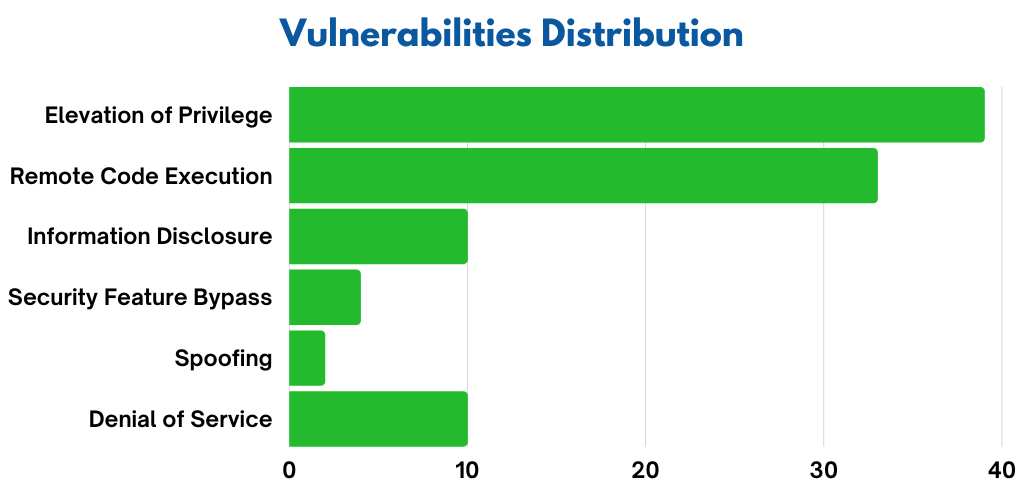
Microsoft has released January 2023 Patch Tuesday security updates, addressing 98 vulnerabilities. Also, 11 are classified as critical as they allow the most severe types of vulnerabilities like privilege elevation, security feature bypass, or remote code execution, and 87 are classified as important. In addition, the products covered in the January security update include Microsoft Office SharePoint, Windows Advanced Local Procedure Call (ALPC), Microsoft Cryptographic Services, Windows Layer 2 Tunneling Protocol (L2TP), Windows Secure Socket Tunneling Protocol, etc.
Microsoft January Patch Tuesday 2023 fixes one zero-day vulnerability that is known to be actively exploited (CVE-2023-21674). However, it is essential to have a vulnerability management software.
Zero-Days Vulnerabilities
CVE-2023-21674 | Windows Advanced Local Procedure Call (ALPC) Elevation of Privilege Vulnerability
However, this vulnerability is classified as critical and has a CVSSv3.1 score of 8.8 out of 10. Whereas, this vulnerability is a sandbox escape vulnerability that can lead to the elevation of privileges. Moreover, successful exploitation of this vulnerability can lead an attacker to gain SYSTEM privileges.
Critical Vulnerabilities of Microsoft January Patch Tuesday 2023
CVE-2023-21743 | Microsoft SharePoint Server Security Feature Bypass Vulnerability
This vulnerability has a CVSSv3.1 score of 5.3 out of 10. However, an unauthenticated, remote attacker can exploit the flaw to bypass the protection in SharePoint. Whereas, successful exploitation can lead an attacker to launch and establish an anonymous connection to the targeted SharePoint server.
CVE-2023-21551, CVE-2023-21561, CVE-2023-21730 | Microsoft Cryptographic Services Elevation of Privilege Vulnerability
In fact, these vulnerabilities have a CVSSv3.1 score range from 7.8 to 8.8 out of 10. However, the locally authenticated attacker who sends specially crafted data to the local CSRSS service is required. Whereas, successful exploitation can lead attackers to elevate their privileges from an AppContainer environment to SYSTEM access.
CVE-2023-21556, CVE-2023-21555, CVE-2023-21543, CVE-2023-21546, CVE-2023-21679 | Windows Layer 2 Tunneling Protocol (L2TP) Remote Code Execution Vulnerability
In fact, these vulnerabilities have a CVSSv3.1 score of 8.1 out of 10. However, a remote attacker can send a specially crafted connection request to a Remote Access Server and exploit this vulnerability. Whereas, it can lead an attacker to remote code execution on the Remote Access Server. Moreover, an attacker sends a specially crafted malicious SSTP packet to an SSTP server for exploitation on the server side by remote code execution. To prevent this from occurring, a patch management software will come in handy.
