allowing arbitrary code execution.
Microsoft Security Bulletin Summary for April 2025
In addition, this release includes security updates for the following products, features, and roles.
- Active Directory Domain Services
- ASP.NET Core
- Azure Local
- Azure Local Cluster
- Azure Portal Windows Admin Center
- Dynamics Business Central
- Microsoft AutoUpdate (MAU)
- Microsoft Edge (Chromium-based)
- Microsoft Edge for iOS
- Microsoft Office
- Microsoft Office Excel
- Microsoft Office OneNote
- Microsoft Office SharePoint
- Microsoft Office Word
- Microsoft Streaming Service
- Microsoft Virtual Hard Drive
- OpenSSH for Windows
- Outlook for Android
- Remote Desktop Client
- Remote Desktop Gateway Service
- RPC Endpoint Mapper Service
- Servicing Stack Updates
- System Center
- Visual Studio
- Visual Studio Code
- Visual Studio Tools for Applications and SQL Server Management Studio
- Windows Active Directory Certificate Services
- Windows BitLocker
- Windows Bluetooth Service
- Windows Common Log File System Driver
- Windows Cryptographic Services
- Windows Defender Application Control (WDAC)
- Windows Digital Media
- Windows DWM Core Library
- Windows File Explorer
- Windows Hello
- Windows HTTP.sys
- Windows Hyper-V
- Windows Installer
- Windows Kerberos
- Windows Kernel
- Windows Kernel Memory
- Windows Kernel-Mode Drivers
- Windows LDAP – Lightweight Directory Access Protocol
- Windows Local Security Authority (LSA)
- Windows Local Session Manager (LSM)
- Windows Mark of the Web (MOTW)
- Windows Media
- Windows Mobile Broadband
- Windows NTFS
- Windows Power Dependency Coordinator
- Windows Remote Desktop Services
- Windows Resilient File System (ReFS)
- Windows Routing and Remote Access Service (RRAS)
- Windows Secure Channel
- Windows Security Zone Mapping
- Windows Shell
- Windows Standards-Based Storage Management Service
- Windows Subsystem for Linux
- Windows TCP/IP
- Windows Telephony Service
- Windows Universal Plug and Play (UPnP) Device Host
- Windows Update Stack
- Windows upnphost.dll
- Windows USB Print Driver
- Windows Virtualization-Based Security (VBS) Enclave
- Windows Win32K – GRFX
Instantly Fix Risks with SanerNow Patch Management
SanerNow patch management is a continuous, automated, and integrated software that instantly fixes risks exploited in the wild. The software supports major operating systems like Windows, Linux, and macOS, as well as 550+ third-party applications.
It also allows you to set up a safe testing area to test patches before deploying them in a primary production environment. SanerNow patch management additionally supports a patch rollback feature in case of patch failure or a system malfunction.
Experience the fastest and most accurate patching software here.