Microsoft security bulletin summary for January 2023
- .NET Core
- 3D Builder
- Azure Service Fabric Container
- Microsoft Bluetooth Driver
- Microsoft Exchange Server
- Microsoft Graphics Component
- Microsoft Local Security Authority Server (lsasrv)
- Microsoft Message Queuing
- Microsoft Office
- Microsoft Office SharePoint
- Microsoft Office Visio
- Microsoft WDAC OLE DB provider for SQL
- Visual Studio Code
- Windows ALPC
- Windows Ancillary Function Driver for WinSock
- Windows Authentication Methods
- Windows Backup Engine
- Windows Bind Filter Driver
- Windows BitLocker
- Windows Boot Manager
- Windows Credential Manager
- Windows Cryptographic Services
- Windows DWM Core Library
- Windows Error Reporting
- Windows Event Tracing
- Windows IKE Extension
- Windows Installer
- Windows Internet Key Exchange (IKE) Protocol
- Windows iSCSI
- Windows Kernel
- Windows Layer 2 Tunneling Protocol
- Windows LDAP – Lightweight Directory Access Protocol
- Windows Local Security Authority (LSA)
- Windows Local Session Manager (LSM)
- Windows Malicious Software Removal Tool
- Windows Management Instrumentation
- Windows MSCryptDImportKey
- Windows NTLM
- Windows ODBC Driver
- Windows Overlay Filter
Microsoft January Patch Tuesday 2023 affected products:
Product: Microsoft Windows
CVEs/Advisory: CVE-2023-21524, CVE-2023-21525, CVE-2023-21527, CVE-2023-21532, CVE-2023-21535, CVE-2023-21536, CVE-2023-21537, CVE-2023-21539, CVE-2023-21540, CVE-2023-21541, CVE-2023-21542, CVE-2023-21543, CVE-2023-21546, CVE-2023-21547, CVE-2023-21548, CVE-2023-21549, CVE-2023-21550, CVE-2023-21551, CVE-2023-21552, CVE-2023-21555, CVE-2023-21556, CVE-2023-21557, CVE-2023-21558, CVE-2023-21559, CVE-2023-21560, CVE-2023-21561, CVE-2023-21563, CVE-2023-21674, CVE-2023-21675, CVE-2023-21676, CVE-2023-21677, CVE-2023-21678, CVE-2023-21679, CVE-2023-21680, CVE-2023-21681, CVE-2023-21682, CVE-2023-21683, CVE-2023-21724, CVE-2023-21726, CVE-2023-21728, CVE-2023-21730, CVE-2023-21732, CVE-2023-21733, CVE-2023-21739, CVE-2023-21746, CVE-2023-21747, CVE-2023-21748, CVE-2023-21749, CVE-2023-21750, CVE-2023-21752, CVE-2023-21753, CVE-2023-21754, CVE-2023-21755, CVE-2023-21757, CVE-2023-21758, CVE-2023-21759, CVE-2023-21760, CVE-2023-21765, CVE-2023-21766, CVE-2023-21767, CVE-2023-21768, CVE-2023-21771, CVE-2023-21772, CVE-2023-21773, CVE-2023-21774, CVE-2023-21776
Impact: Denial of Service, Elevation of Privilege, Impact, Information Disclosure, Remote Code Execution, and Security Feature Bypass.
KB’s: 5022282, 5022286, 5022287, 5022289, 5022291, 5022297, 5022303, 5022343, 5022346, 5022348, 5022352
Product: Microsoft Office
CVEs/Advisory: CVE-2023-21734, CVE-2023-21735, CVE-2023-21736, CVE-2023-21737, CVE-2023-21738, CVE-2023-21741, CVE-2023-21742, CVE-2023-21743, CVE-2023-21744
Impact: Information Disclosure, Remote Code Execution, Security Feature Bypass
KB’s: 5002329, 5002331, 5002332, 5002335, 5002336, 5002337, 5002338
Product: Microsoft SharePoint
CVEs/Advisory: CVE-2023-21743
Impact: Security Feature Bypass
KB’s: 5002329
Finally, SanerNow VM and SanerNow PM can detect and automatically fix these vulnerabilities by applying security updates. However, use SanerNow and keep your systems updated and secure.

